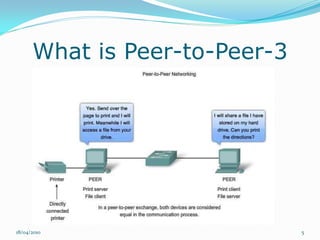
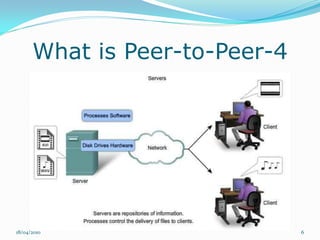
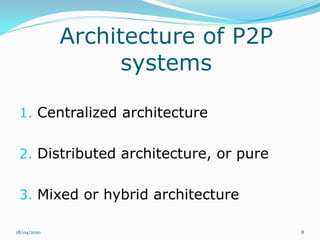
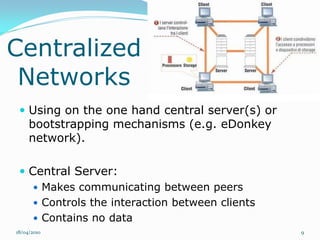
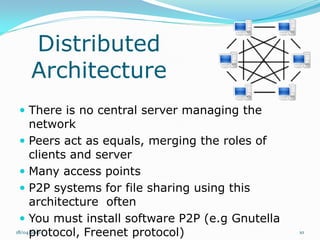
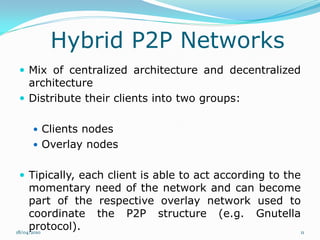
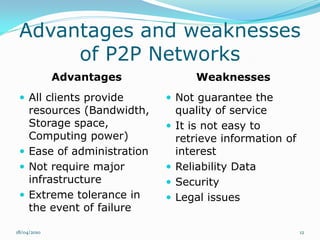
Il documento esplora il concetto di peer-to-peer (P2P) come architettura di rete distribuita, analizzando vantaggi, debolezze, questioni legali e di sicurezza. Si discute dell'evoluzione storica del P2P, diverse architetture di rete e le applicazioni in ambito di condivisione file e potenza computazionale. Infine, si considerano gli sviluppi futuri, evidenziando problemi tecnici e normativi che ne limitano l'adozione.