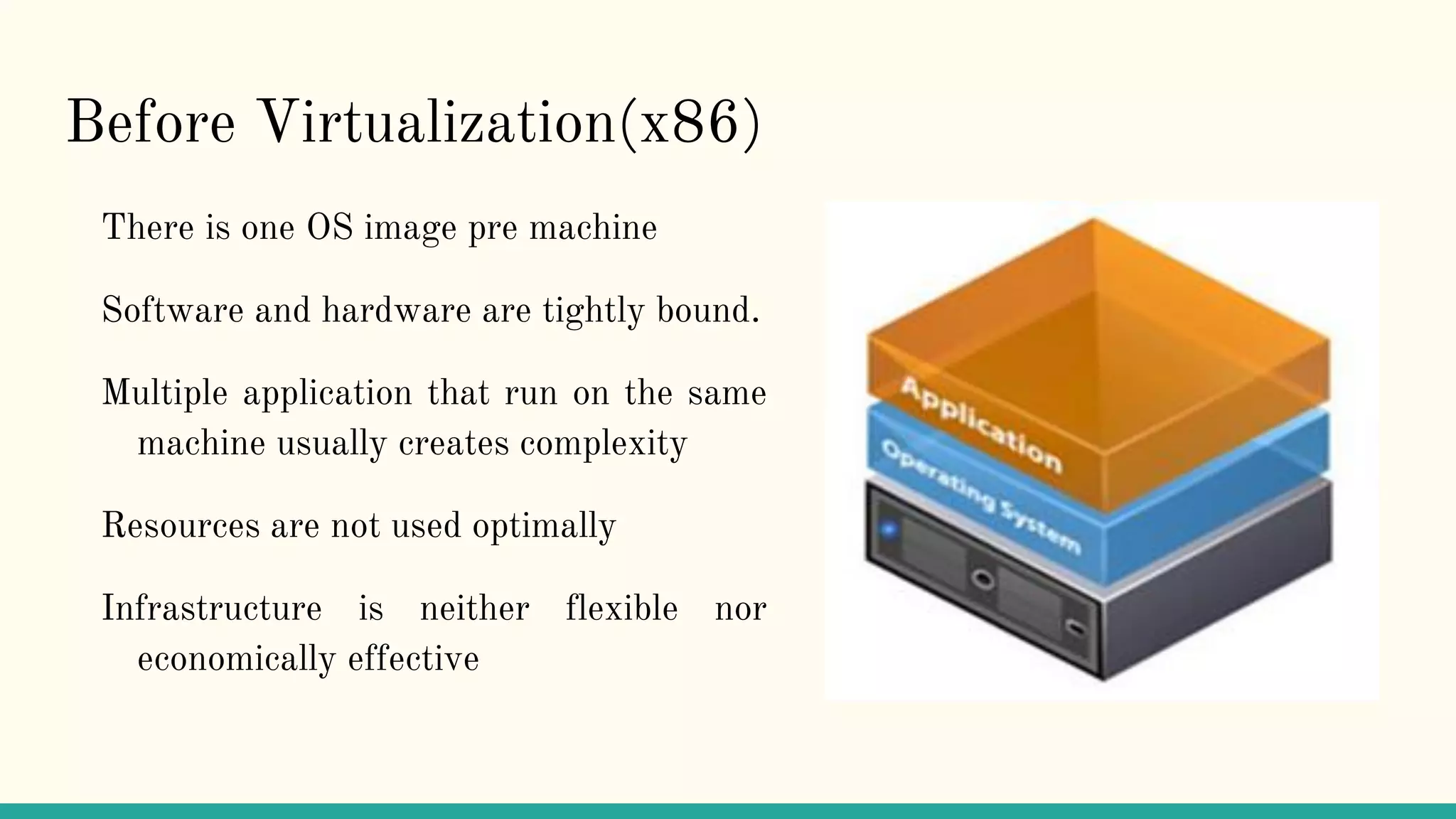
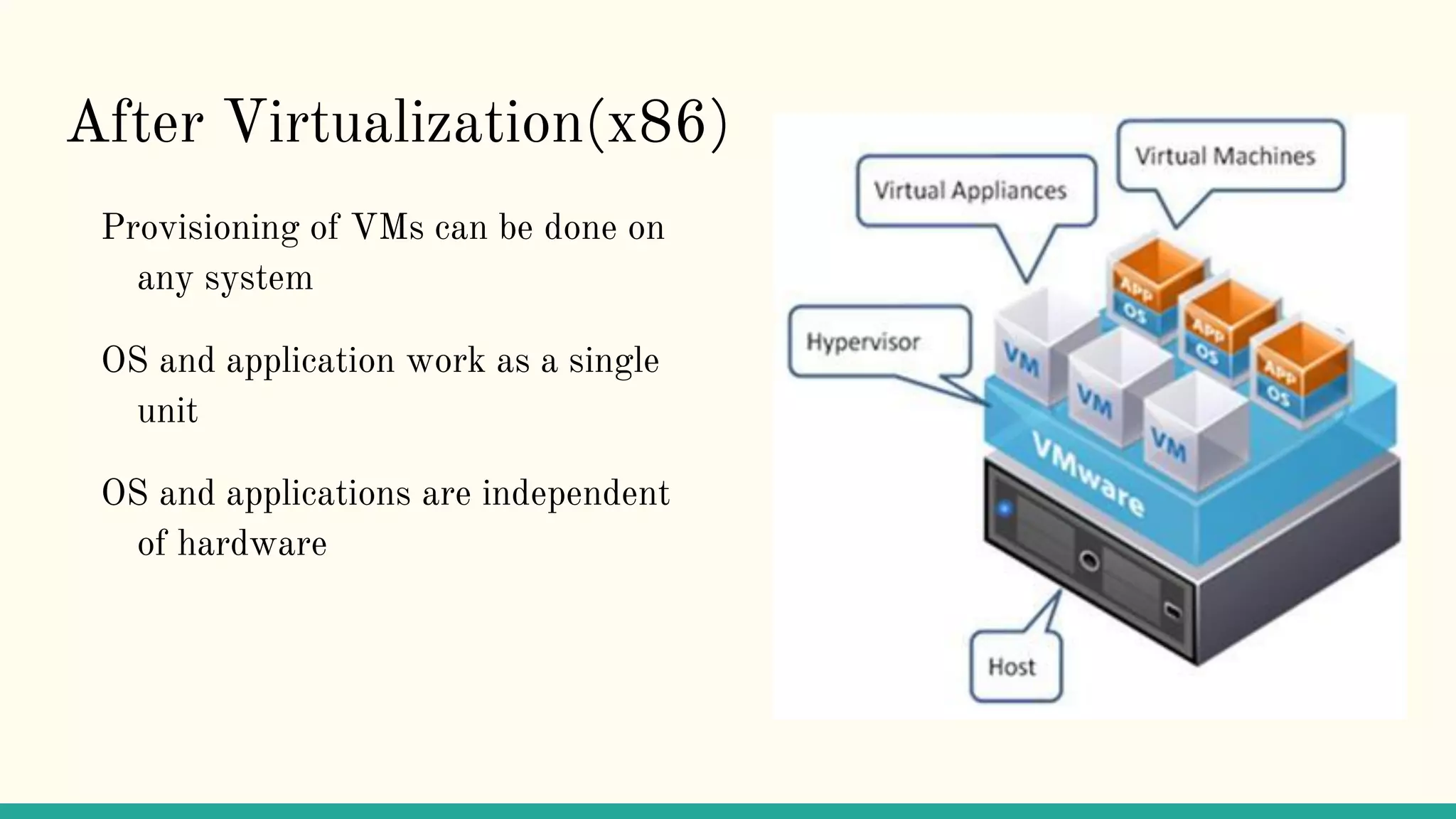
