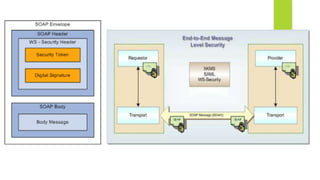
Web Services Security (WS-Security) is a proposed standard that addresses securing data exchanged as part of a web service. It provides authentication, authorization, confidentiality, integrity, and non-repudiation. Security can be implemented at the transport level using SSL/TLS to secure the communication channel, or at the message level by securing the SOAP message itself using standards like XML Encryption, XML Signature, and WS-Security. Transport level security secures the connection, while message level security secures individual messages and allows security to travel with the message between applications and intermediaries.