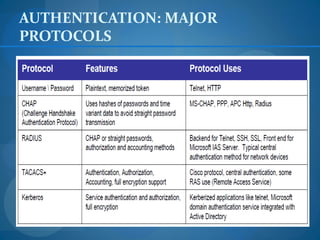
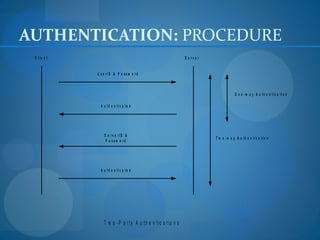
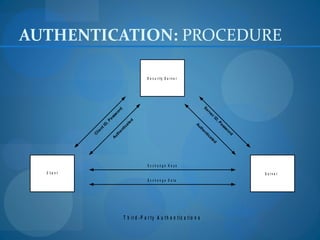
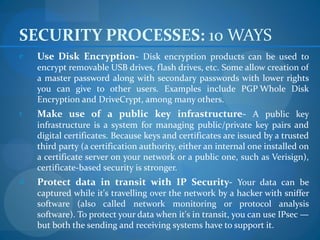
1. Formulate a testing plan with the client to identify systems to evaluate and the scope of testing allowed.
2. Remotely or locally access the target systems to find vulnerabilities by simulating common attacks.
3. Report any found vulnerabilities to the client along with recommendations on how to remedy security issues.