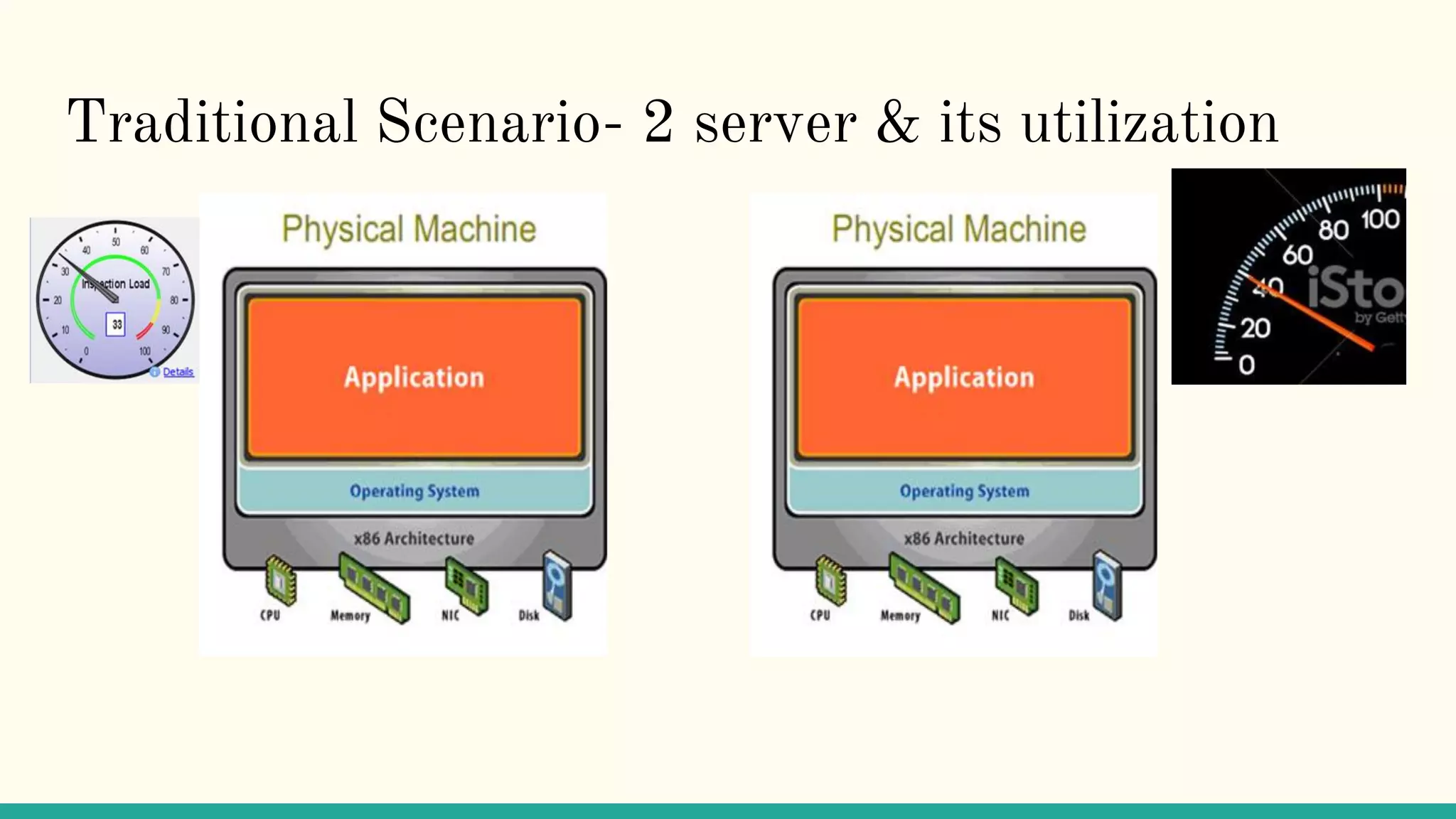
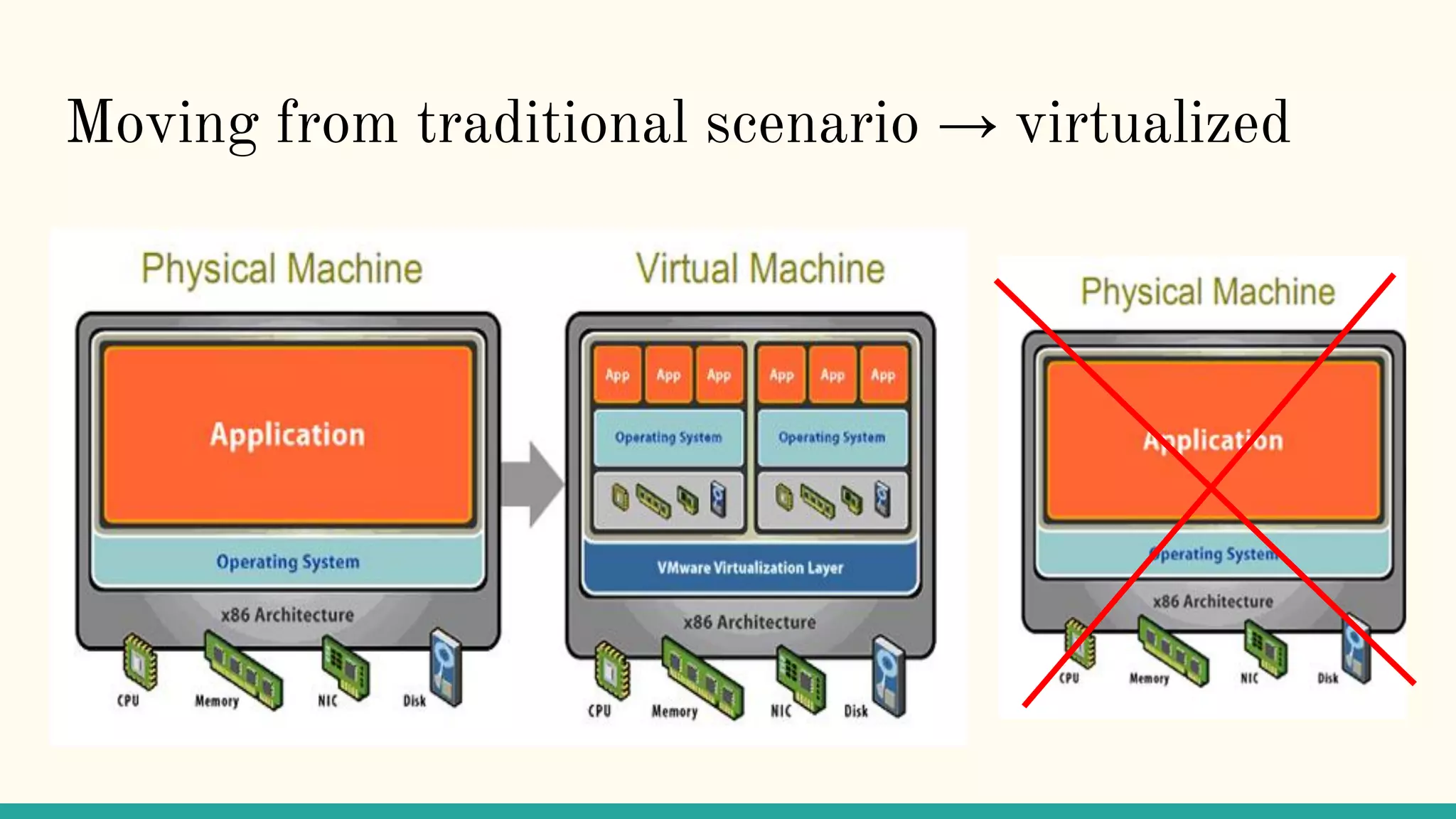
