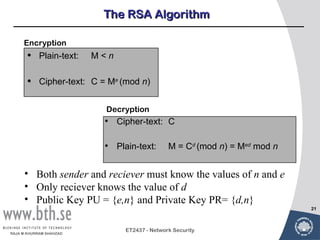
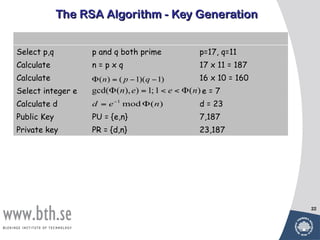
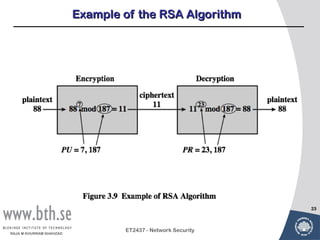
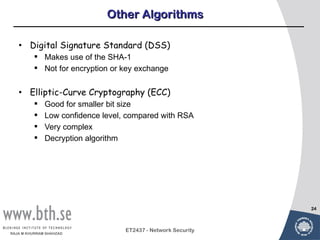
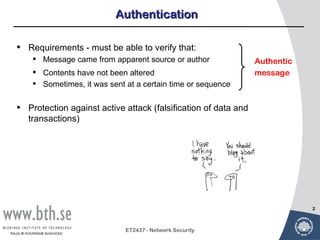
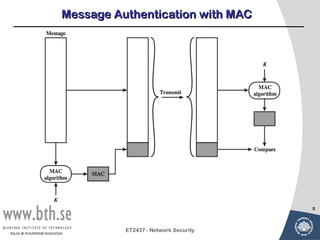
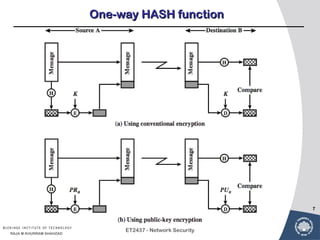
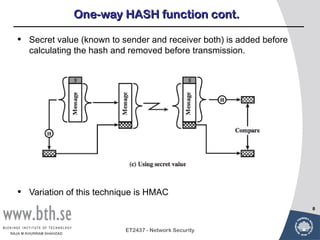
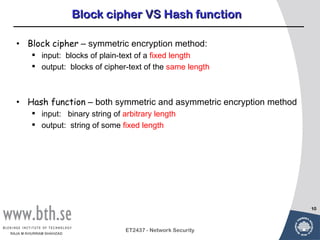
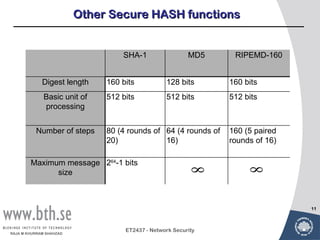
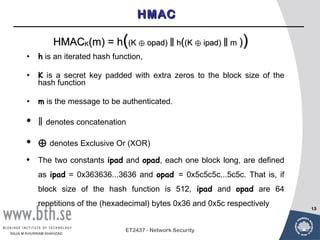
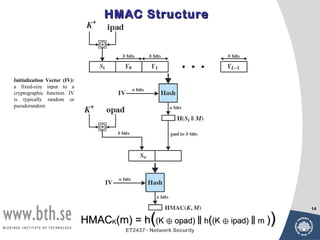
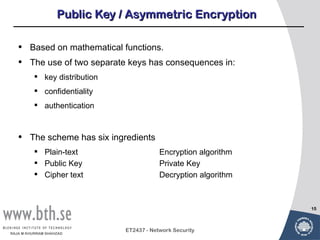
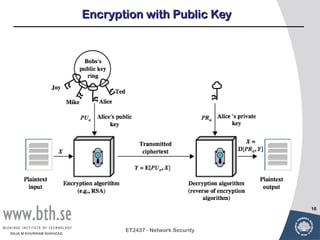
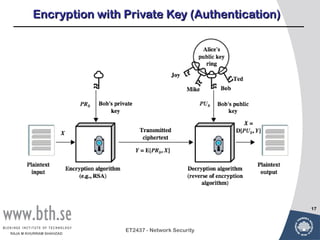
Public-key cryptography uses message authentication codes (MACs) and digital signatures to verify the authenticity and integrity of messages. MACs are calculated using a secret key shared between the sender and receiver. Digital signatures are generated using the sender's private key and can be verified by the receiver using the sender's public key. Common MAC algorithms include HMAC, which uses a cryptographic hash function combined with a secret key. Asymmetric encryption algorithms like RSA enable confidential communication by encrypting messages with the public key while only the holder of the private key can decrypt.







![Requirements for Asymmetric Encryption
1. Computationally easy for a party B to generate a pair (PUblic key
PUb, PRivate key PRb)
2. Easy for sender to generate cipher-text: C = E(Pub, M)
3. Easy for the receiver to decrypt cipher-text using private key:
M = D(PRb, C) = D[PRb, E(PUb, M)]
5. Computationally in-feasible to determine Private Key (PRb) knowing
Public Key (PUb)
6. Computationally infeasible to recover message M, knowing PUb and
cipher-text C
7. Either of the two related keys can be used for encryption, with the
other used for decryption:
19
M = D[PUb, E(PRb,M) = D[PRb, E(PUb,M)]
ET2437 - Network Security
RAJA M KHURRAM SHAHZAD](https://image.slidesharecdn.com/lecture3bpublickeyencryption0-3-120612174205-phpapp01/85/Lecture-3b-public-key_encryption-19-320.jpg)