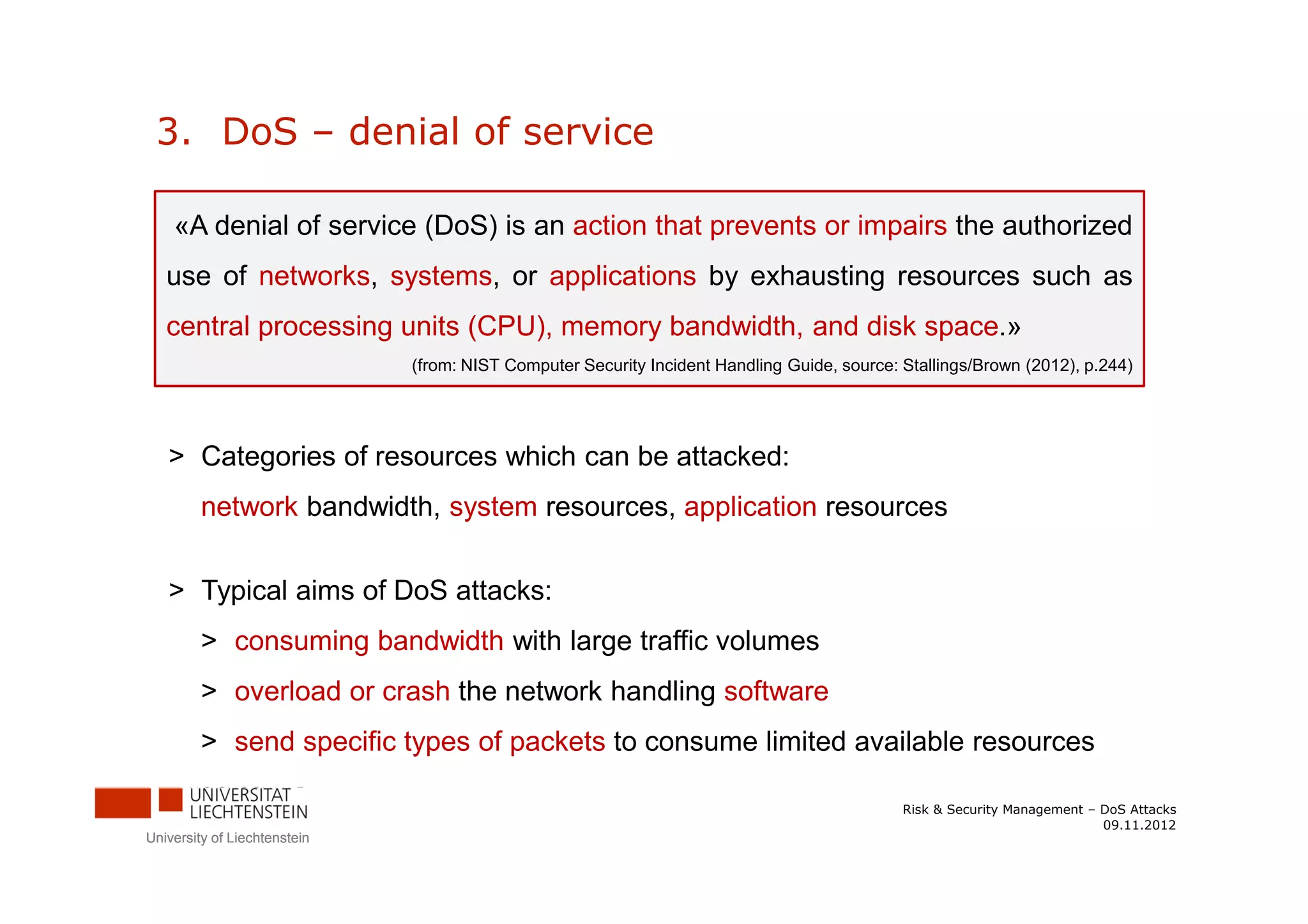
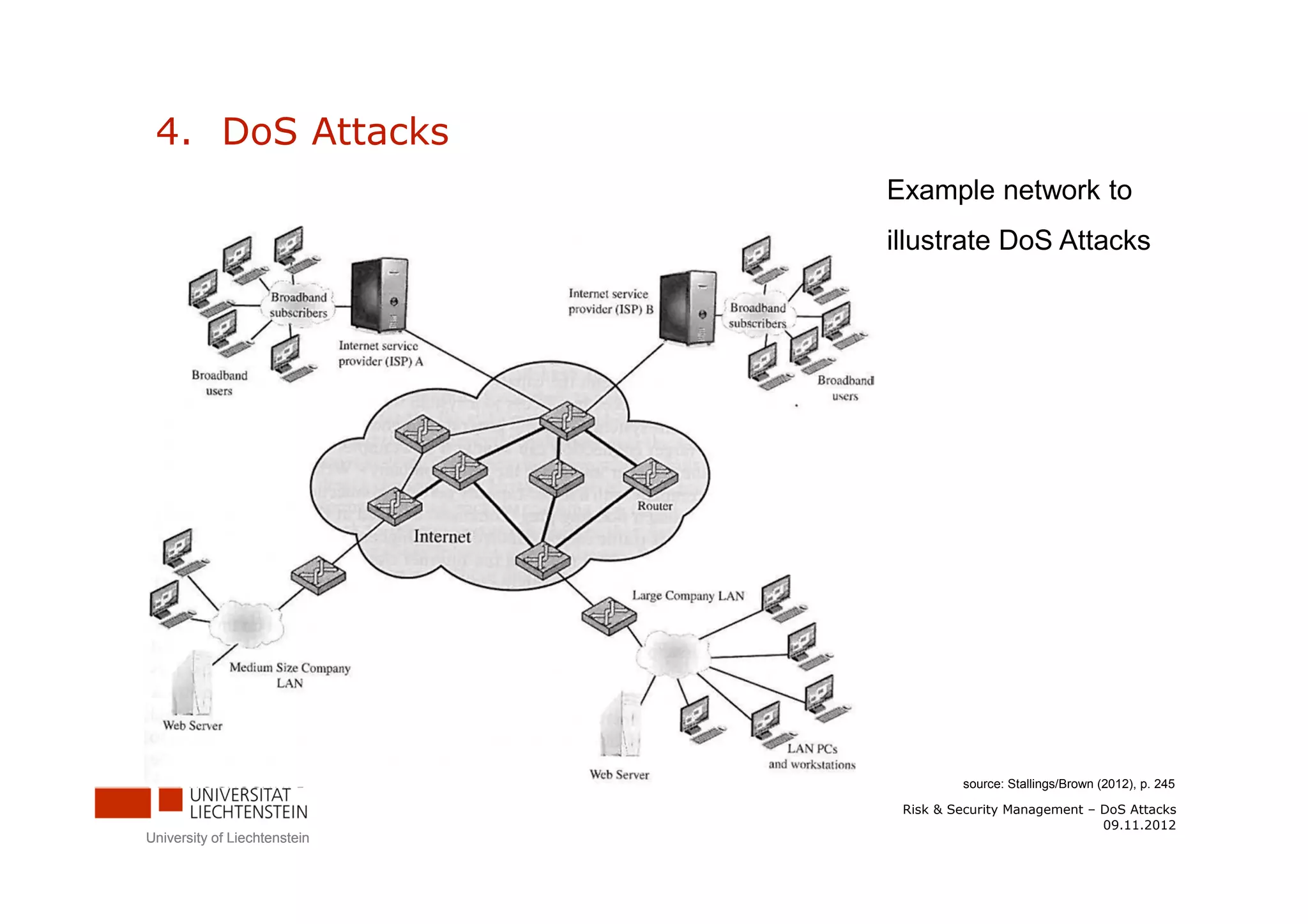
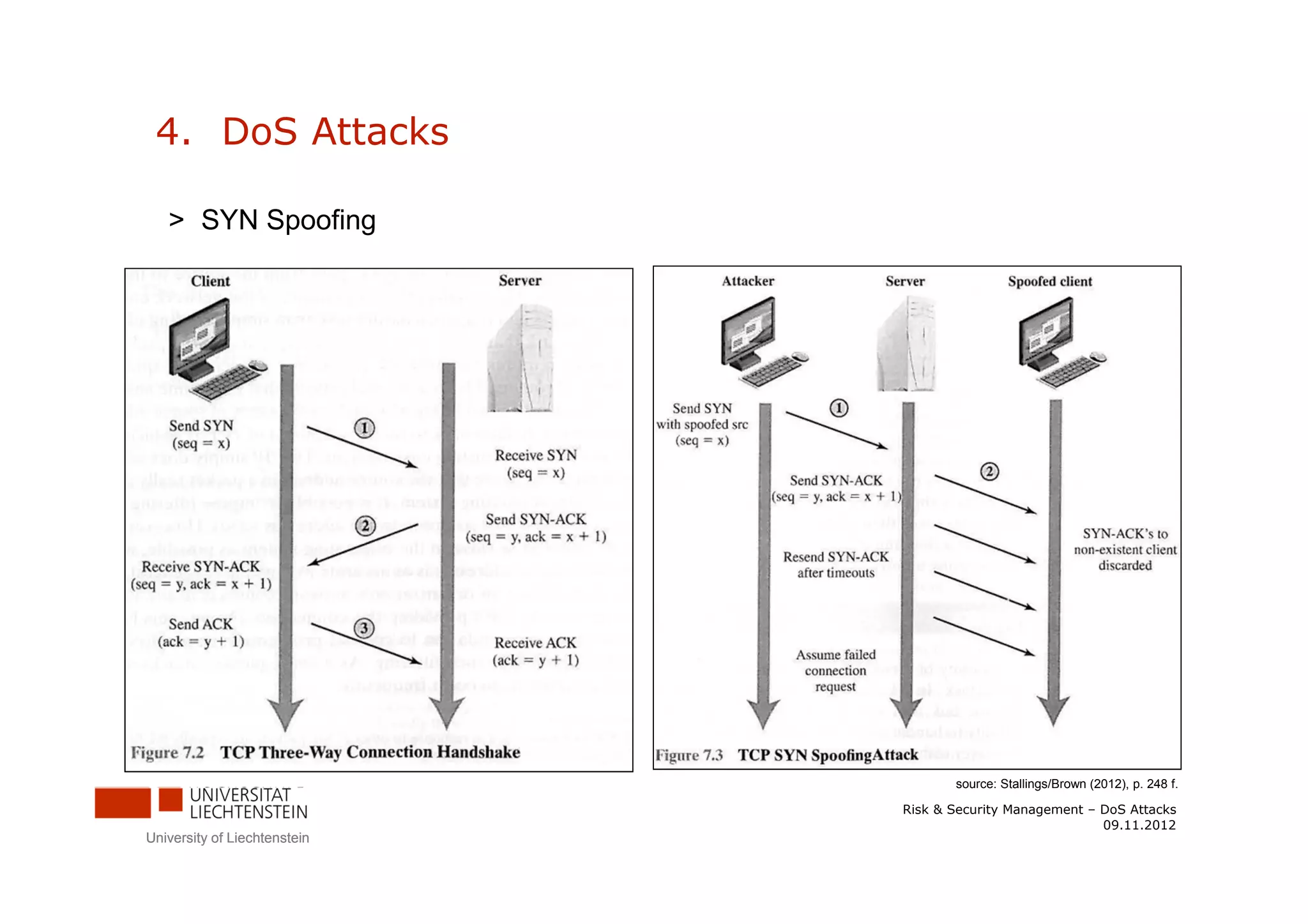