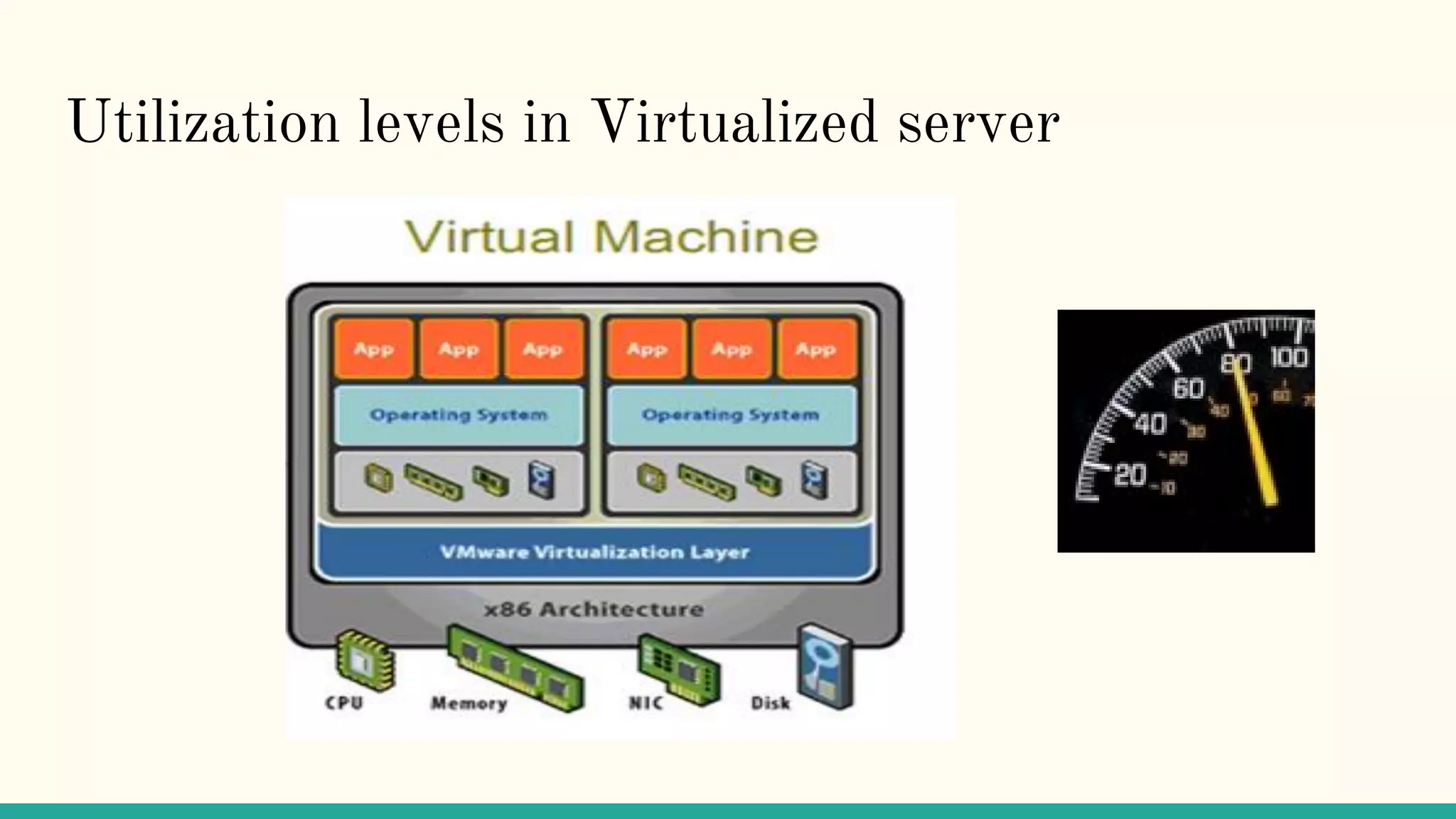
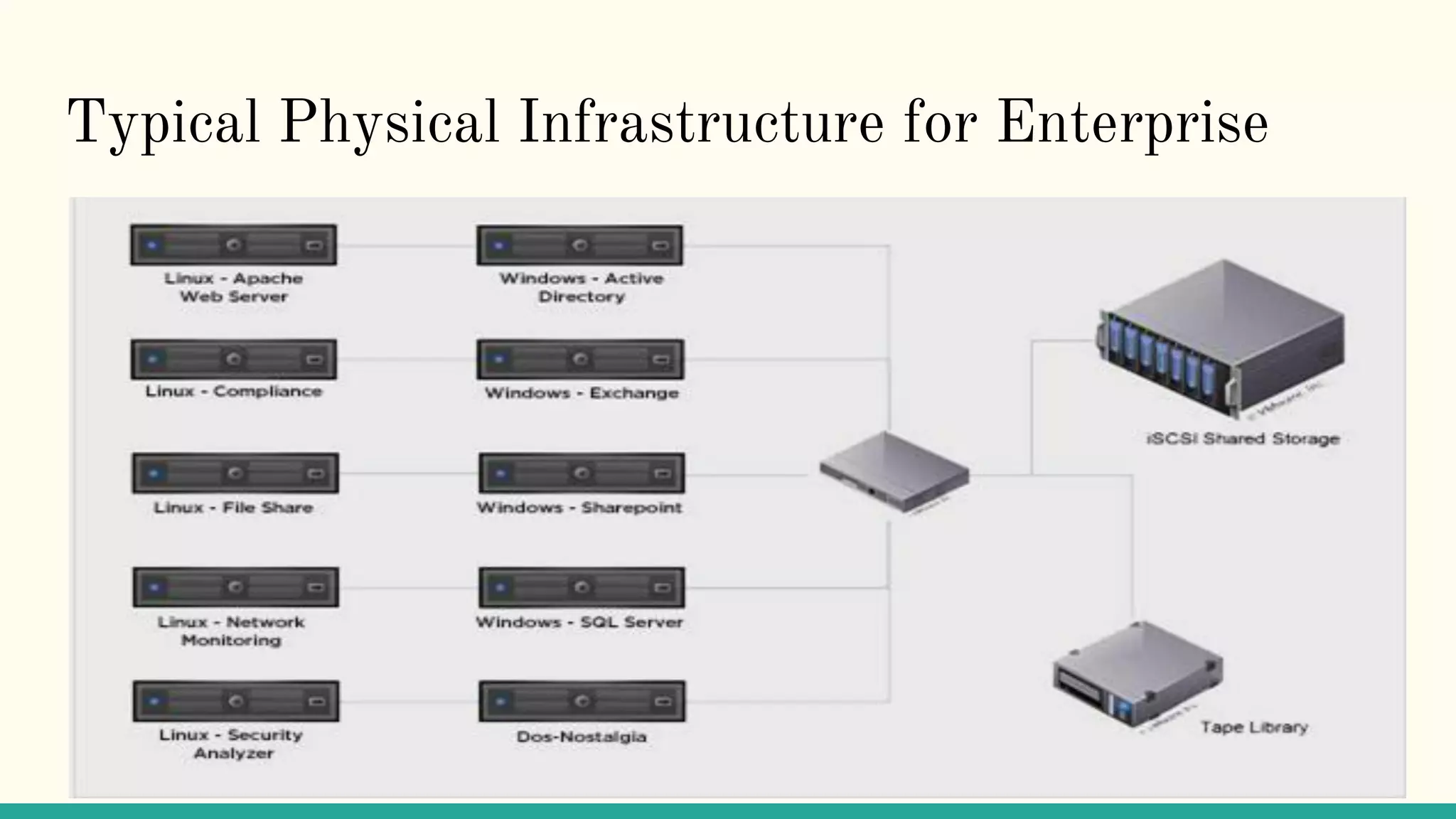
