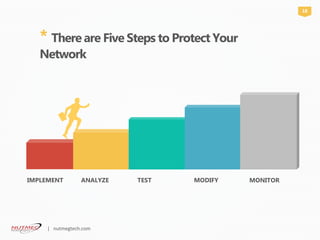
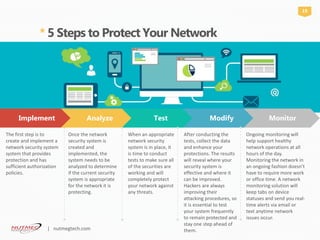
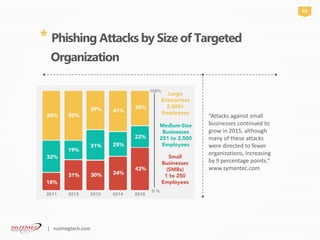
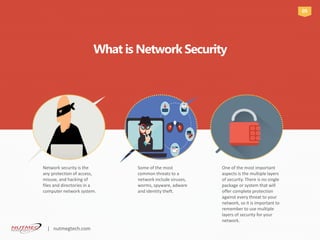
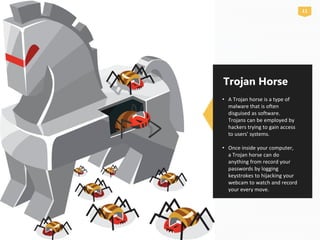
Network security is crucial for protecting computer networks from various cyber threats, especially for small businesses which are often targeted due to their lack of resources. Key threats include malware, phishing, and unsecured systems, highlighting the need for multi-layered security protocols. Implementing a structured approach involving the creation, testing, and ongoing monitoring of security systems is essential for safeguarding sensitive data and maintaining operational integrity.





![*Malware
[mal-wair]
noun, Computers.
1. “malicious” software intended to damage a
computer, mobile device, computer
system, or computer network, or
to take partial control over its operation](https://image.slidesharecdn.com/whatisnetworksecurity-170207194637/85/What-is-Network-Security-8-320.jpg)


![* Malicious Spyware
[spahy-wair]
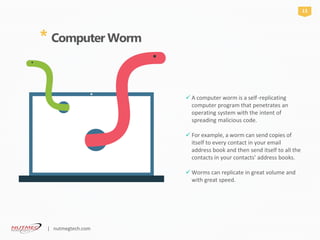
Malicious spyware is used to describe the•
Trojan application that was created by cyber
criminals to spy on their victims.
An example would be key logger software that•
records a victim’s every keystroke on his or her
keyboard.
Spyware is used to conduct espionage.•
12
| nutmegtech.com](https://image.slidesharecdn.com/whatisnetworksecurity-170207194637/85/What-is-Network-Security-12-320.jpg)

![Rootkit
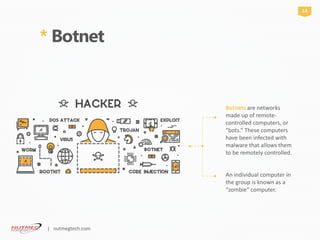
A set of software tools that
enable an unauthorized user
to gain control of a computer
system without being
detected.
* A rootkit could be installed on
your computer by a
cybercriminal exploiting a
vulnerability or security hole in
a legitimate application on your
PC and may contain spyware
that monitors and records
keystrokes.
*
17
[ro͞otˌkit]
Noun, computing.
a set of software tools that enable an unauthorized user to gain control of a computer system
without being detected.
| nutmegtech.com](https://image.slidesharecdn.com/whatisnetworksecurity-170207194637/85/What-is-Network-Security-17-320.jpg)