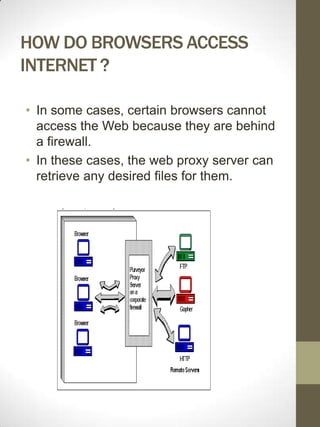
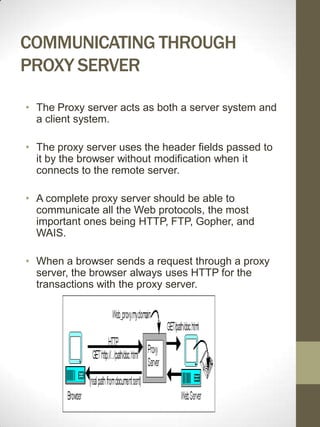
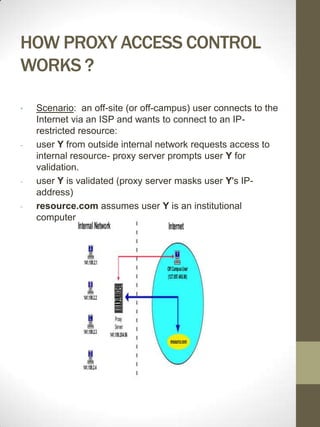
A web proxy server functions as a firewall by limiting outside access to client computers and protecting them from hackers. It allows clients connected to the proxy server to access the internet from behind the firewall with minimal effort and without compromising security. The proxy server listens for requests from clients and forwards them to remote internet servers, and also listens for responses to send back to clients. This allows the proxy server to cache frequently requested documents and control internet access at the protocol level.