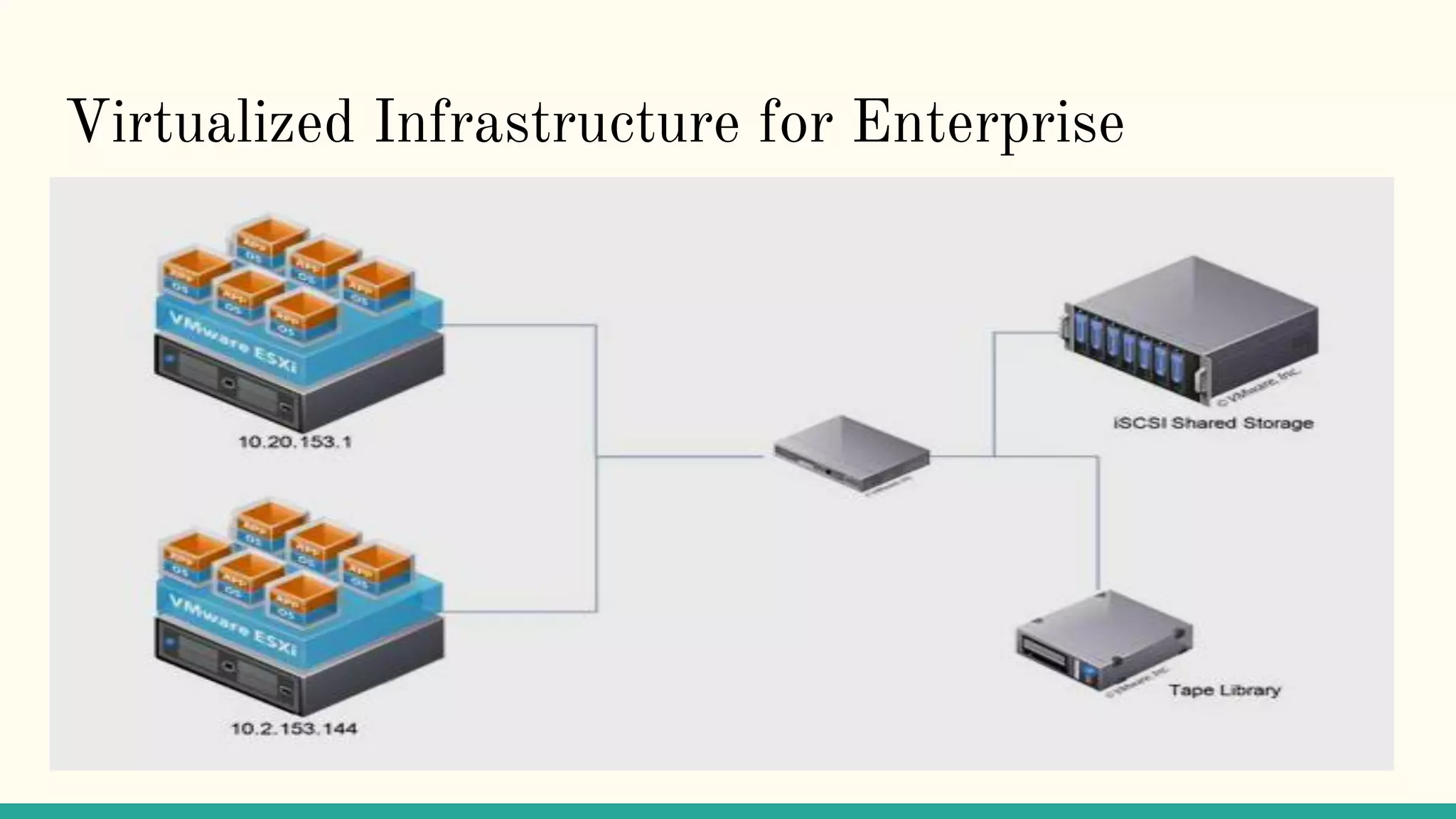
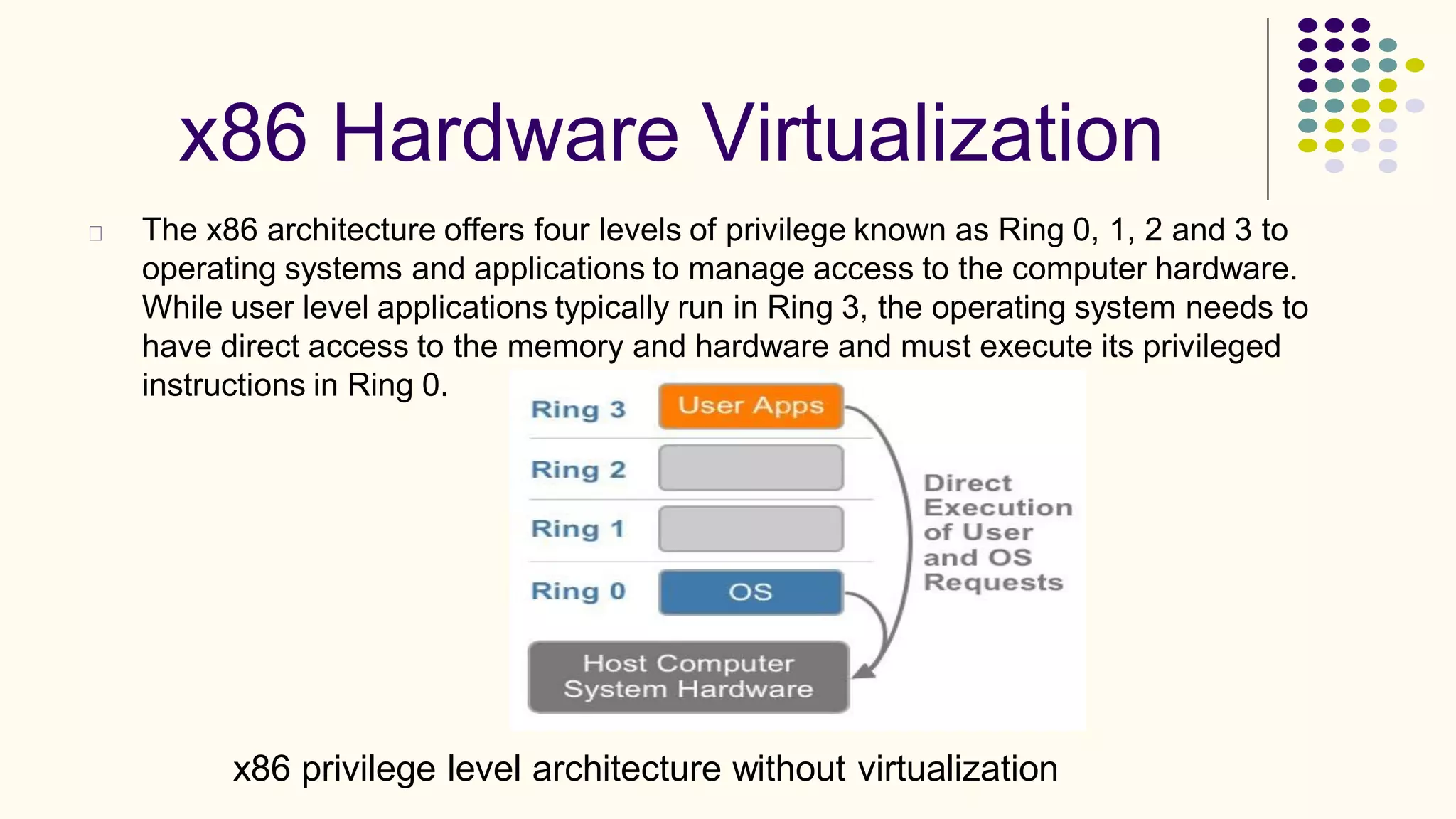
