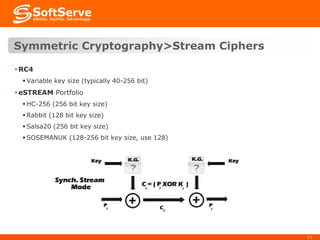
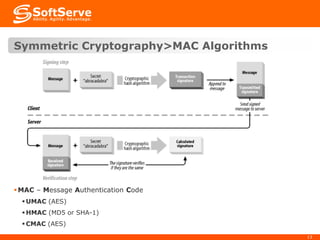
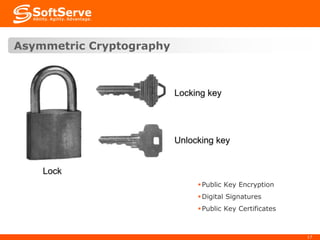
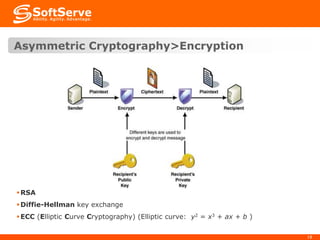
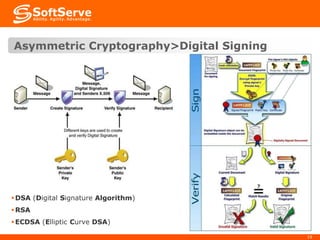
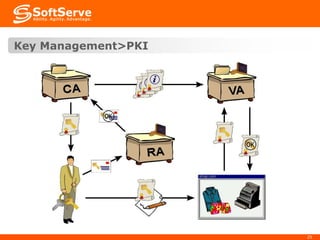
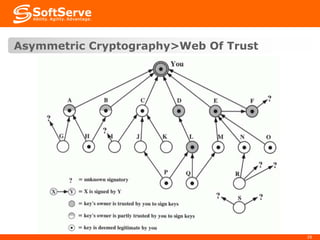
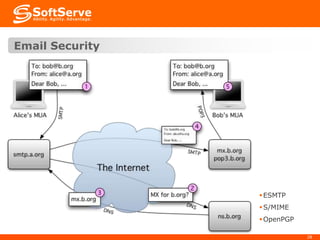
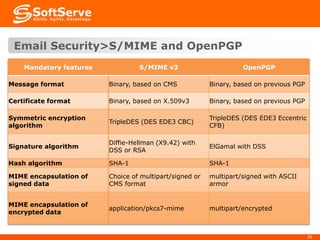
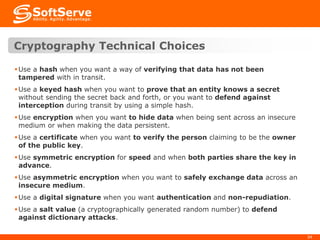
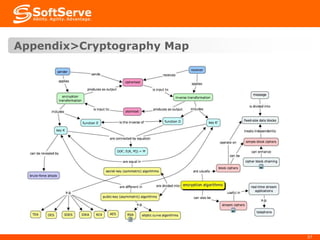
This document provides an overview of cryptography basics, including symmetric and asymmetric cryptography. Symmetric cryptography uses the same key for encryption and decryption, with examples being AES, DES, and stream ciphers. Asymmetric cryptography uses public/private key pairs, with common algorithms being RSA for encryption and DSA for digital signatures. The document also discusses key management, certificates, email security protocols like S/MIME and PGP, network security protocols like TLS/SSL, and technical considerations for cryptographic choices.





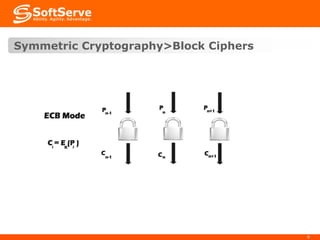
![Symmetric Cryptography>Block Ciphers
DES (Data Encryption Standard)
56 bit key size
Secure? NO!
3DES (Triple DES)
56-bit key size. 1 or 2 or 3 keys used. Max: 168 bits
Secure? ALMOST (using 3 different keys)
AES (Advanced Encryption Standard) or Rijndael [rɛindal]
128/192/256 bit key size
Secure? 128 bit – for dynamic data, 192 bit – ALMOST, 256 – YES (Currently)
6 times faster than 3DES !!!
RC2
Variable key size
Secure? Vulnerable to related key attack using 2^34 chosen plaintexts
10](https://image.slidesharecdn.com/2-140307141942-phpapp02/85/Security-Training-2-Cryptography-Basics-10-320.jpg)