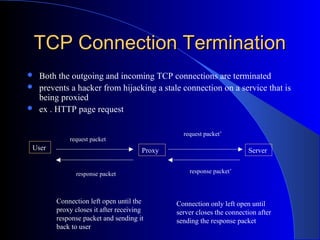
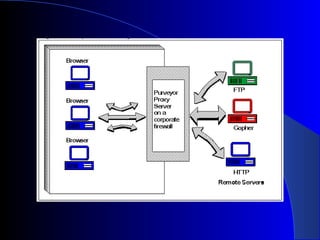
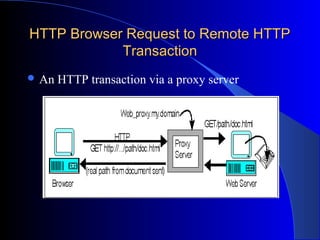
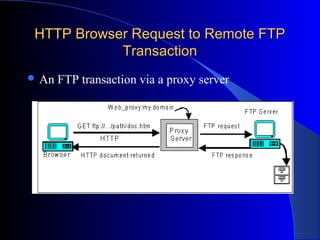
A web proxy server acts as an intermediary between clients and external servers on the internet. It protects clients by filtering traffic and limiting outside access. When a client requests a resource, the proxy server evaluates the request according to its rules before forwarding it to the external server. It then sends the response back to the client. This allows all clients connected to the proxy server to access the internet from behind the firewall with improved security and performance. The proxy server can also cache frequently requested resources to speed up access.