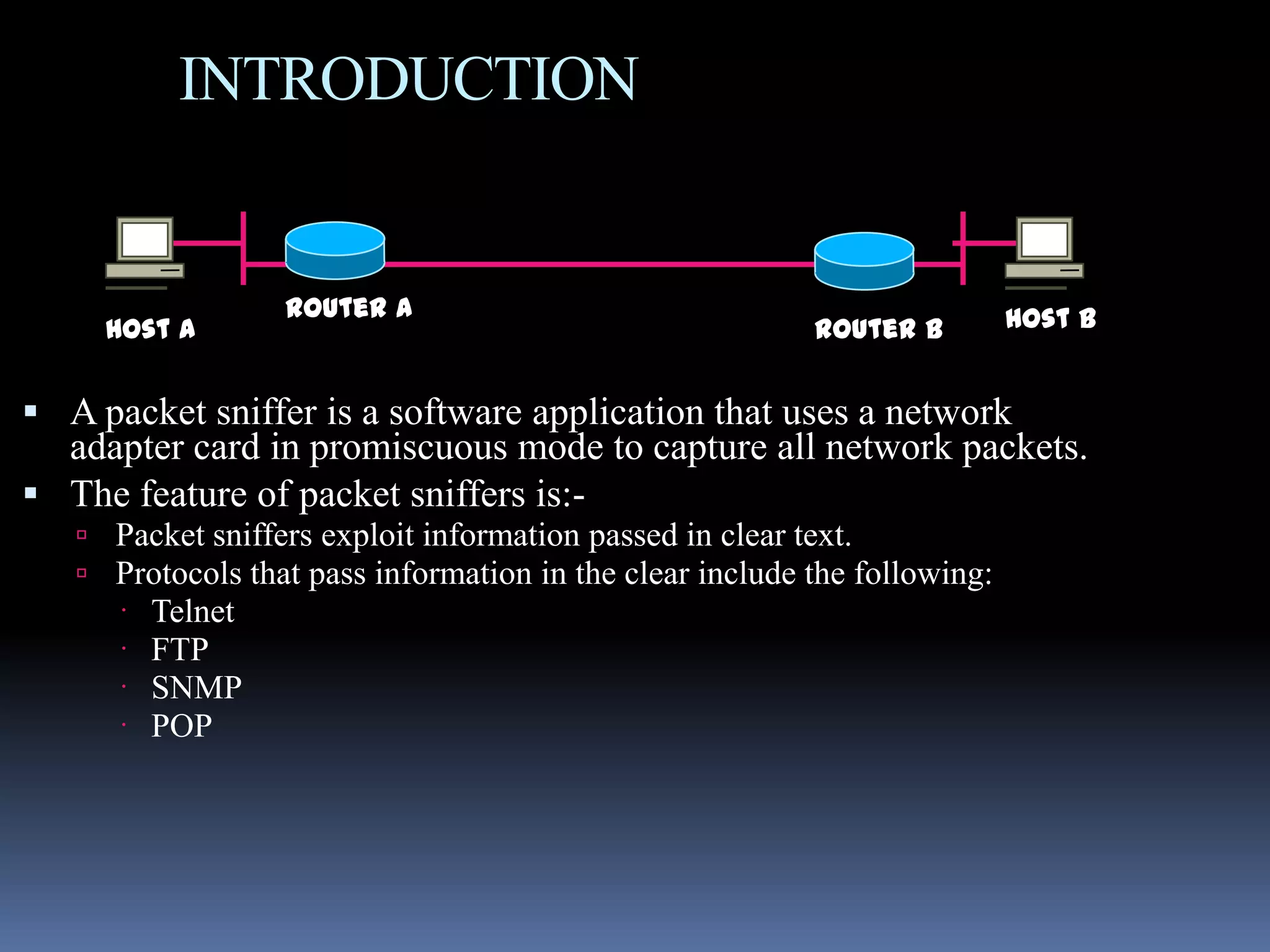
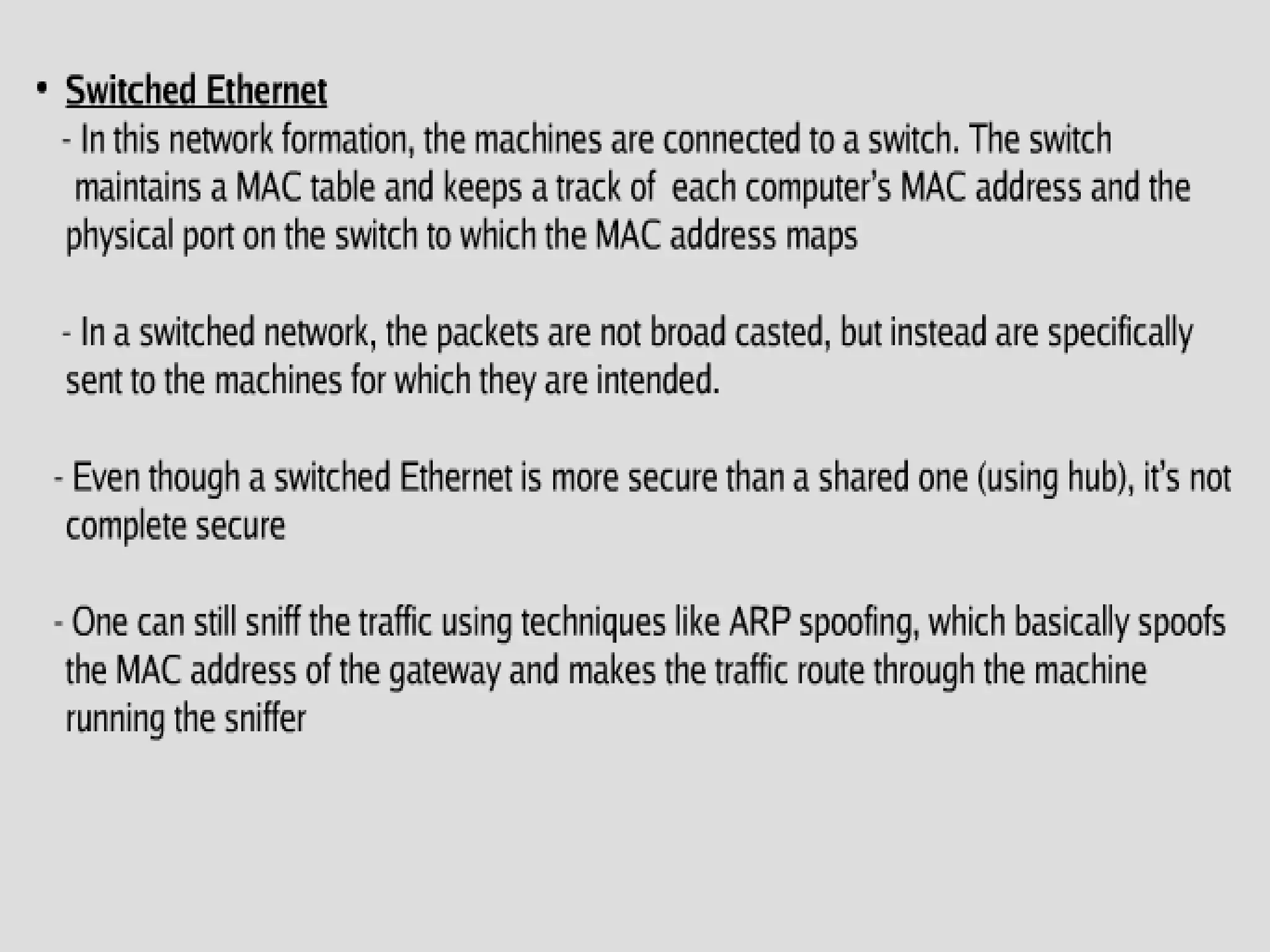
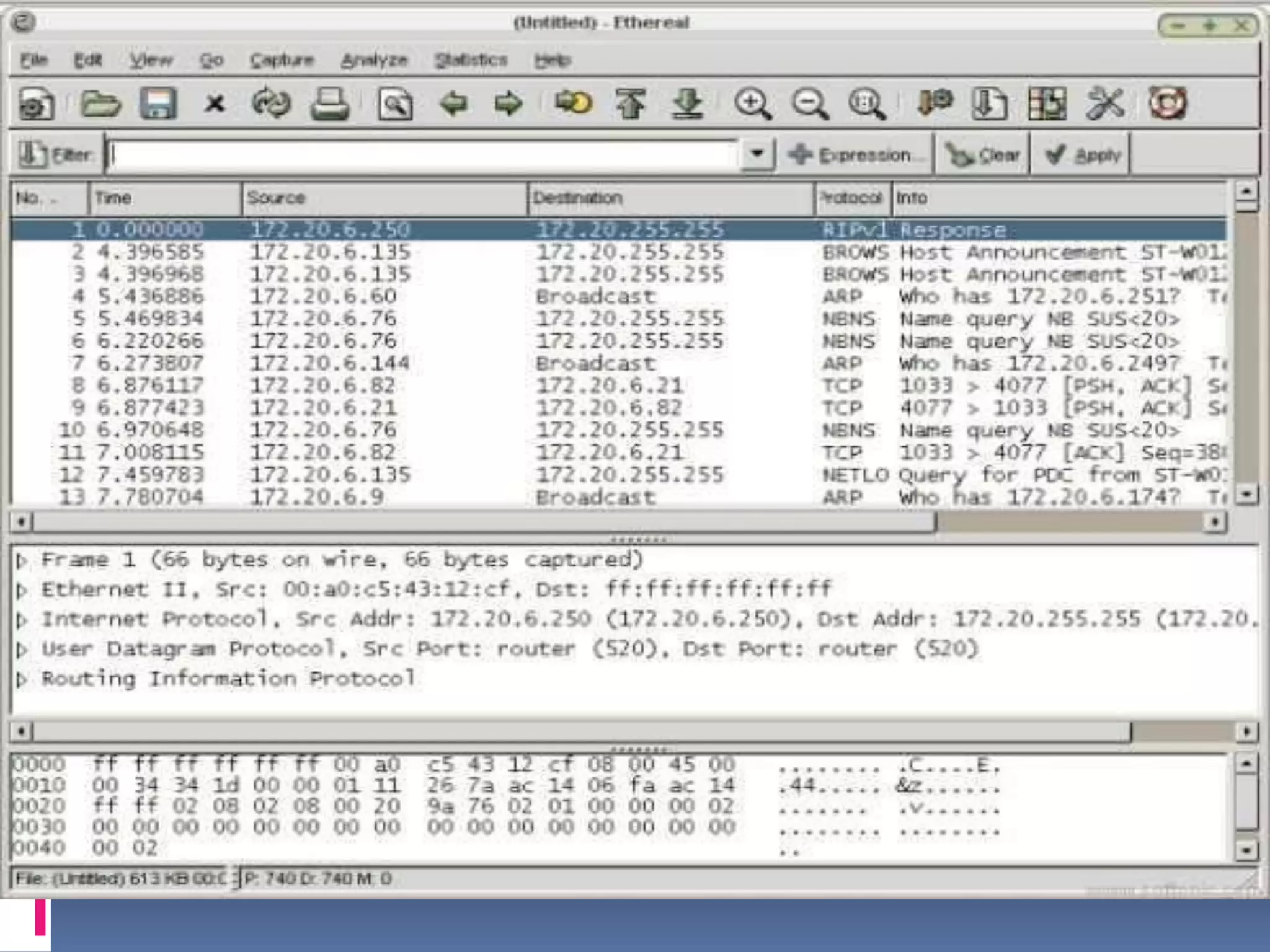
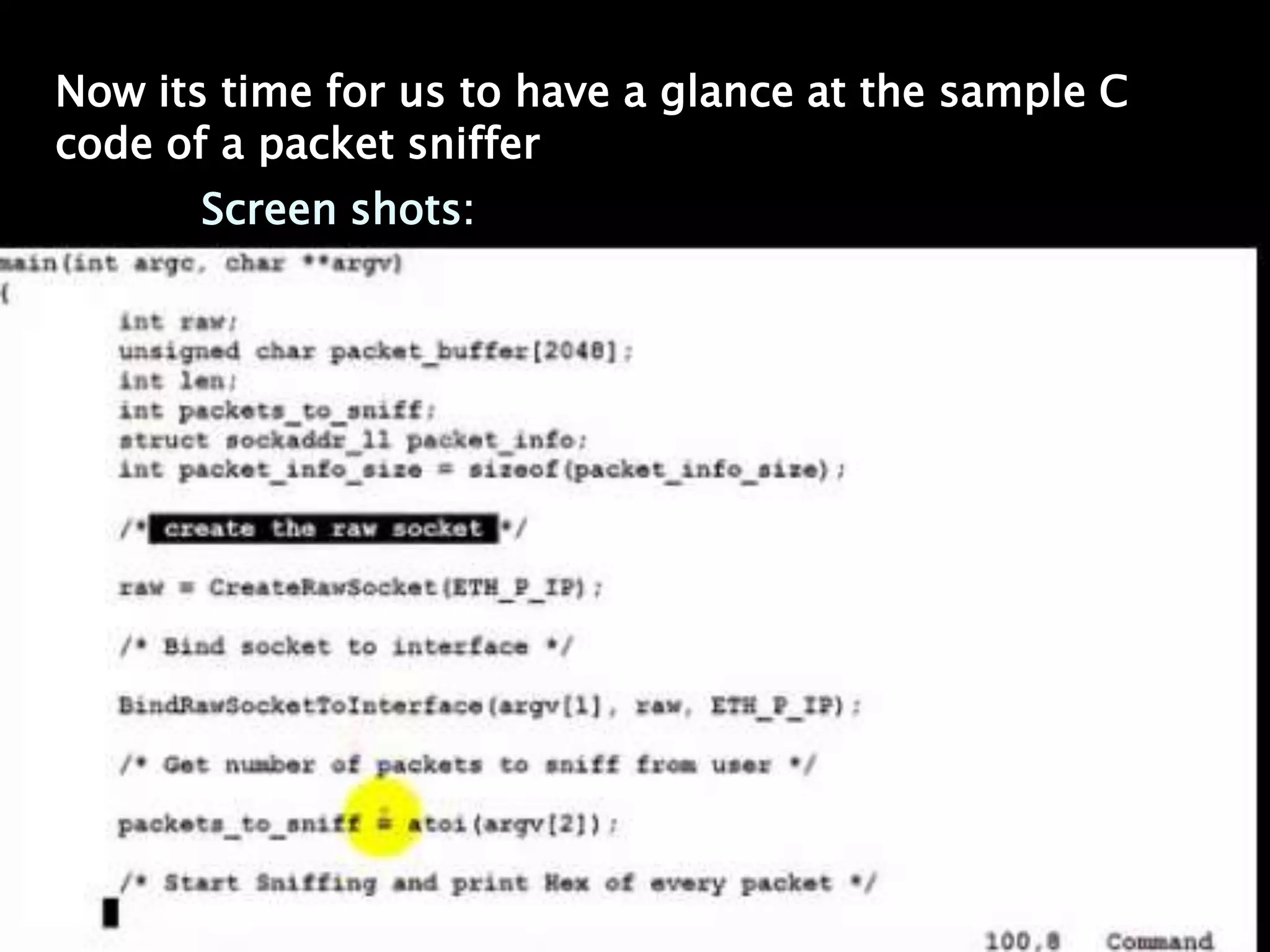
