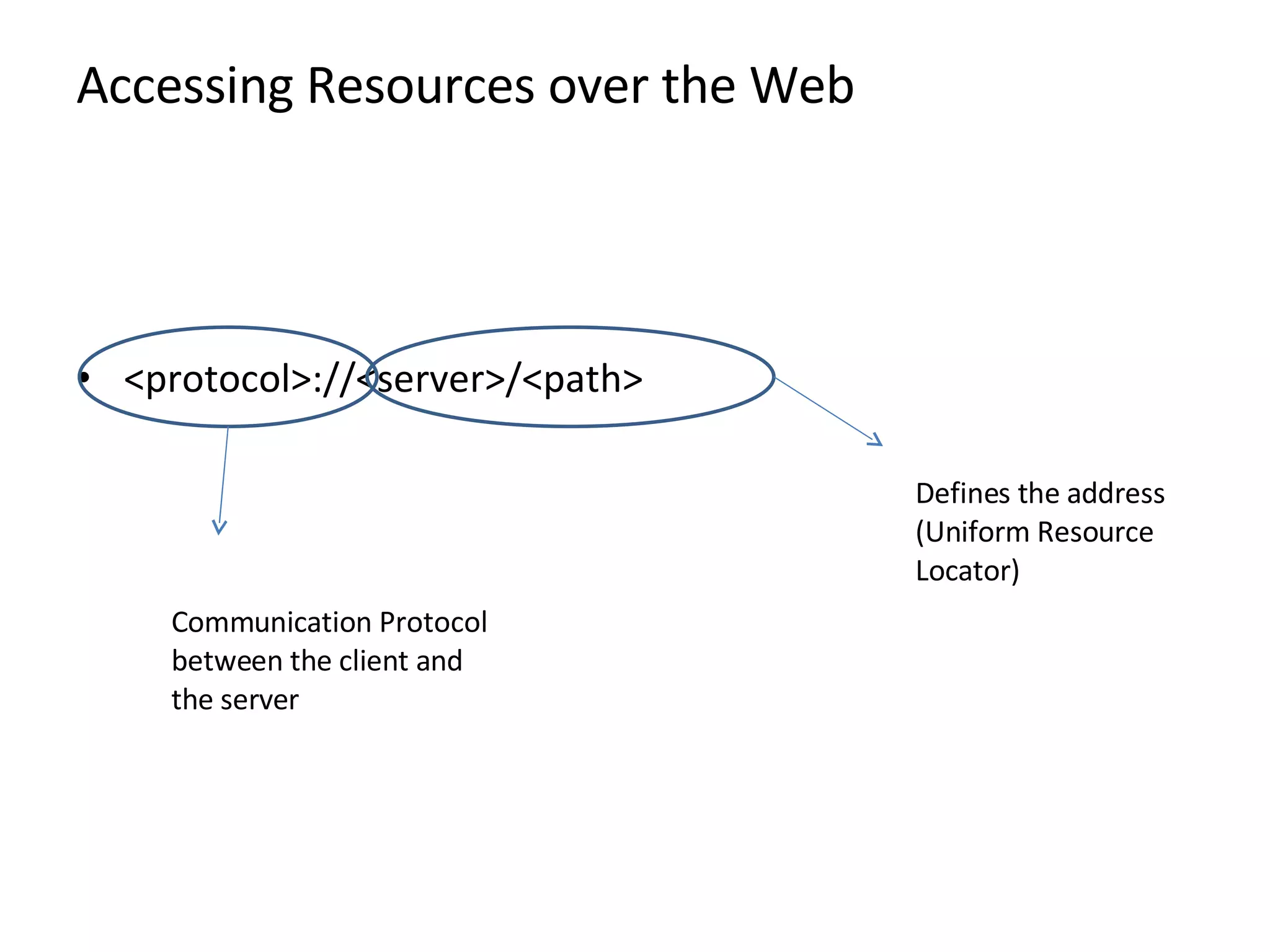
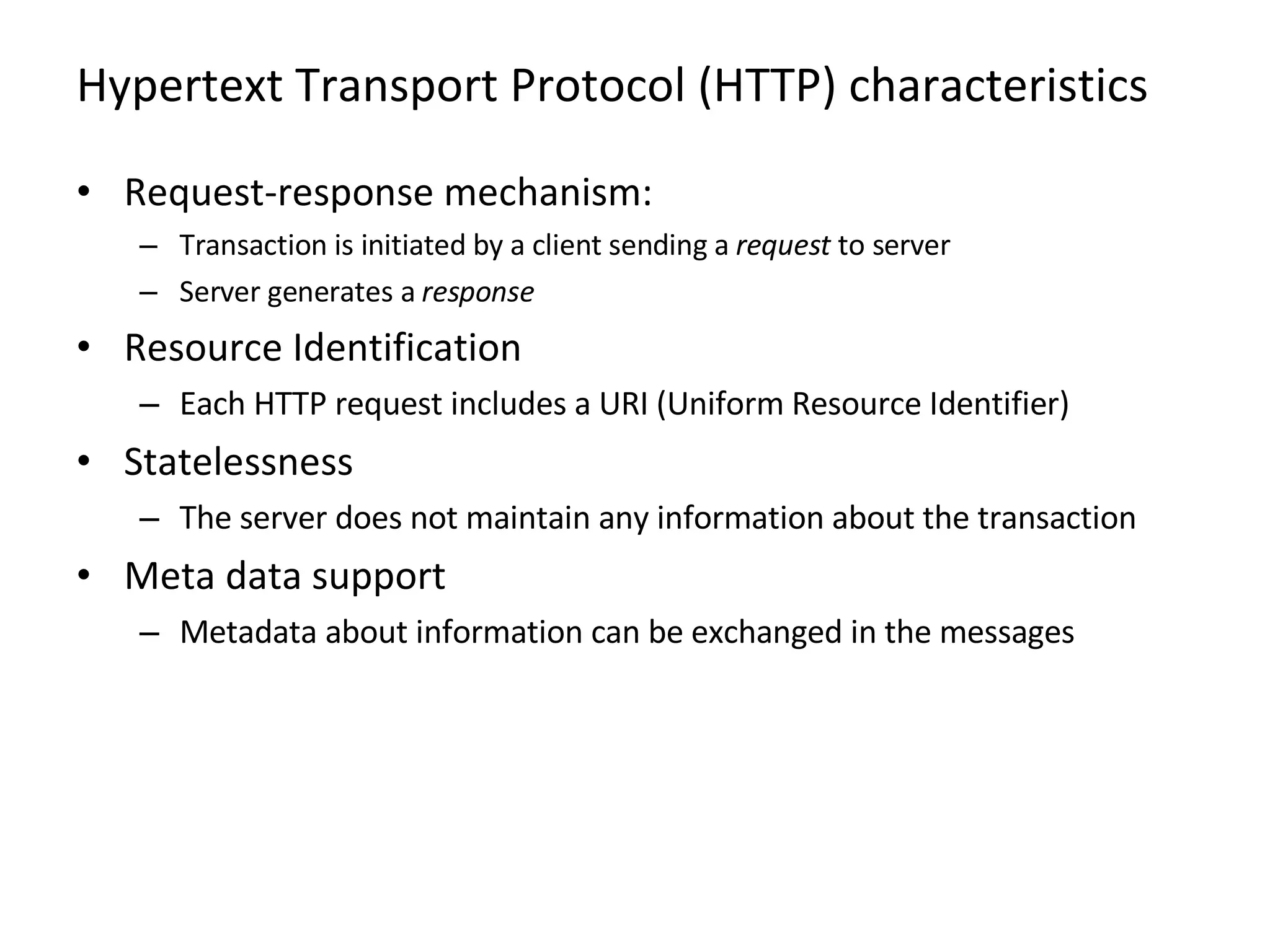
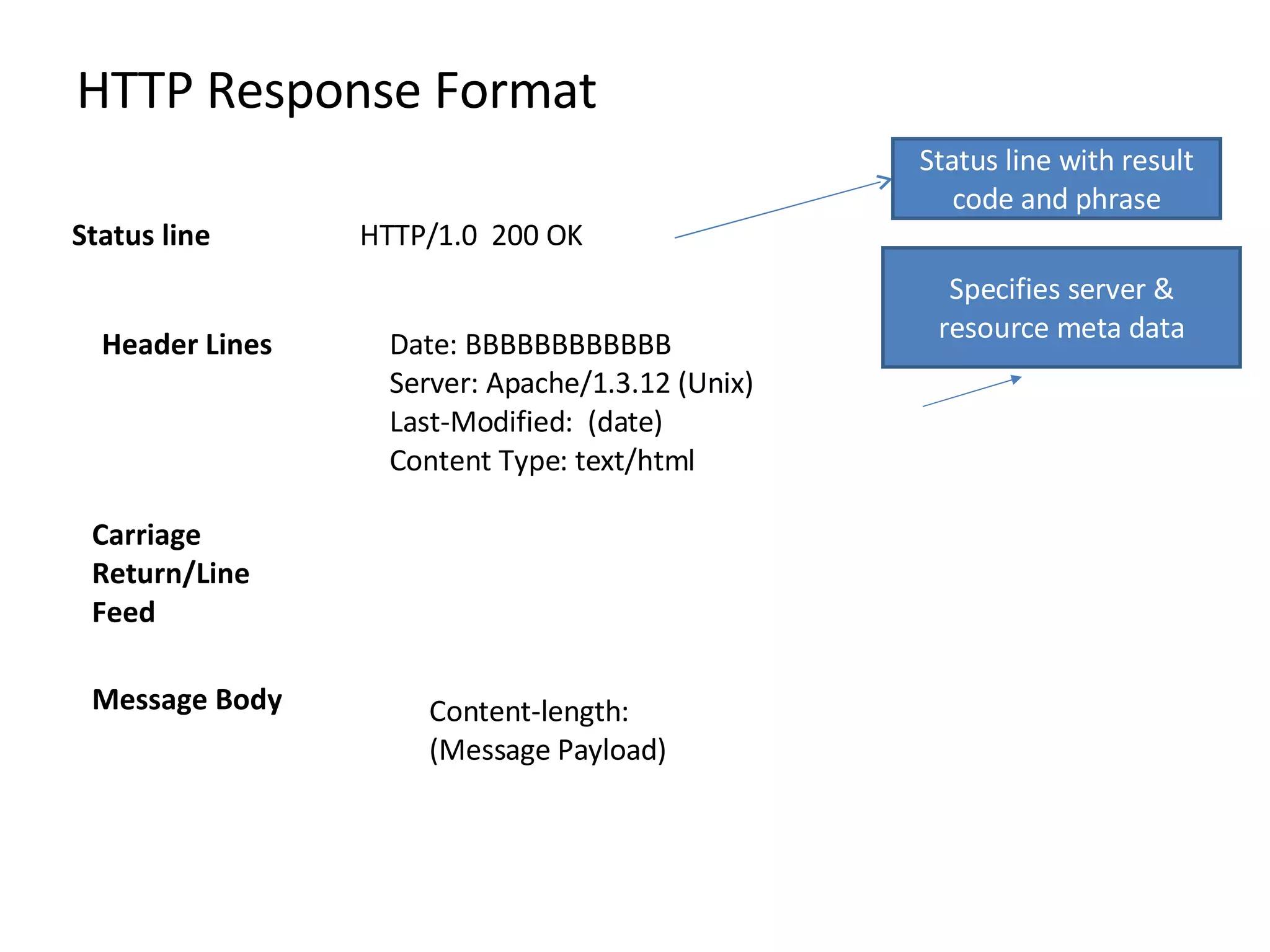
HTTP is the protocol that powers the web. It uses a request-response model where clients make requests that servers respond to. Common request methods include GET, POST, HEAD, PUT, DELETE, and OPTIONS. Responses include status codes like 200 for OK and content types. HTTP 1.1 added features like persistent connections and chunked encoding. Cookies are used to maintain statelessness. HTTPS uses SSL/TLS to secure HTTP connections with encryption, server authentication, and integrity.