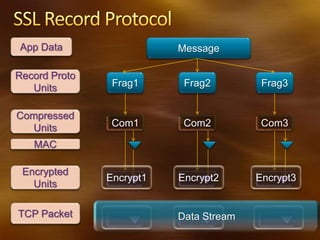
The TLS/SSL protocol provides privacy and integrity of communications over TCP by encrypting message content and verifying message integrity. It operates in layers, with the TLS record protocol handling fragmentation, compression, encryption, and MAC verification of messages, and the TLS handshake protocol allowing client and server to authenticate and establish encryption parameters before transmitting application data. Openssl is an open source implementation of the TLS/SSL protocols and cryptographic functions used for tasks like generating certificates.


















![Selected Cipher Suite
Selected Comp Algo
Selected Version
S X509 Certificate
Cryptographic Info
SSL Client SSL Server
Session ID
Random Data
Cipher Suite List
Compression Algo List
Version List
CL X509 Certificate
Premaster secret
ClientHello
Certificate
ServerKeyExchange
CertificateRequest
ServerHello
ServerHelloDone
Certificate
ClientKeyExchange
CertificateVerify
Finished
[ChangeCipherSpec]
Application Data
Finished
[ChangeCipherSpec]](https://image.slidesharecdn.com/securesocketlayer-200430235444/85/Secure-socket-layer-21-320.jpg)

![ServerHello
[ChangeCipherSpec]
Finished
Application Data
SSL Client SSL Server
ClientHello
[ChangeCipherSpec]
Finished
Application Data](https://image.slidesharecdn.com/securesocketlayer-200430235444/85/Secure-socket-layer-23-320.jpg)