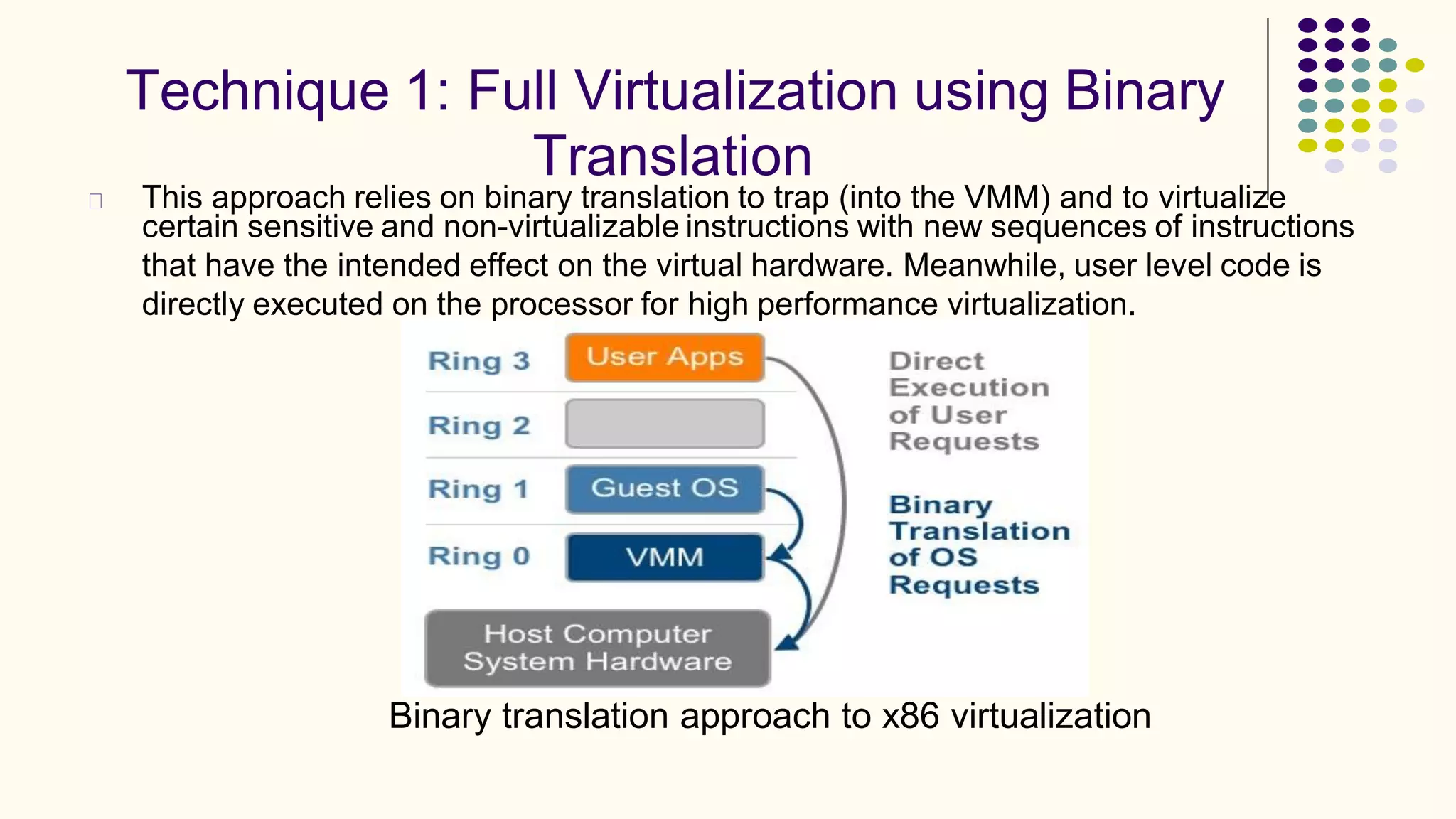
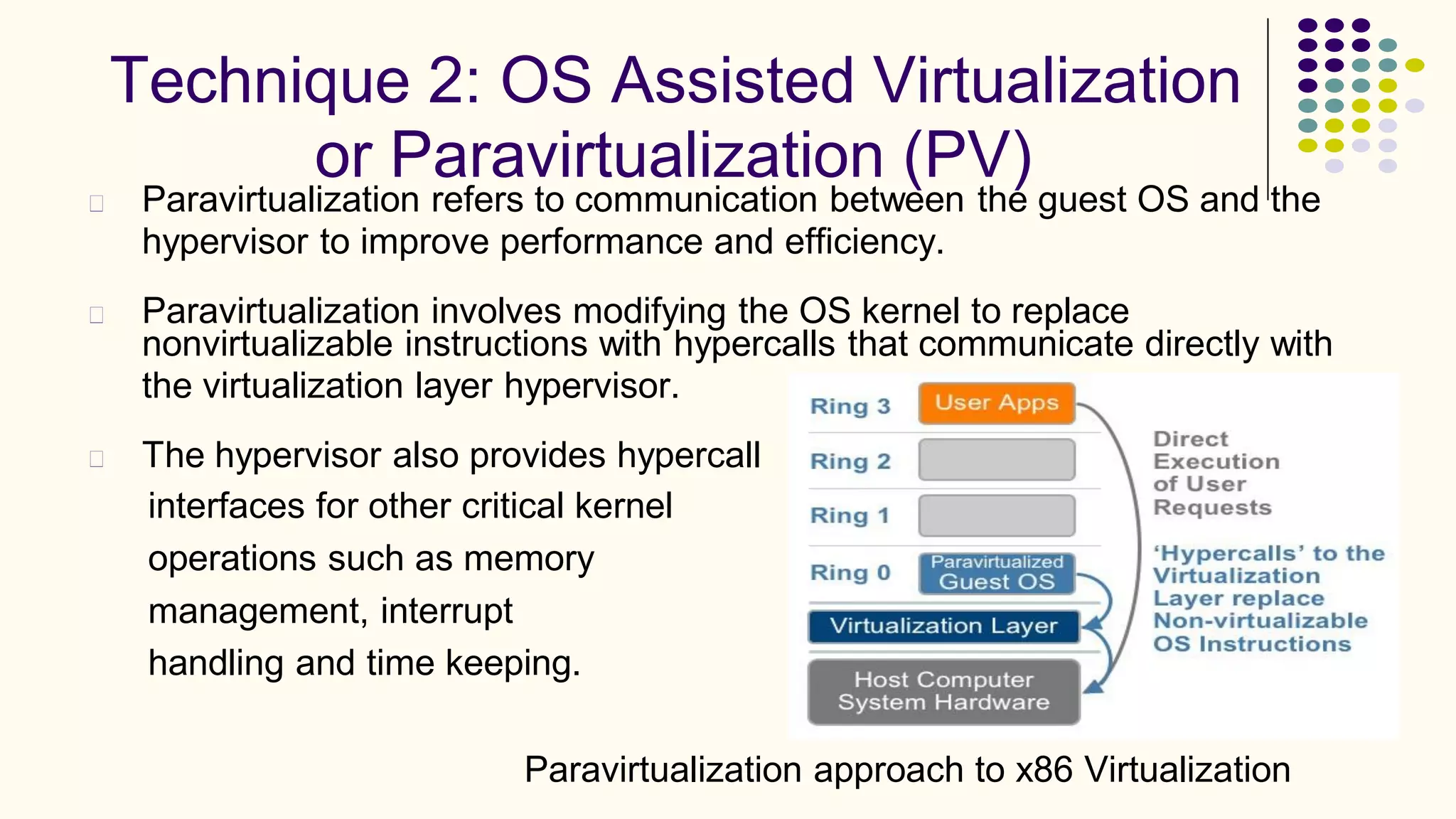
