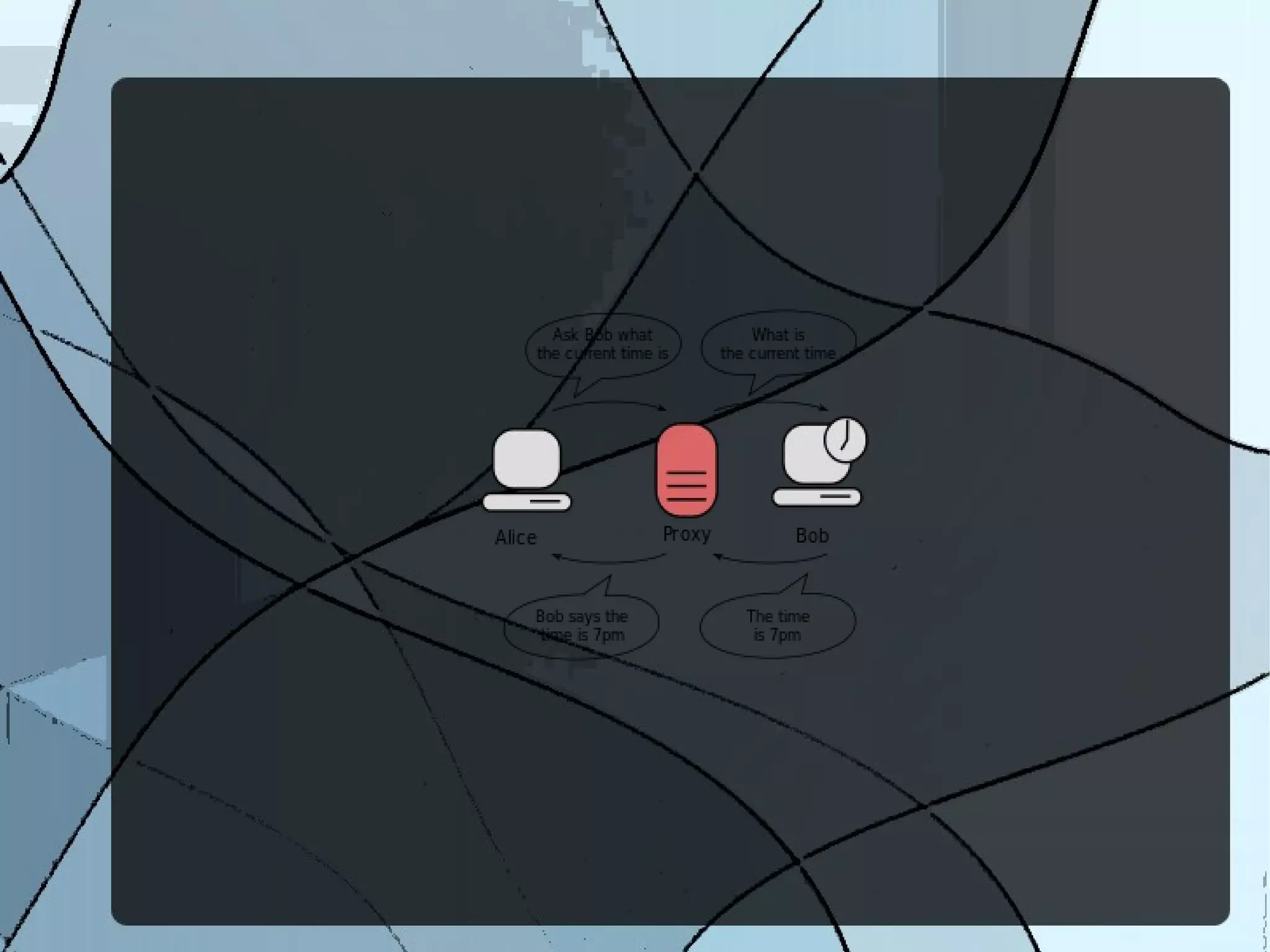
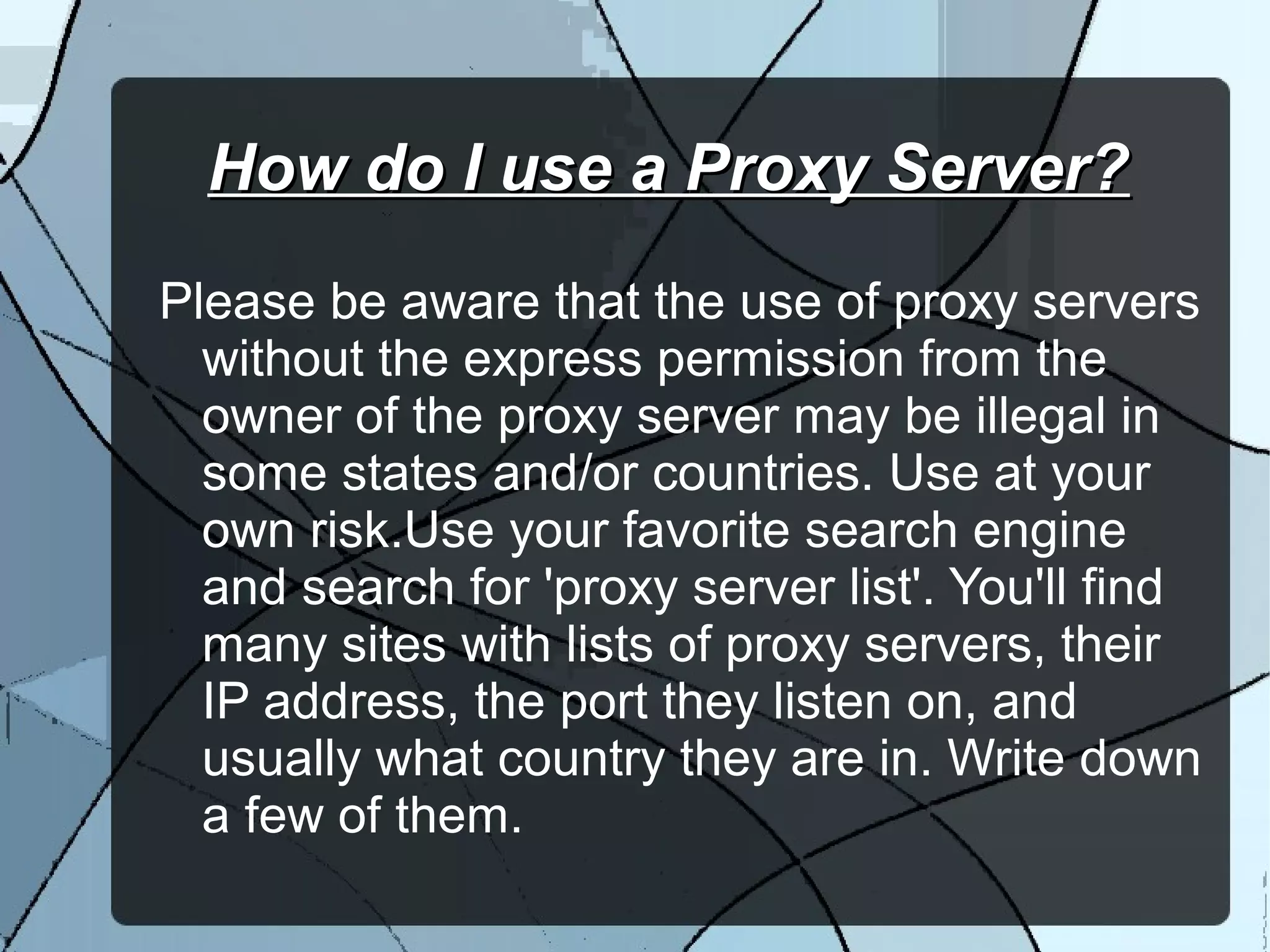
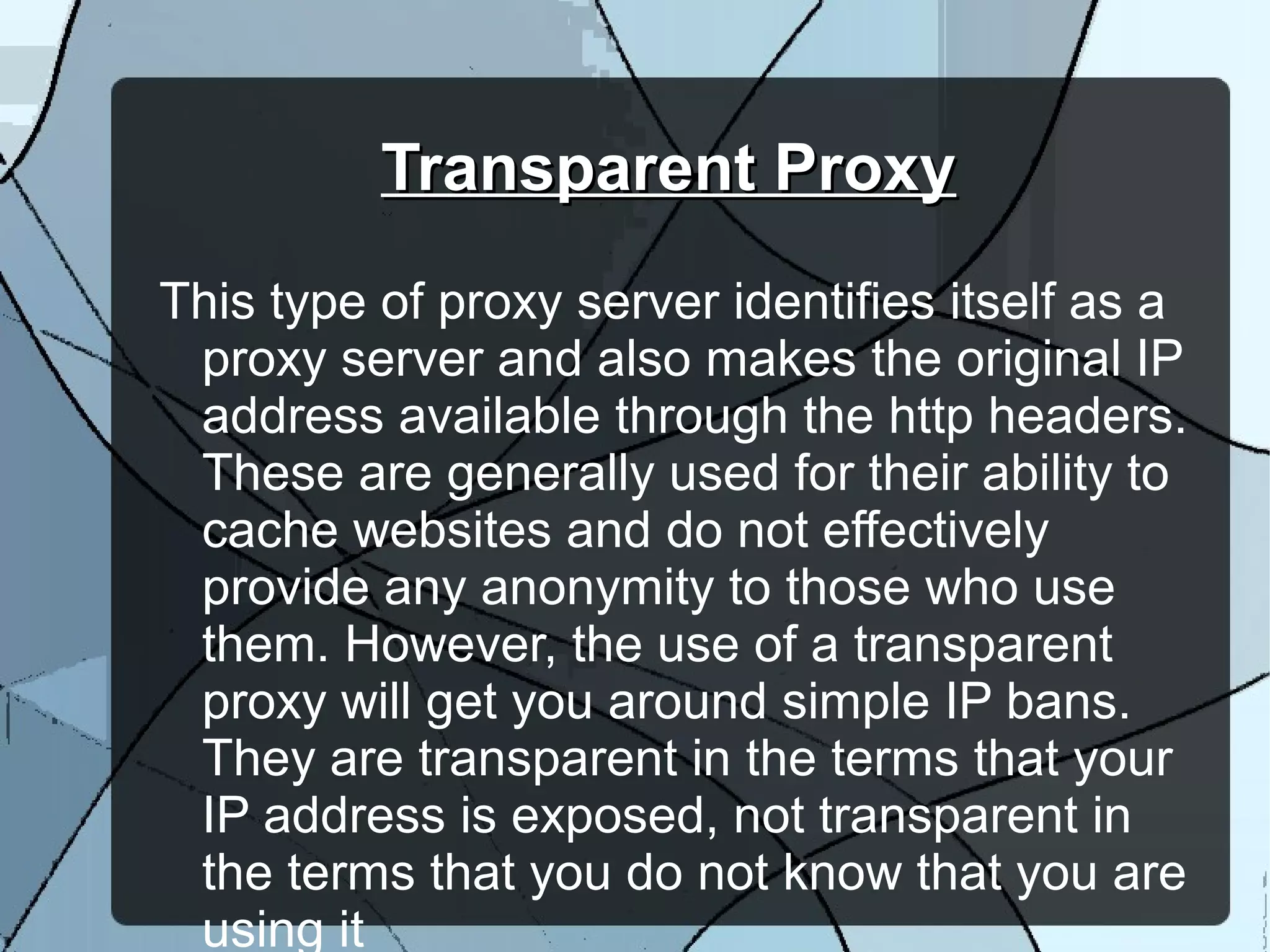
The document discusses various types of proxy servers, including transparent, anonymous, distorting, and high anonymity proxies, each offering different levels of anonymity and caching capabilities. It highlights the functions of web proxies, such as speeding up resource access, logging usage, preventing data loss, and filtering content. Users are advised to use proxy servers with caution and seek permission, as their usage may be illegal in certain jurisdictions.