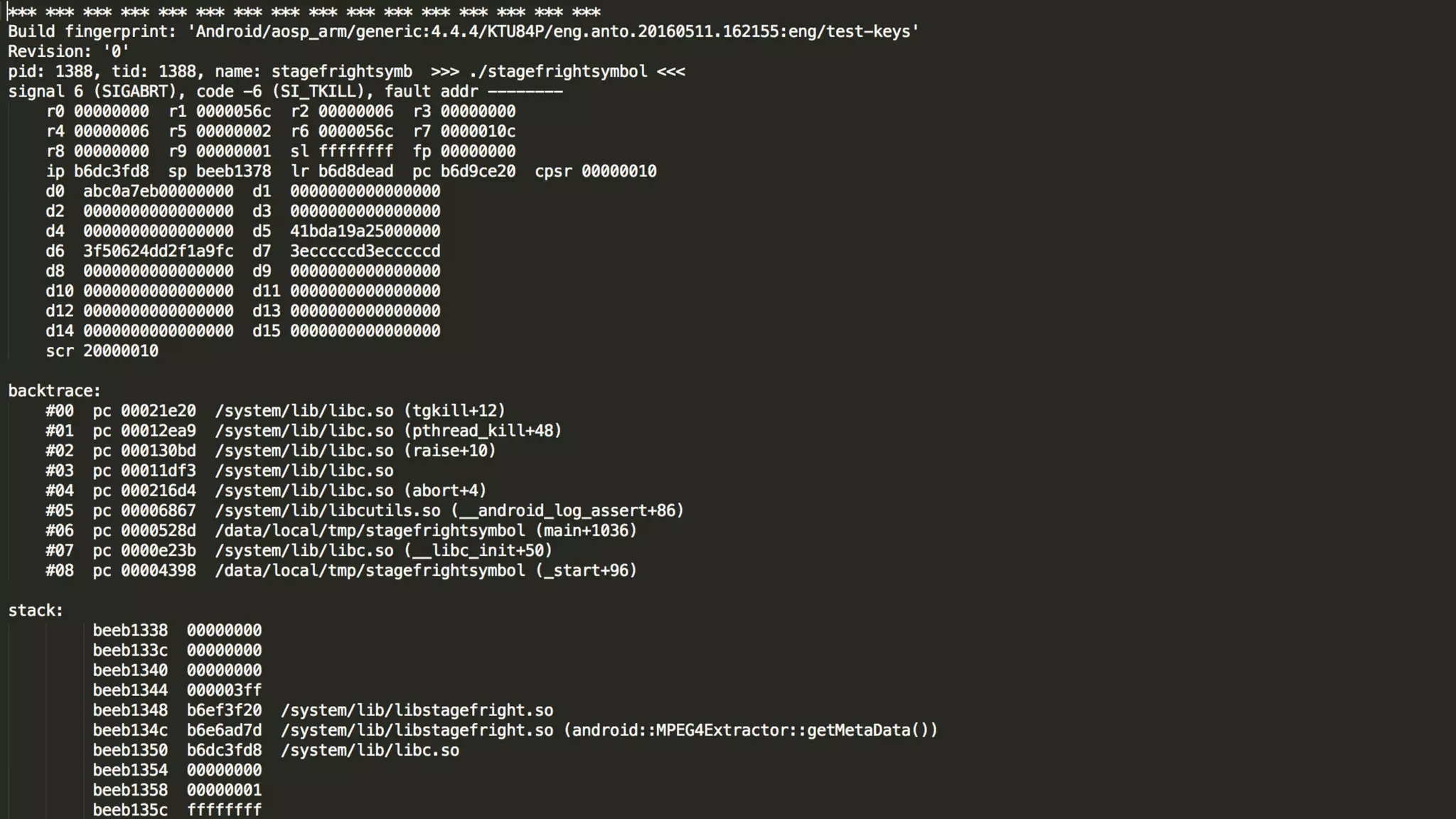
Droid-FF is an Android fuzzing framework that aims to automate the fuzzing process on mobile devices like Android. It generates test input data using techniques like bit flipping, integrates with other fuzzers like Peach and Pyzuff, implements custom crash logging and triaging. It can identify exploitable crashes using a GDB plugin, map crashes to source code locations, and has been used to find many crashes, helping to improve Android security. The tool is open source and customizable to make fuzzing easier and more accessible.