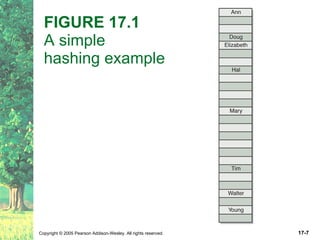
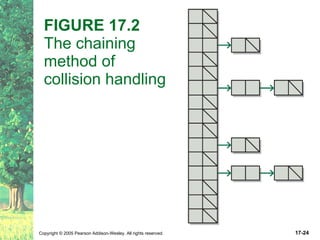
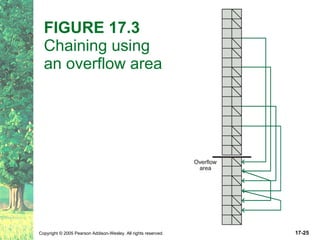
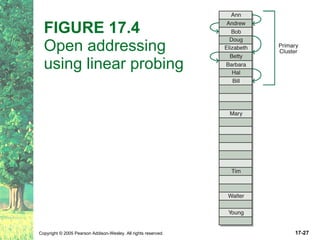
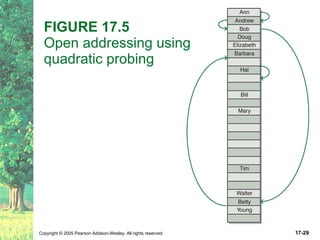
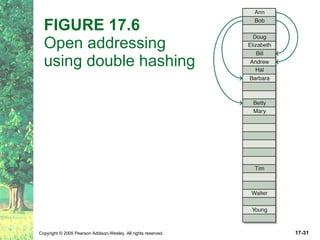
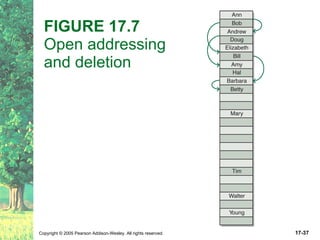
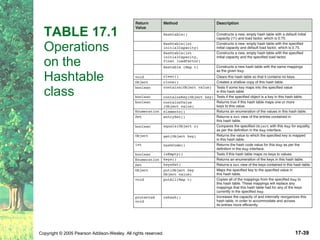
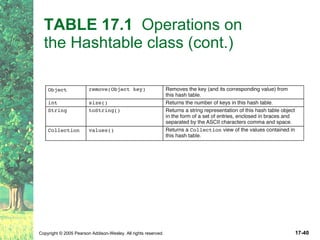
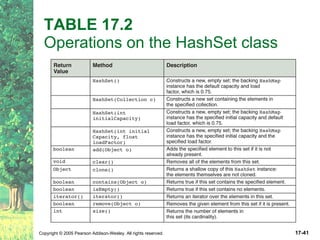
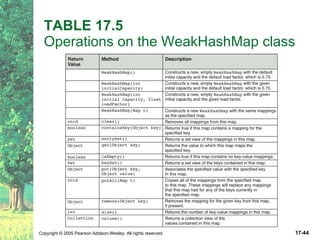
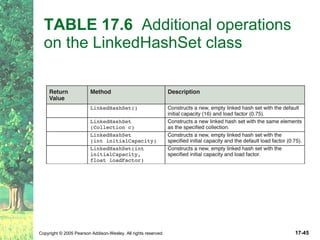
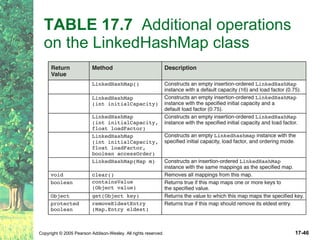
The document discusses hashing and hash tables. It defines hashing as a technique where the location of an element in a collection is determined by a hashing function of the element's value. Collisions can occur if multiple elements map to the same location. Common techniques for resolving collisions include chaining and open addressing. The Java Collections API provides several implementations of hash tables like HashMap and HashSet.