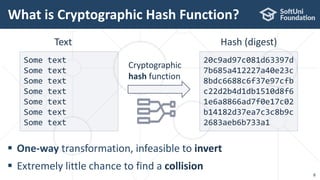
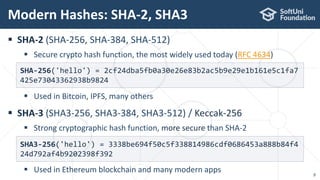
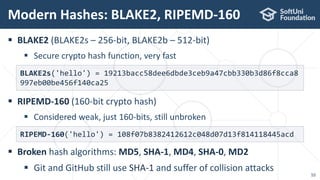
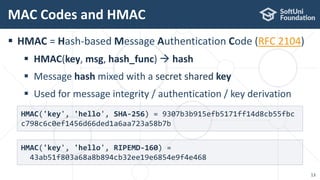
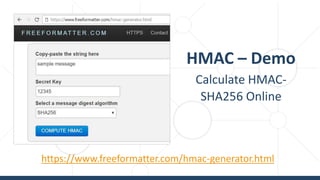
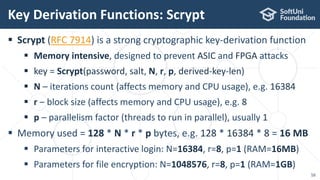
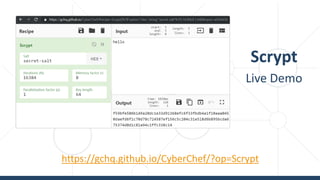
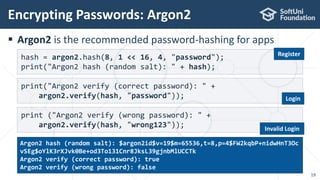
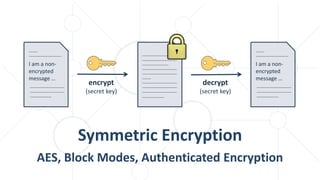
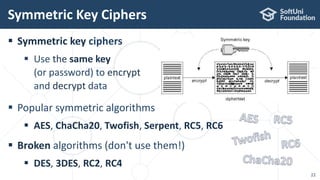
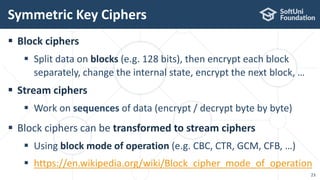
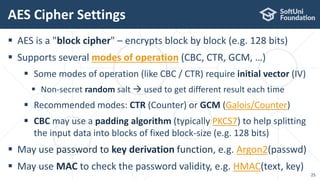
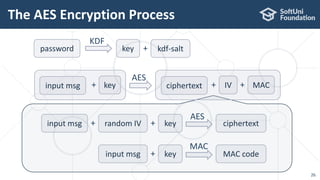
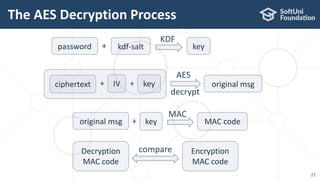
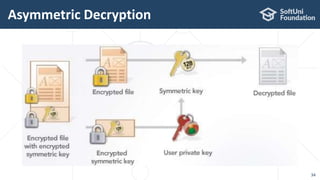
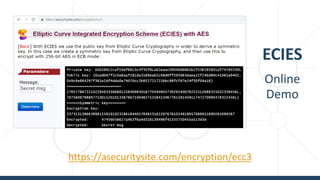
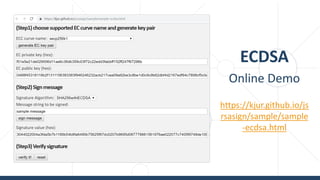
The document provides an introductory overview of cryptography, explaining key topics such as hashing, encryption, digital signatures, and key derivation functions. It covers various cryptographic algorithms, including symmetric ciphers like AES and hash functions like SHA-2 and Argon2, emphasizing their importance for secure data storage and transmission. The speaker, Dr. Svetlin Nakov, is a seasoned expert in the field, highlighting practical applications within the domain of cryptography.