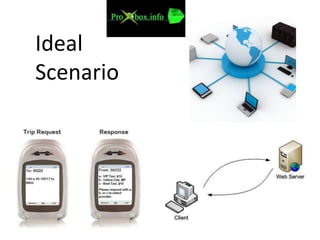
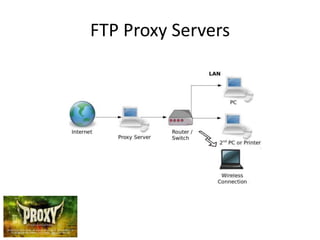
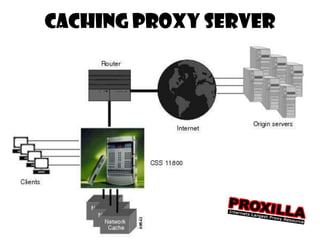
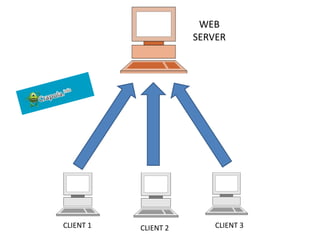
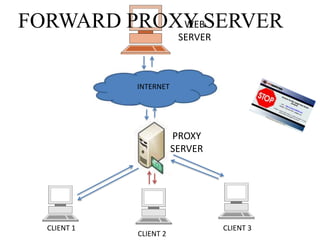
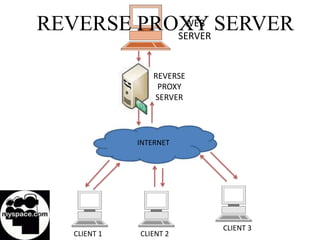
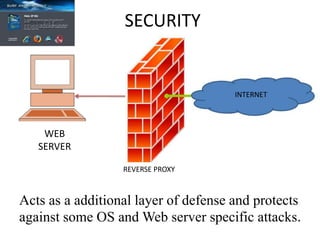
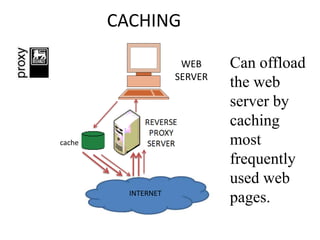
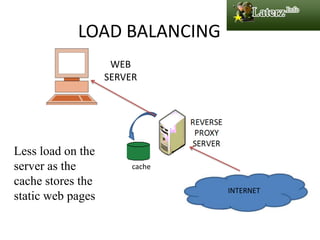
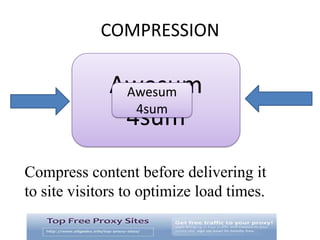
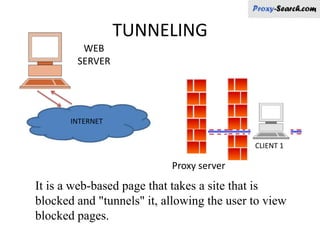
This document discusses various types of proxy servers including anonymous proxy servers, HTTP proxy servers, FTP proxy servers, caching proxy servers, content filtering proxy servers, reverse proxy servers, and ICAP servers. It provides details on their functions and purposes. Team members on the Awesum4sum project are listed and an index outlines topics covered which include introduction to proxy servers, advantages and disadvantages, and a demonstration on CC Proxy.