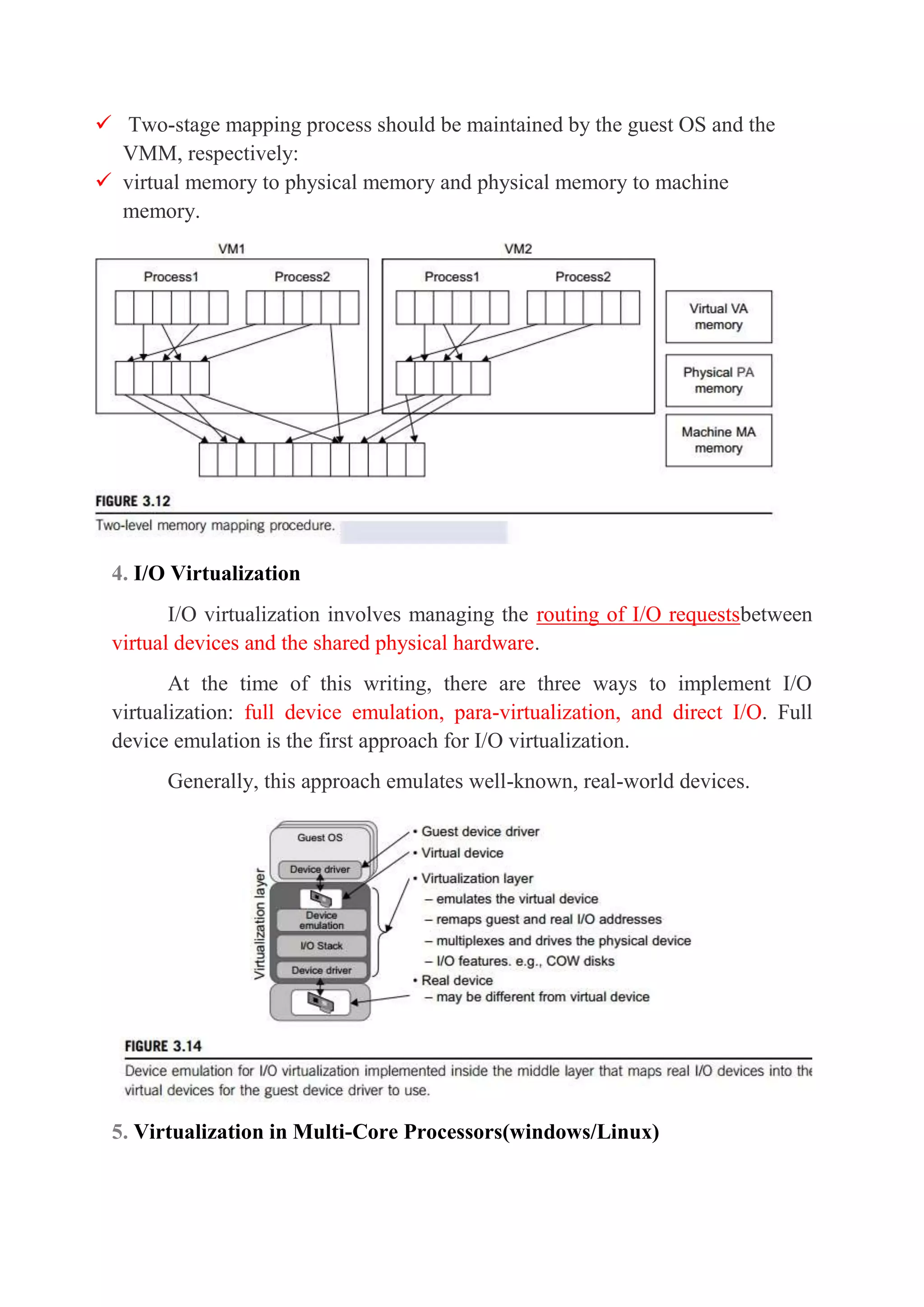
This document discusses different aspects of virtualization including CPU, memory, I/O devices, and multi-core processors. It describes how CPU virtualization works by classifying instructions as privileged, control-sensitive, or behavior-sensitive and having a virtual machine monitor mediate access. Memory virtualization uses two-stage address mapping between virtual and physical memory. I/O virtualization manages routing requests between virtual and physical devices using emulation, para-virtualization, or direct access. Virtualizing multi-core processors introduces challenges for programming models, scheduling, and managing heterogeneous resources.