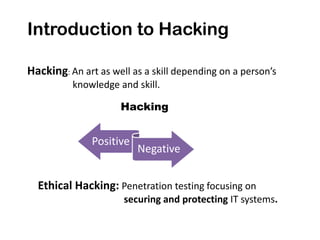
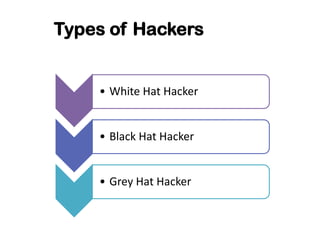
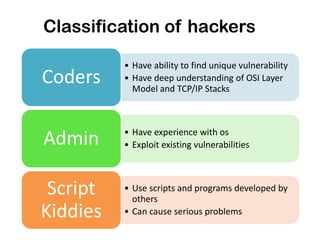
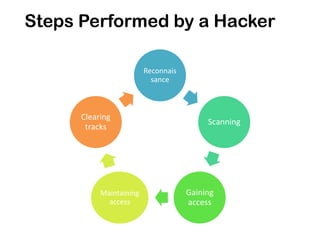
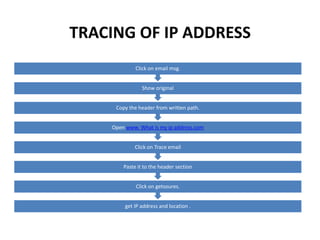
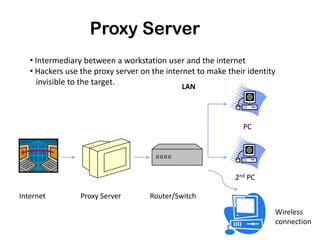
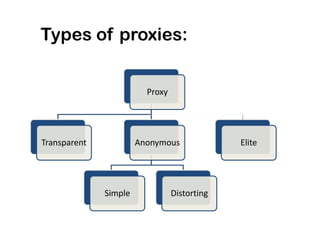
Ethical hacking involves performing penetration testing to locate security weaknesses and implement countermeasures in order to secure IT systems. There are three main types of hackers: white hat hackers who perform ethical hacking, black hat hackers who hack illegally for malicious purposes, and grey hat hackers who sometimes act legally and sometimes not. The steps a hacker may perform include reconnaissance, scanning, gaining access, maintaining access, and covering their tracks. IP addresses are classified into ranges and tracing IP addresses can help identify locations. Security measures like confidentiality, integrity, availability, and proper access controls can help protect against hacking threats.