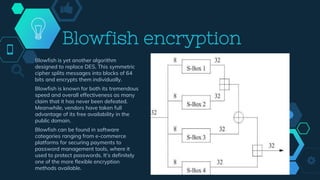
Encryption is a process that converts plain text into ciphertext through the use of cryptographic algorithms and encryption keys. There are two main types of encryption: symmetric encryption which uses the same key for encryption and decryption, and asymmetric encryption which uses a public key for encryption and a private key for decryption. Common symmetric encryption algorithms discussed include DES, Triple DES, AES, Blowfish and Twofish. Asymmetric algorithms include RSA. Other algorithms mentioned are IDEA, MD5, and FPE. The document also discusses how encryption keys are used and changed in Magento.
















![Step 1: Make the File Writable
◇ To change the encryption key, make sure that the following file is
writable: [your store]/app/etc/env.php
Step 2: Change the Encryption Key
◇ On the Admin sidebar, go to System > Other Settings > Manage
Encryption Key.
◇ Do one of the following:
■ To generate a new key, set Auto-generate Key to Yes.
■ To use a different key, set Auto-generate Key to No. Then in the
New Key field, enter or paste the key that you want to use.
◇ Click Change Encryption Key.
◇ Keep a record of the new key in a secure location.
◇ It will be required to decrypt the data, if any problems occur with your
files.](https://image.slidesharecdn.com/encryptiontechniquesmodify-201027101422/85/Encryption-techniques-18-320.jpg)
