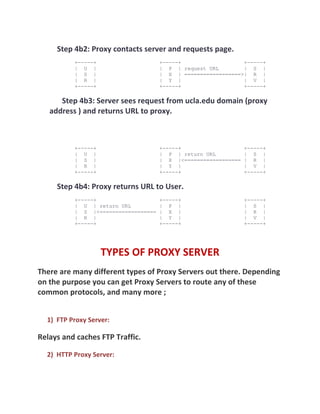
A proxy server acts as an intermediary between a client and the server they want to access. It intercepts all requests to the real server to see if it can fulfill the requests itself. If not, it forwards the request to the real server. Proxy servers improve performance by caching frequently requested content and filtering requests according to rules. Common types include HTTP, FTP, and SOCKS proxy servers. Proxy servers have advantages like improved performance and request filtering but also disadvantages like possible security risks, bandwidth usage, and speed issues.







![through ProxyWay - you stay anonymous when you visit web sites,
download files, send emails, etc.
www.proxyserverprivacy.com/proxy-web-sites -
You can access blocked or restricted websites by using Yahoo
Babelfish or Google Translate language tools as a proxy server
www.topproxysites.com –
Top Proxy Sites and list server sorted out daily!
www.bestproxysites.com –
It provides you with a Free list of proxy websites for unfiltered web
www.daveproxy.co.uk-
If you require a proxy server that lets you anonymously surf the web
to the sites you want from our UK server
www.hideglobal.com –
HideGlobal.com - Free anonymous proxy sites, Free proxy server to
unblock websites myspace ,bebo, facebook - bypass web filter from
school and office .
DISADVANTAGE OF PROXY SERVER
1) It is possible for a computer to run as an open
proxy server without the computer's owner
knowing this. This can result from
misconfiguration of proxy software running on
the computer, or from infection
with malware (viruses, trojans or worms)
designed for this purpose.[2] If it is caused](https://image.slidesharecdn.com/proxyserver-091122013547-phpapp02/85/seminar-on-proxyserver-10-320.jpg)