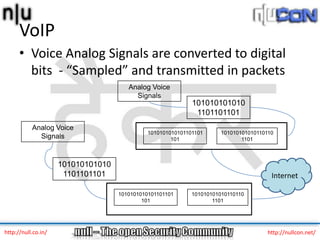
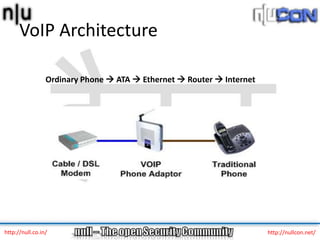
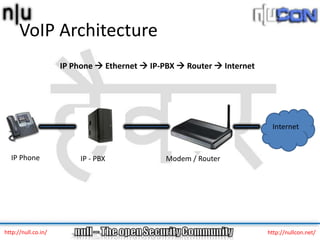
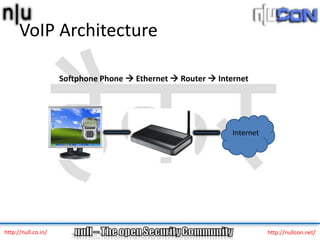
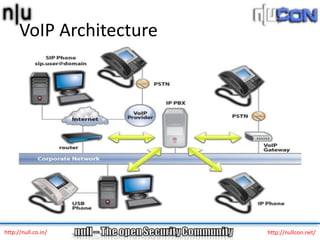
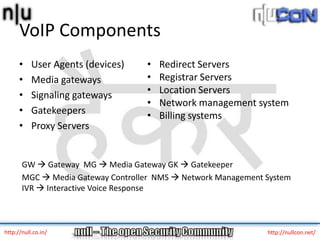
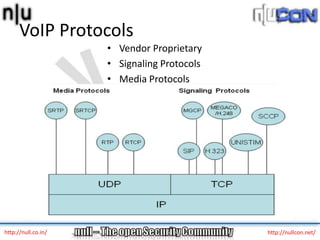
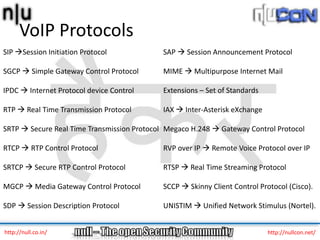
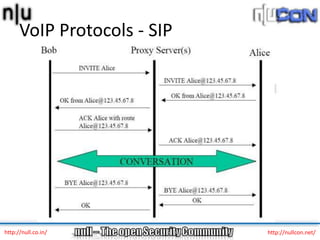
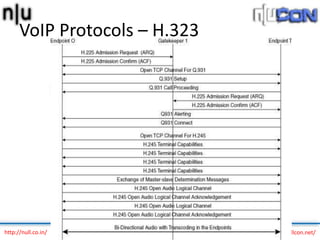
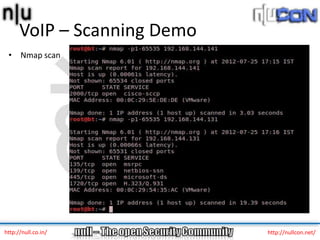
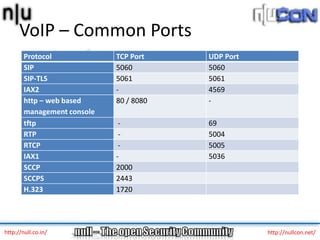
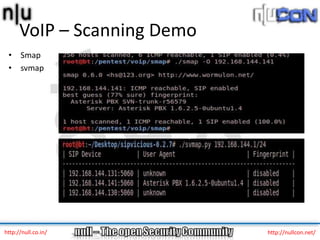
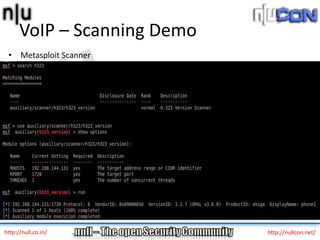
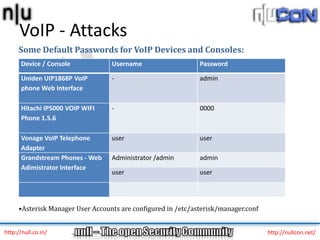
The document discusses vulnerabilities and attacks against Voice over IP (VoIP) systems. It begins with an introduction to VoIP architecture, components, and protocols. It then covers vulnerabilities and common attack vectors against VoIP, such as identity spoofing, eavesdropping, password cracking, and denial of service attacks. The document demonstrates some example attacks and outlines tools that can be used for scanning, attacking, and testing the security of VoIP systems. It concludes with recommendations for countermeasures like firewalls, encryption, and network hardening to better secure VoIP infrastructures.