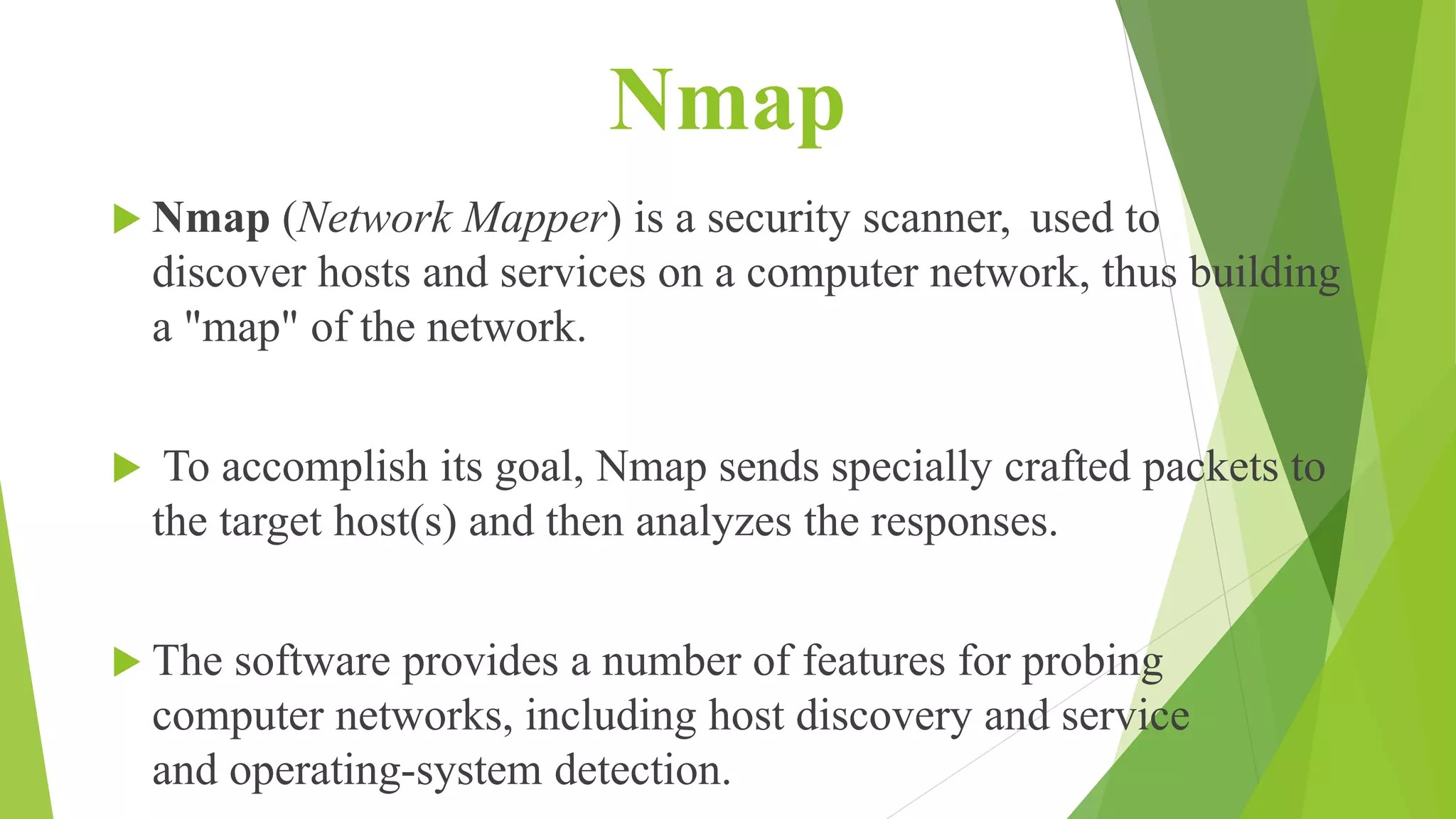
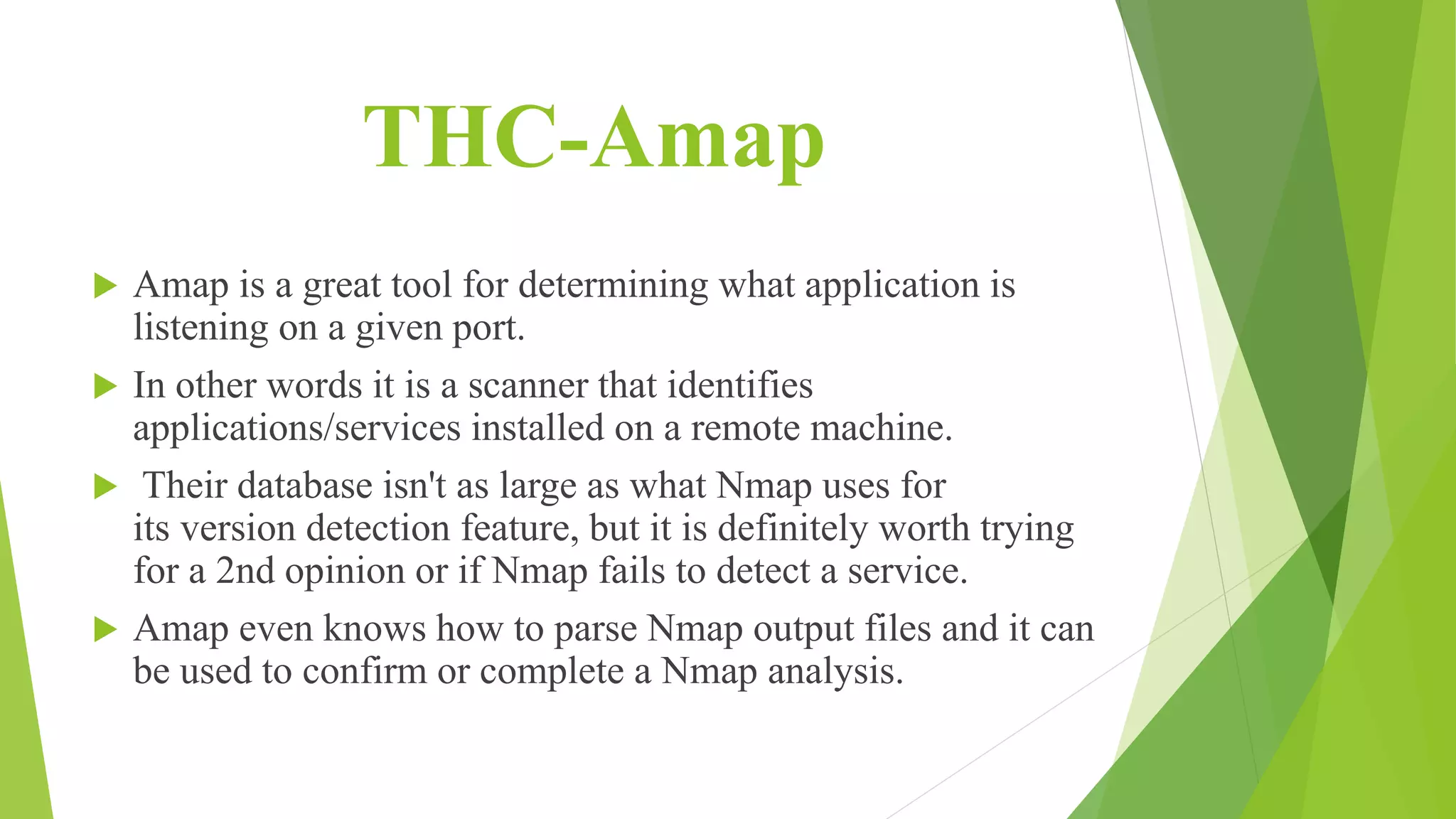
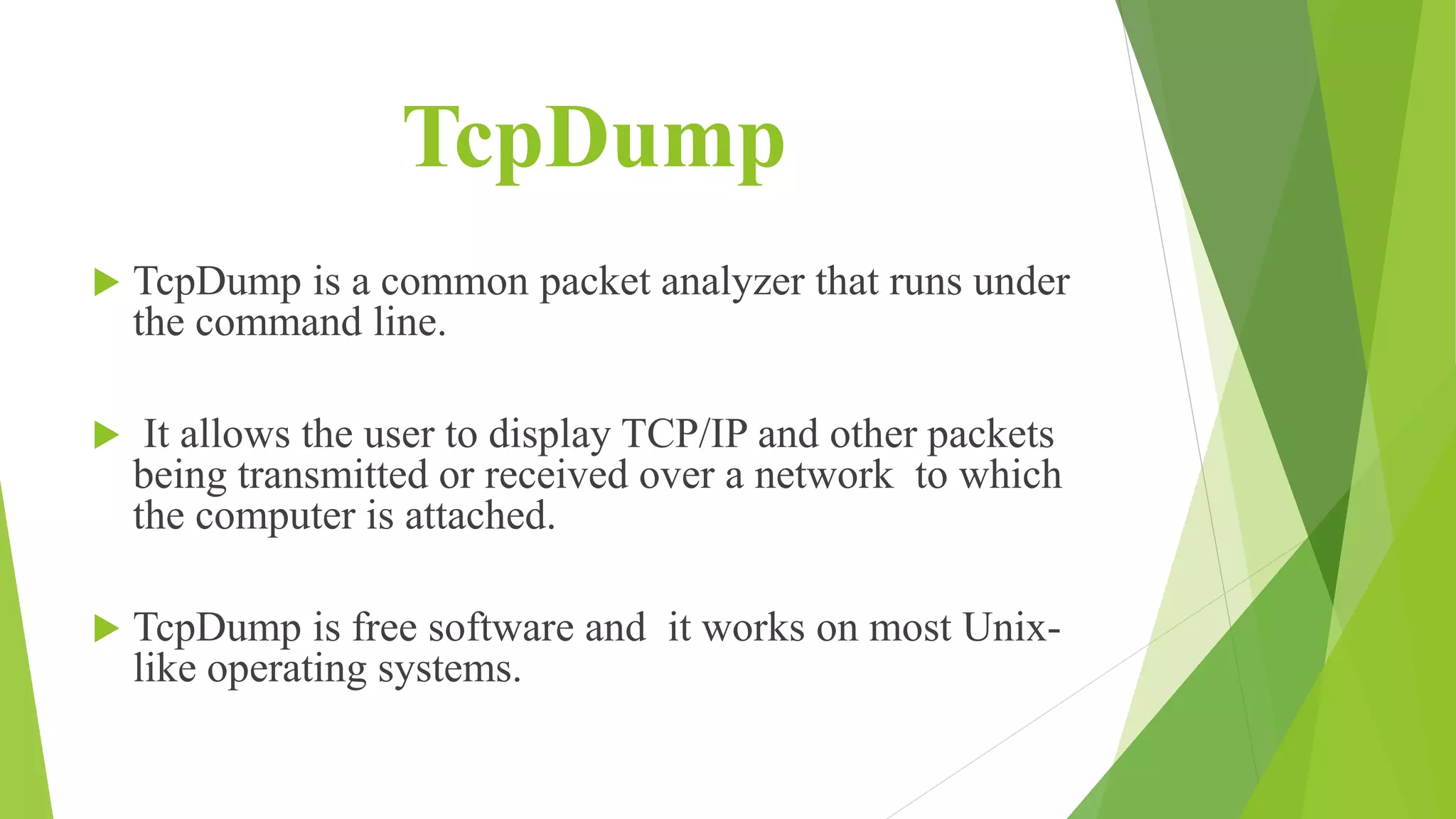
Network reconnaissance tools like Nmap and THC-Amap are used to discover hosts, services, and potential vulnerabilities on a computer network. Nmap sends custom packets to analyze responses and build a network map, while THC-Amap identifies applications listening on ports. Network sniffing tools such as Wireshark, TcpDump and WinDump capture and analyze packet-level traffic to locate network problems. Common sniffers also include Ettercap, Hping and Kismet. Injection interferes with network connections by constructing spoofed packets.