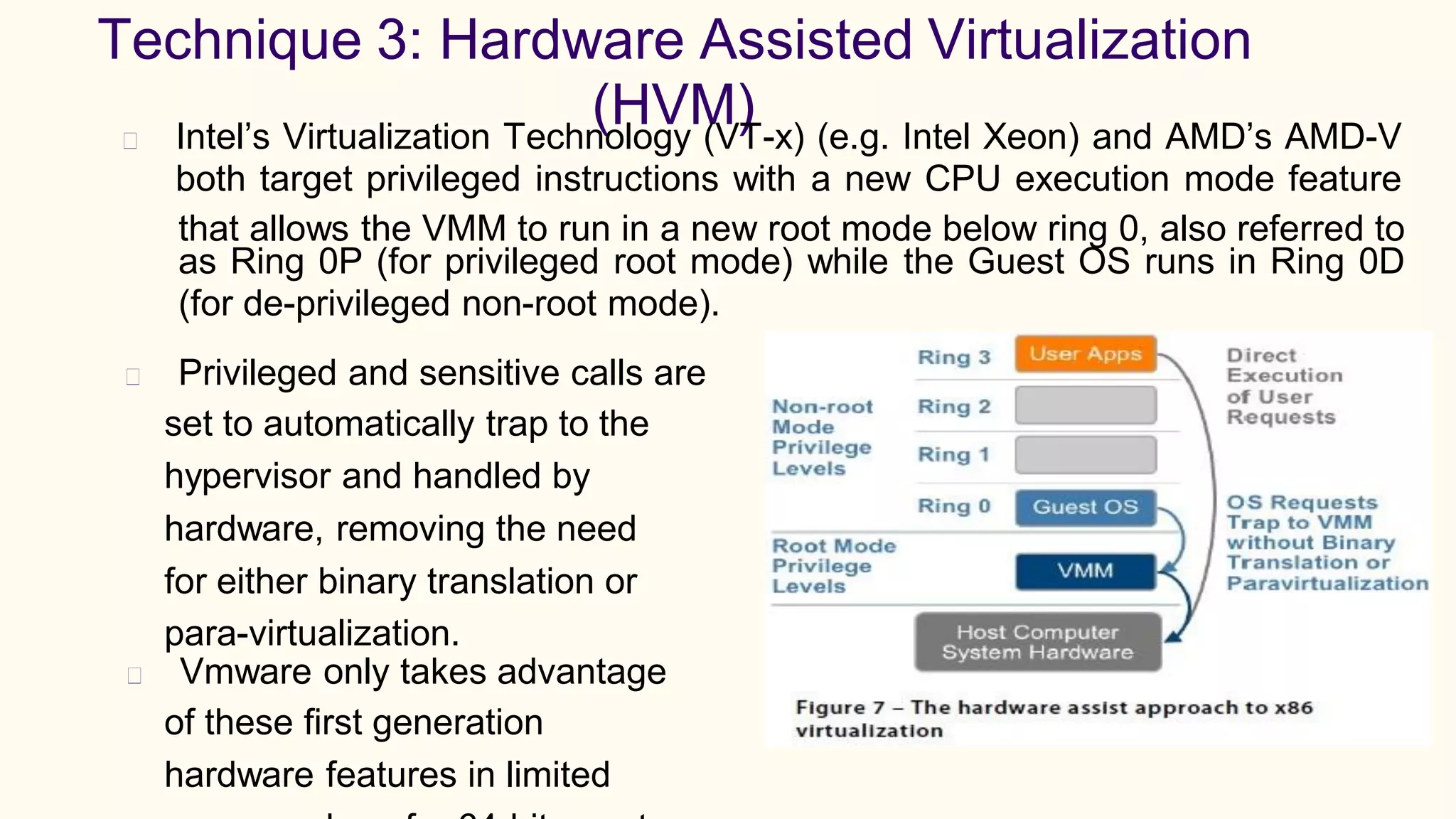
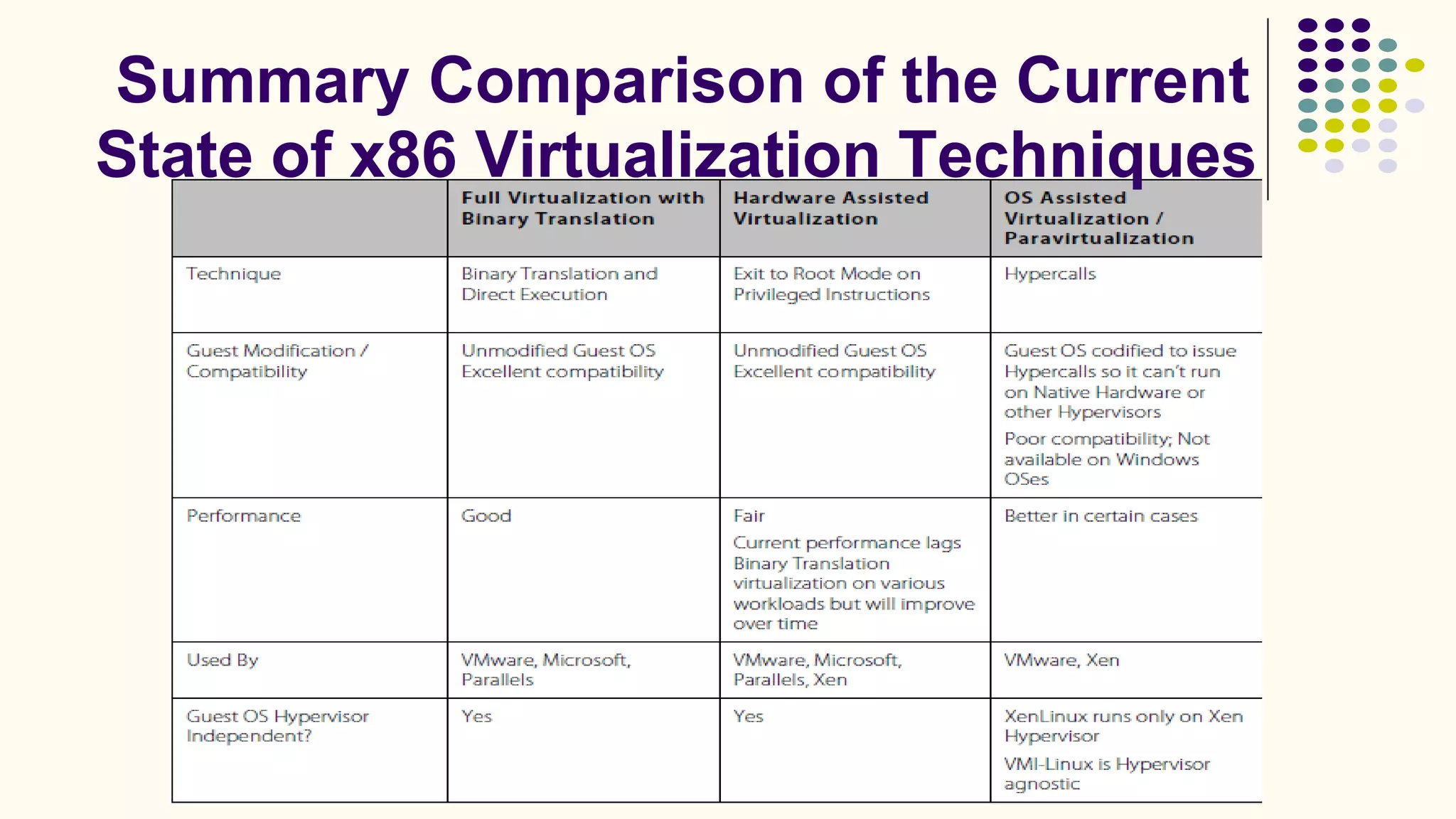