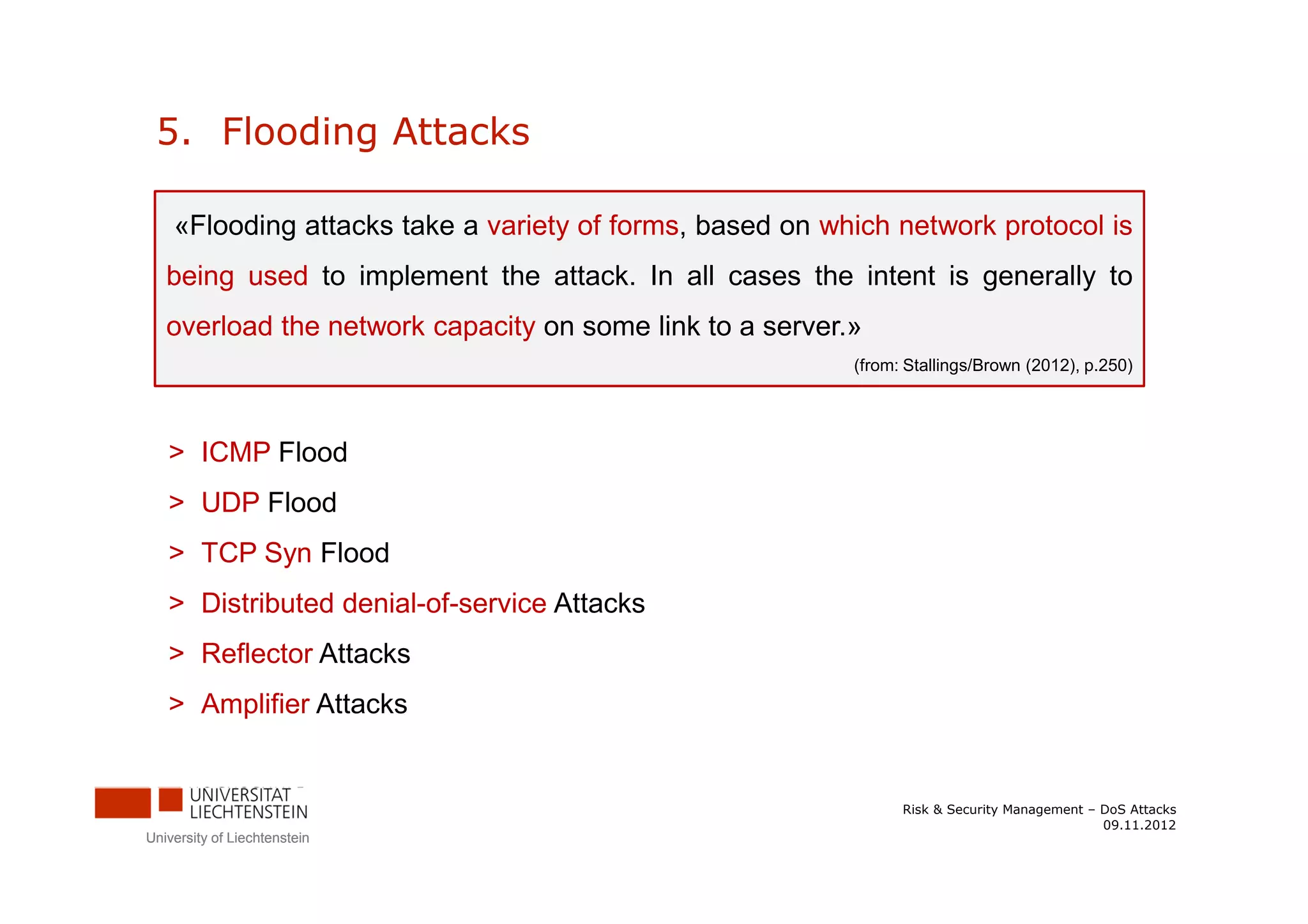
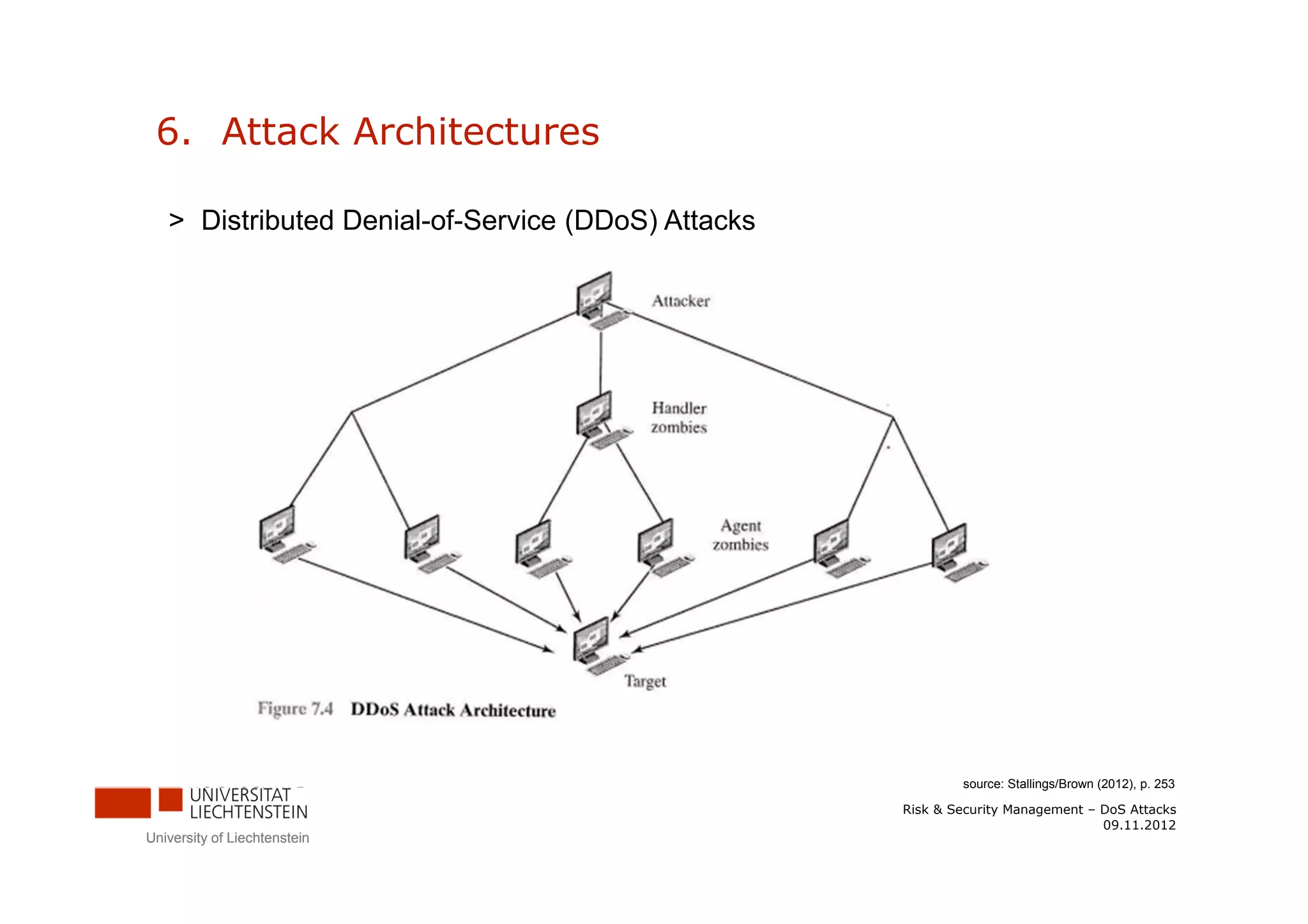
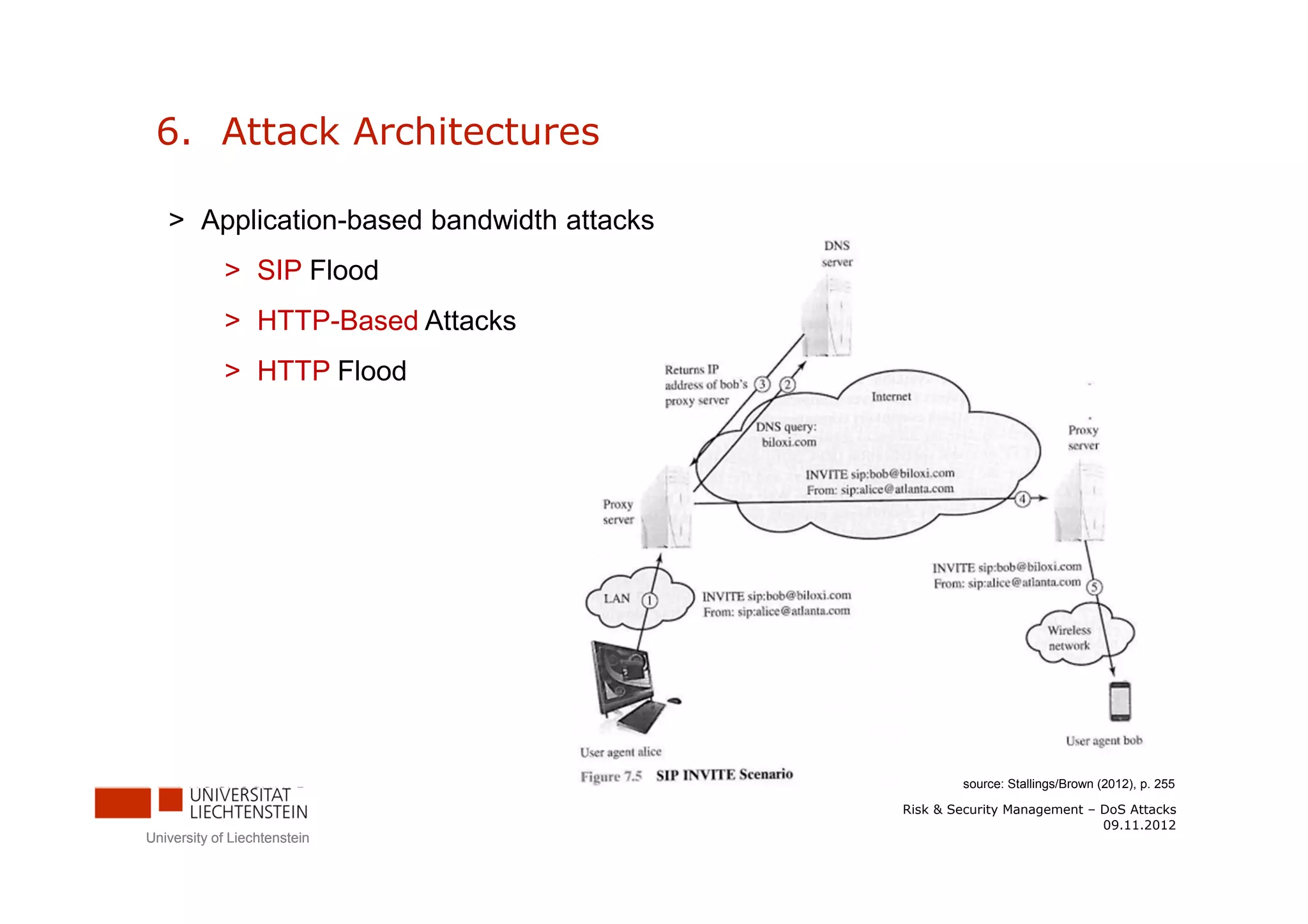