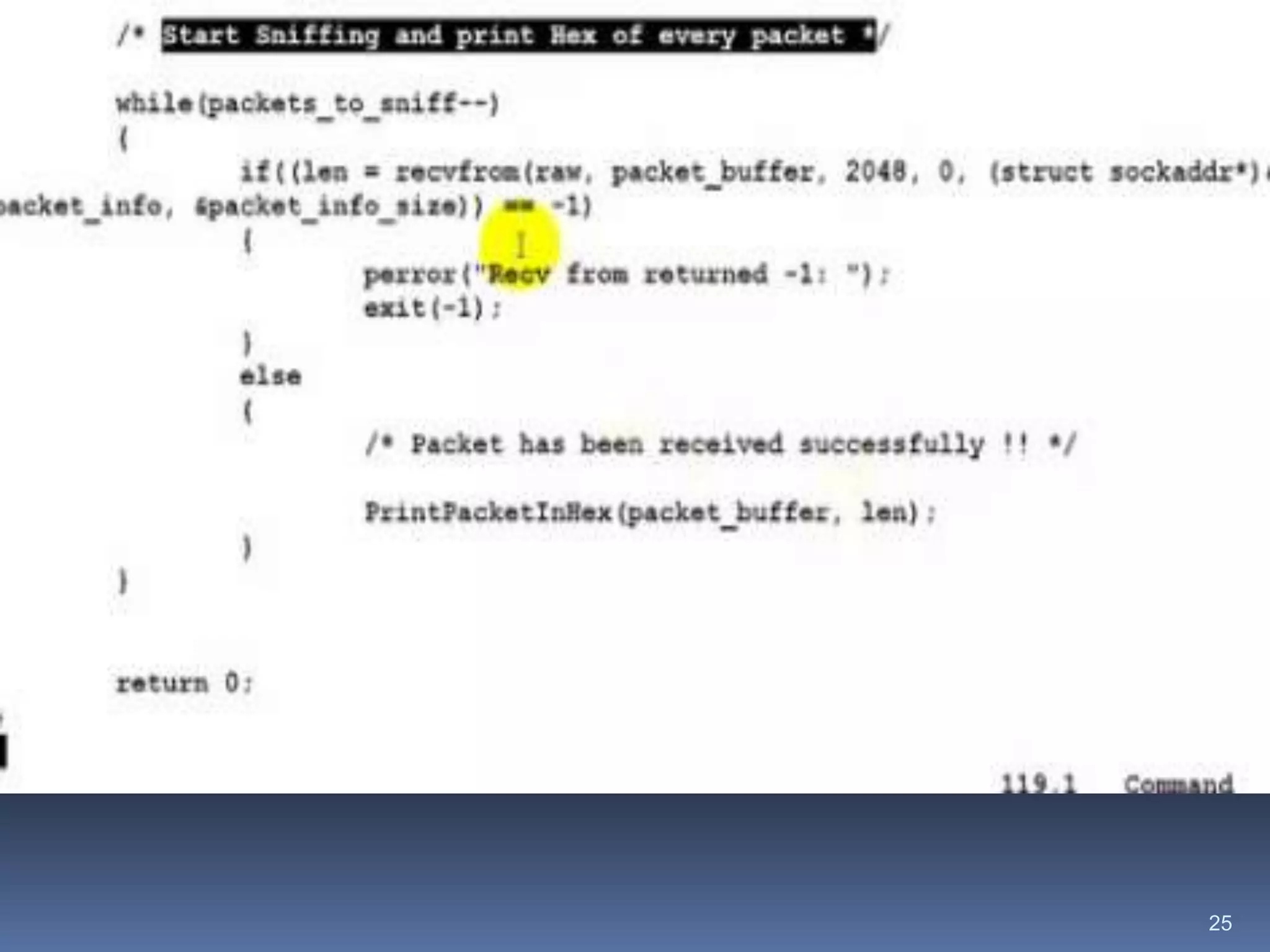
This document discusses packet sniffers, which are software applications that can monitor and capture network traffic. It describes how packet sniffers work by putting the network adapter into promiscuous mode to see all network traffic. The document outlines different types of packet sniffers, including commercial and underground varieties. It explains that packet sniffers are used for both legitimate purposes like network debugging and security, as well as illegitimate purposes like hacking. Specific packet sniffer software like Wireshark are profiled, describing their features, capabilities, and limitations. Risks of using packet sniffers like potential security vulnerabilities are also highlighted.