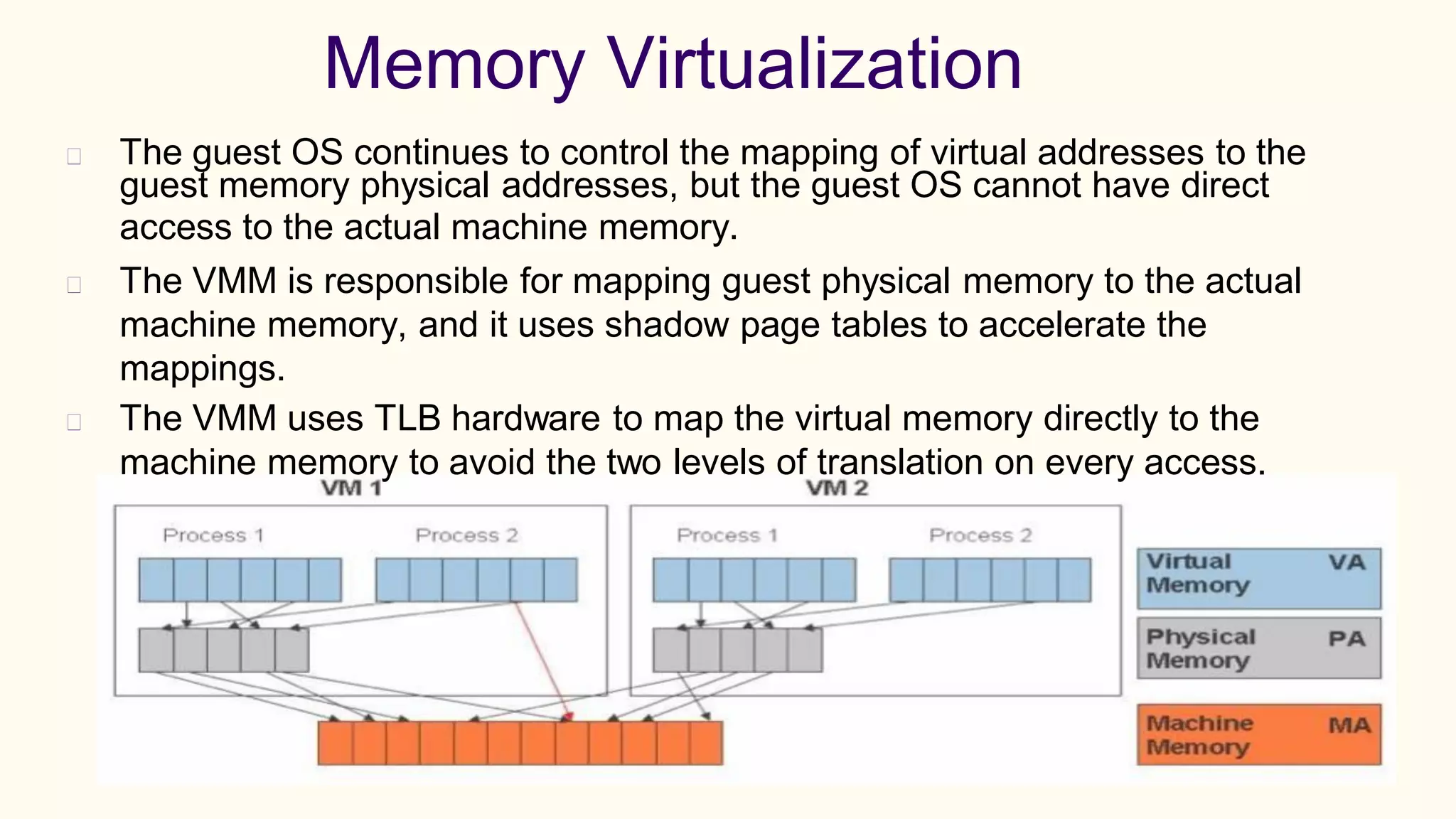
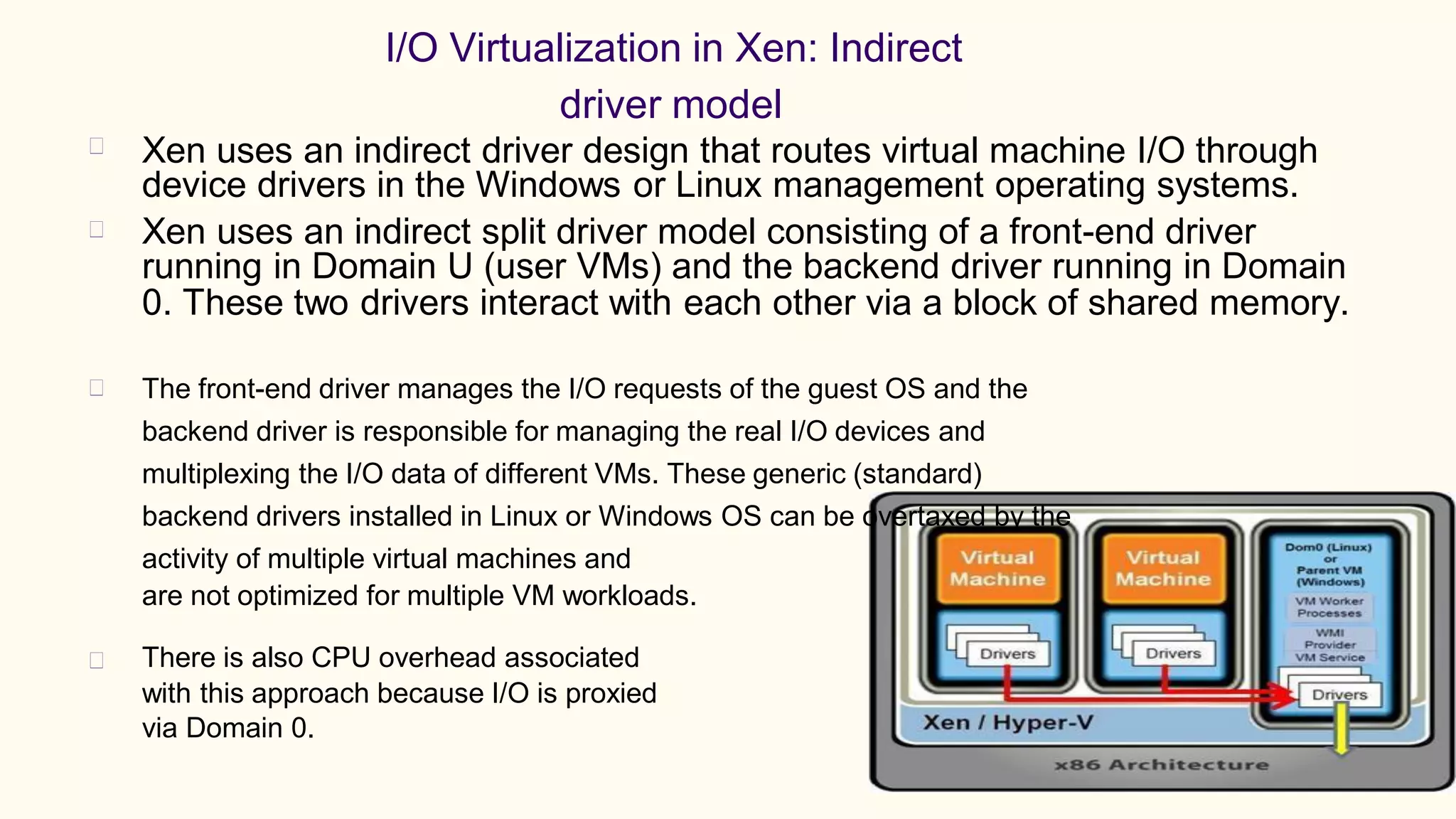