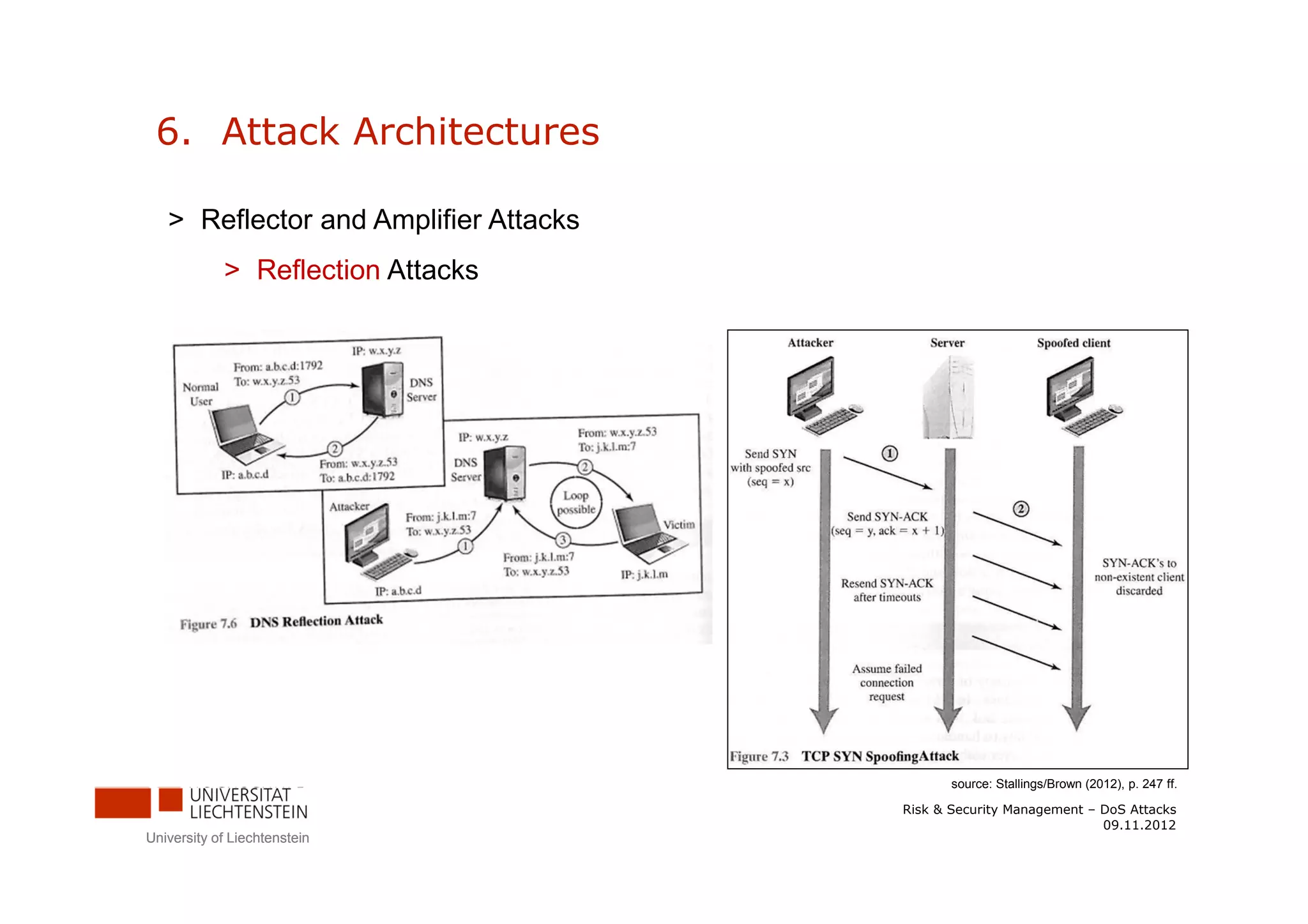
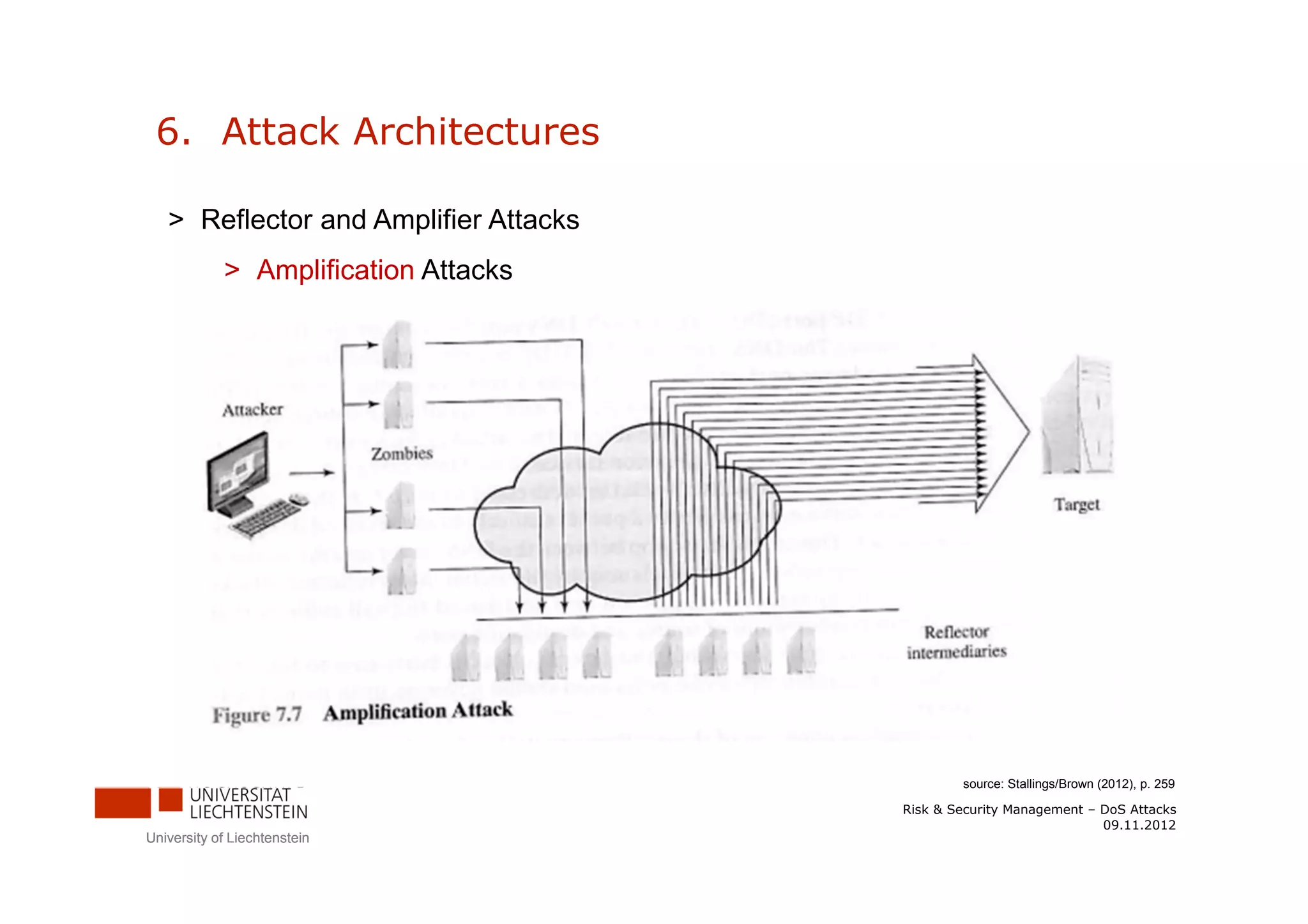
The document discusses denial-of-service (DoS) attacks. It provides facts about the increasing scale of DDoS attacks over the past decade. It then describes different types of DoS attacks like SYN spoofing and flooding attacks using various protocols. The document also outlines attack architectures including distributed denial-of-service attacks. It discusses defenses against DoS attacks that focus on prevention, detection, and traceback. Finally, it proposes guidelines for responding to a DoS attack by identifying the attack type, defending against it, analyzing network traffic, documenting actions, and developing backup plans to restore services.