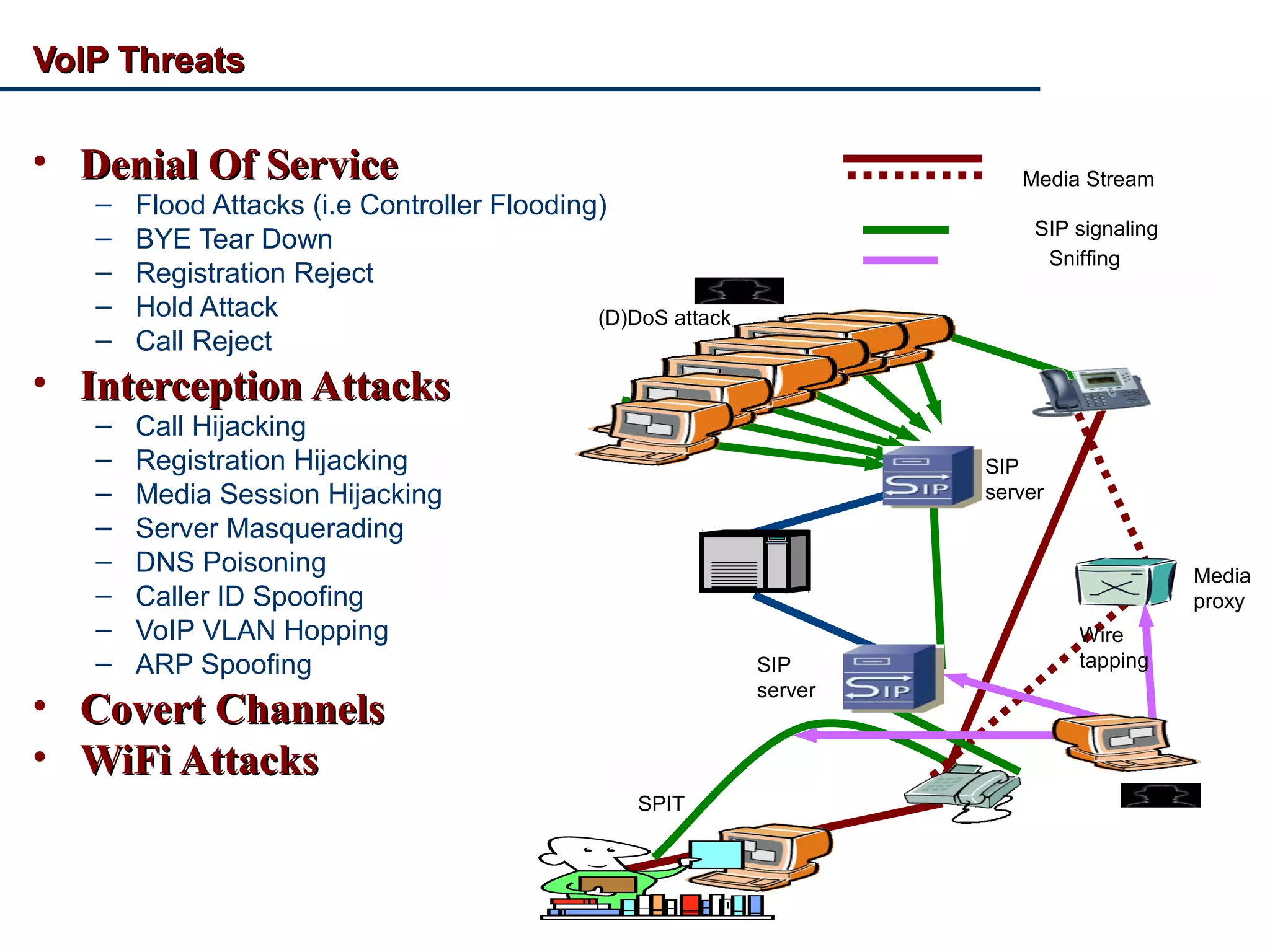
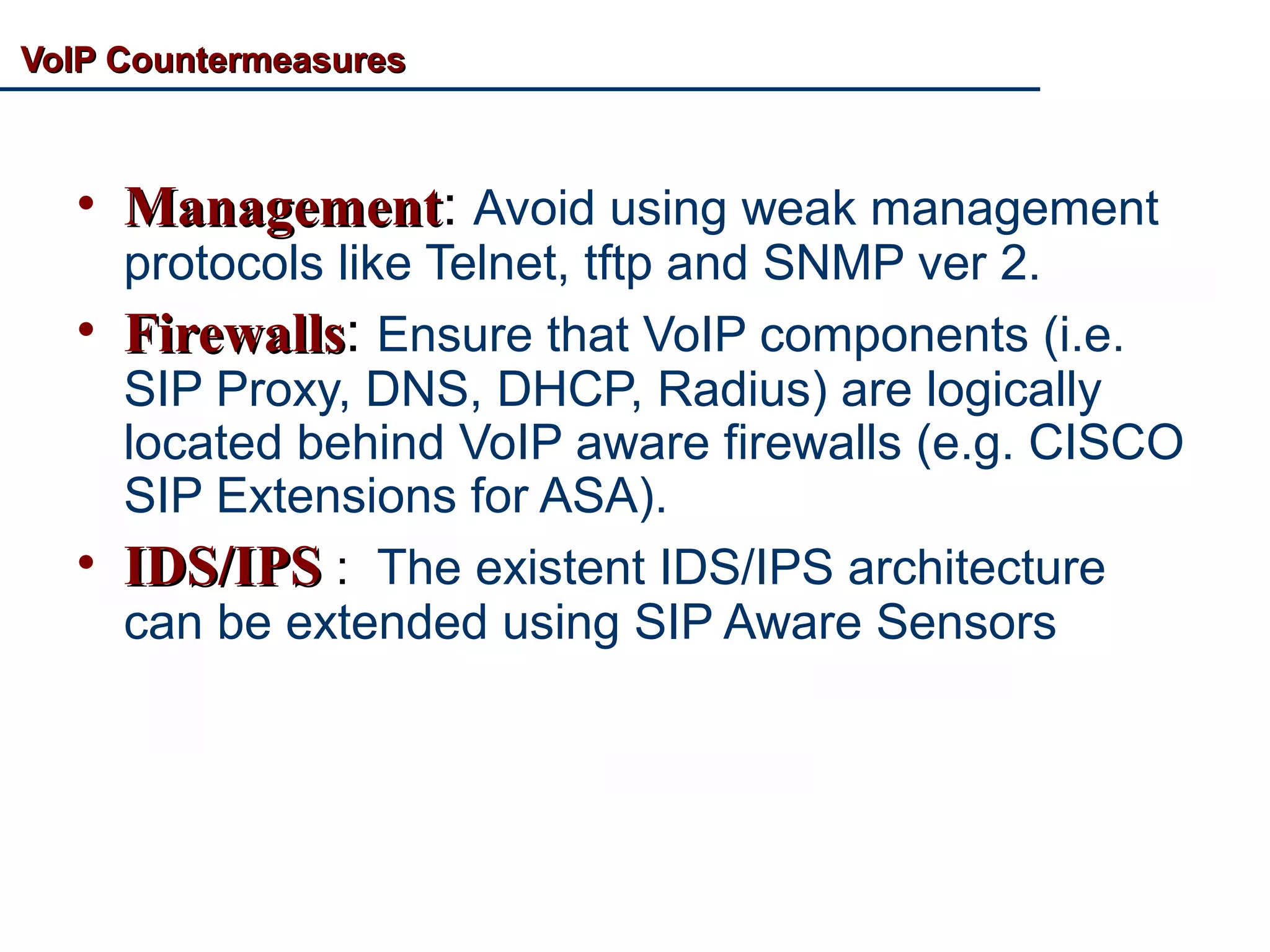
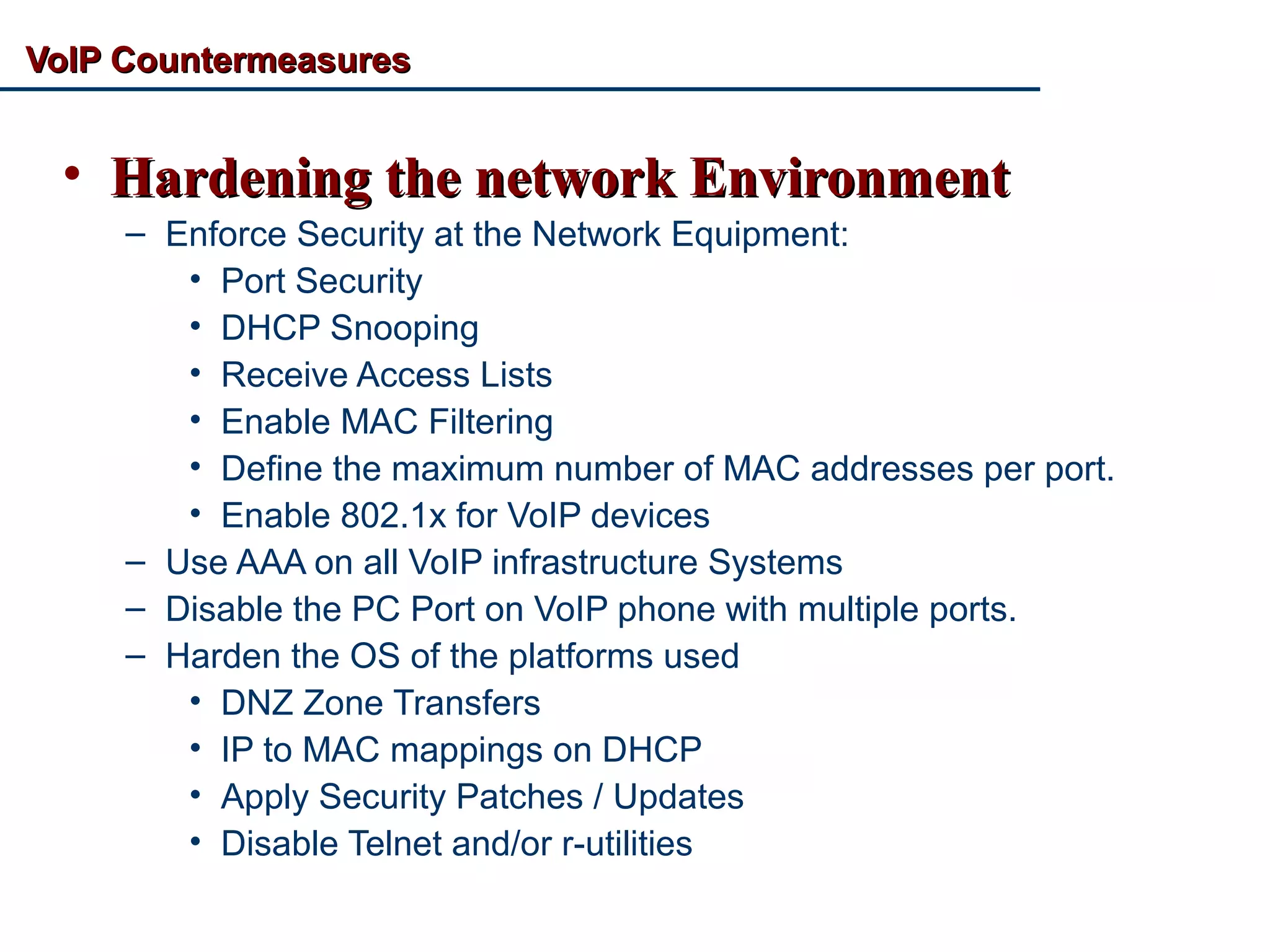
VoIP Security: An Overview discusses the security challenges of Voice over IP (VoIP) technology. It notes that VoIP inherits vulnerabilities from TCP/IP networks and uses the corporate network, making it complex to secure. Common VoIP threats include denial of service attacks, interception attacks, covert channels, and vulnerabilities in VoIP platforms. The document outlines example attacks and tools used by hackers. It recommends countermeasures like network separation, encryption of SIP and RTP, firewalls, intrusion detection systems, and hardening VoIP infrastructure and devices. VoIP honeypots can also be used to detect attackers.