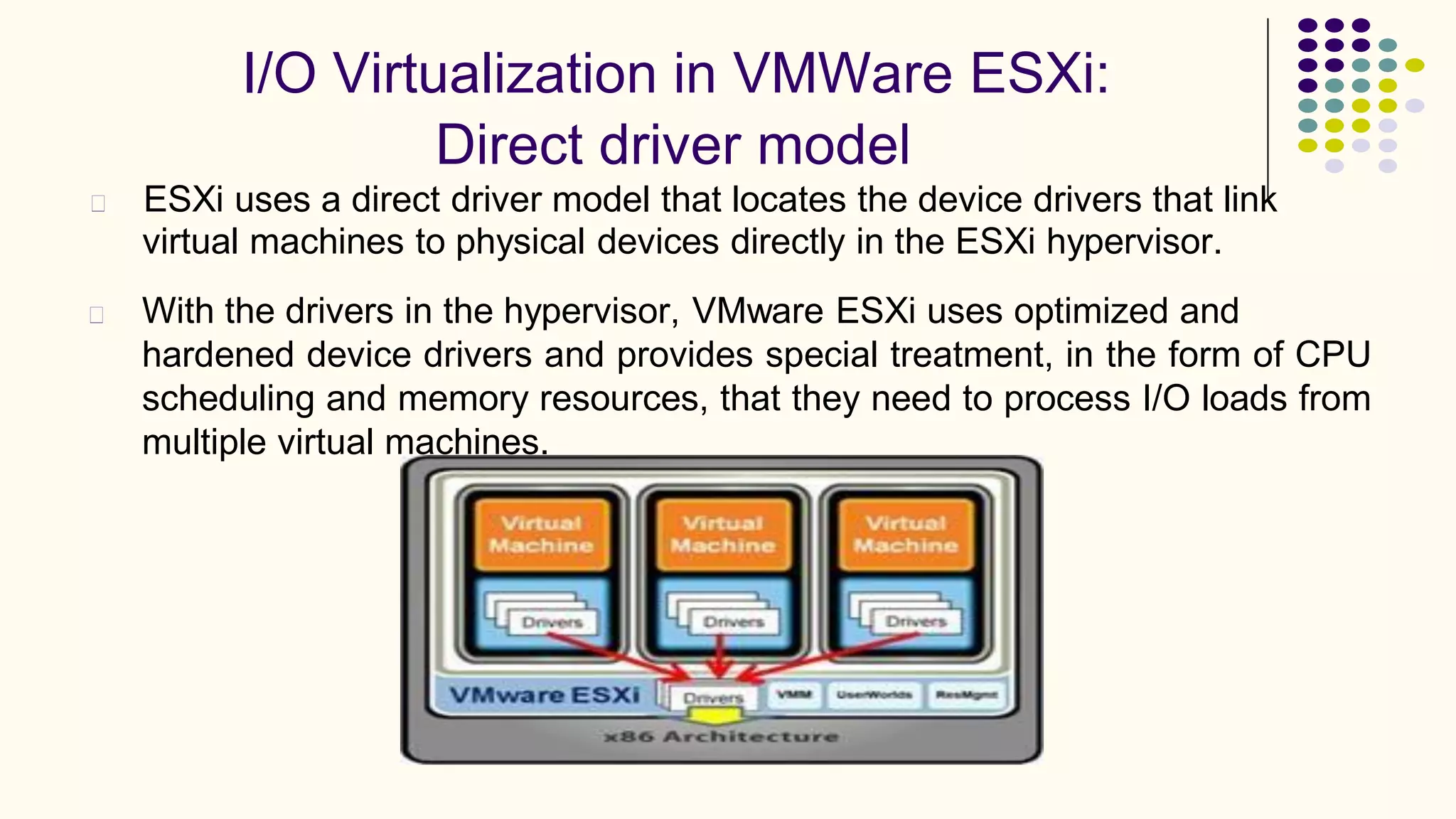
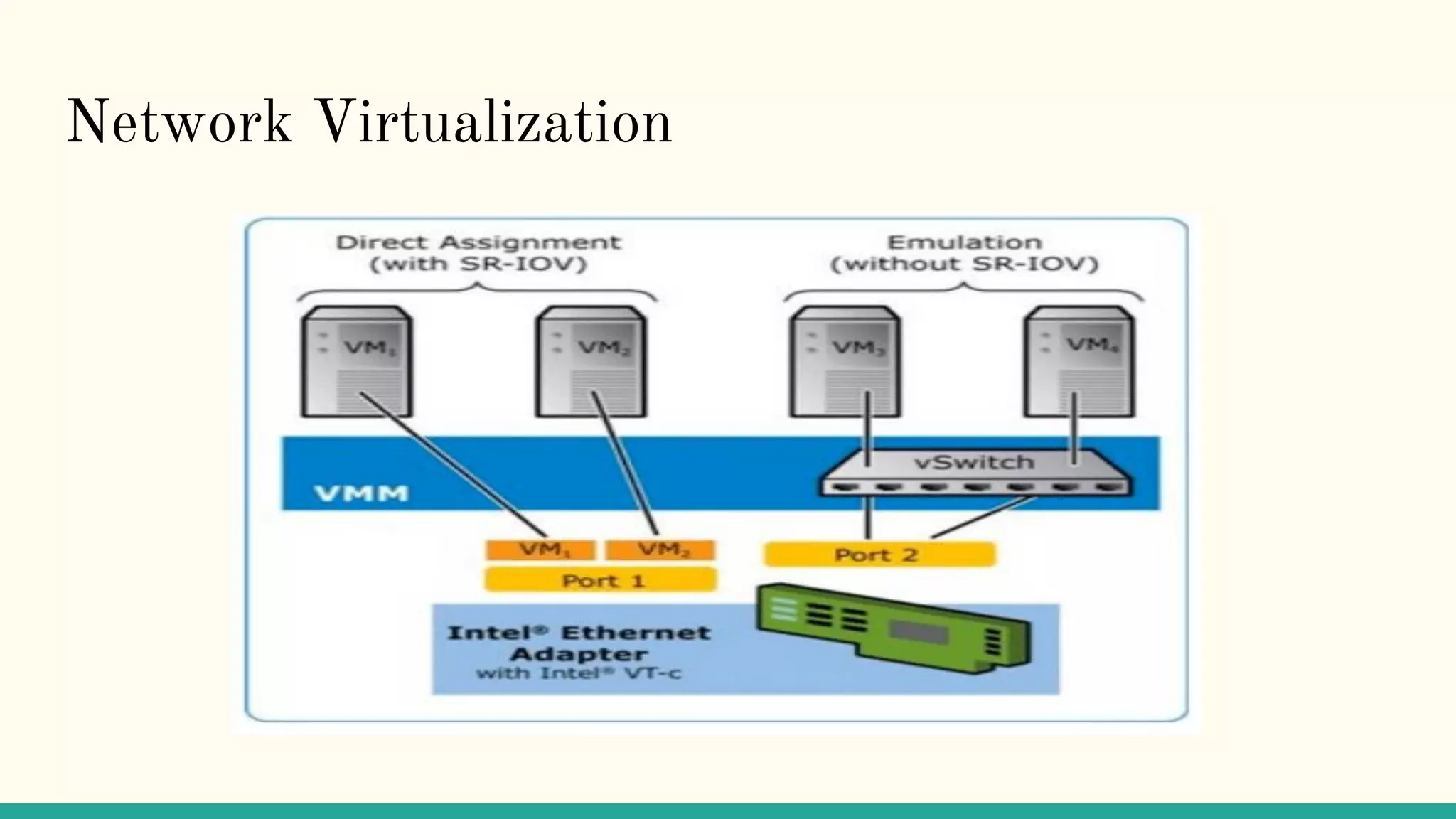
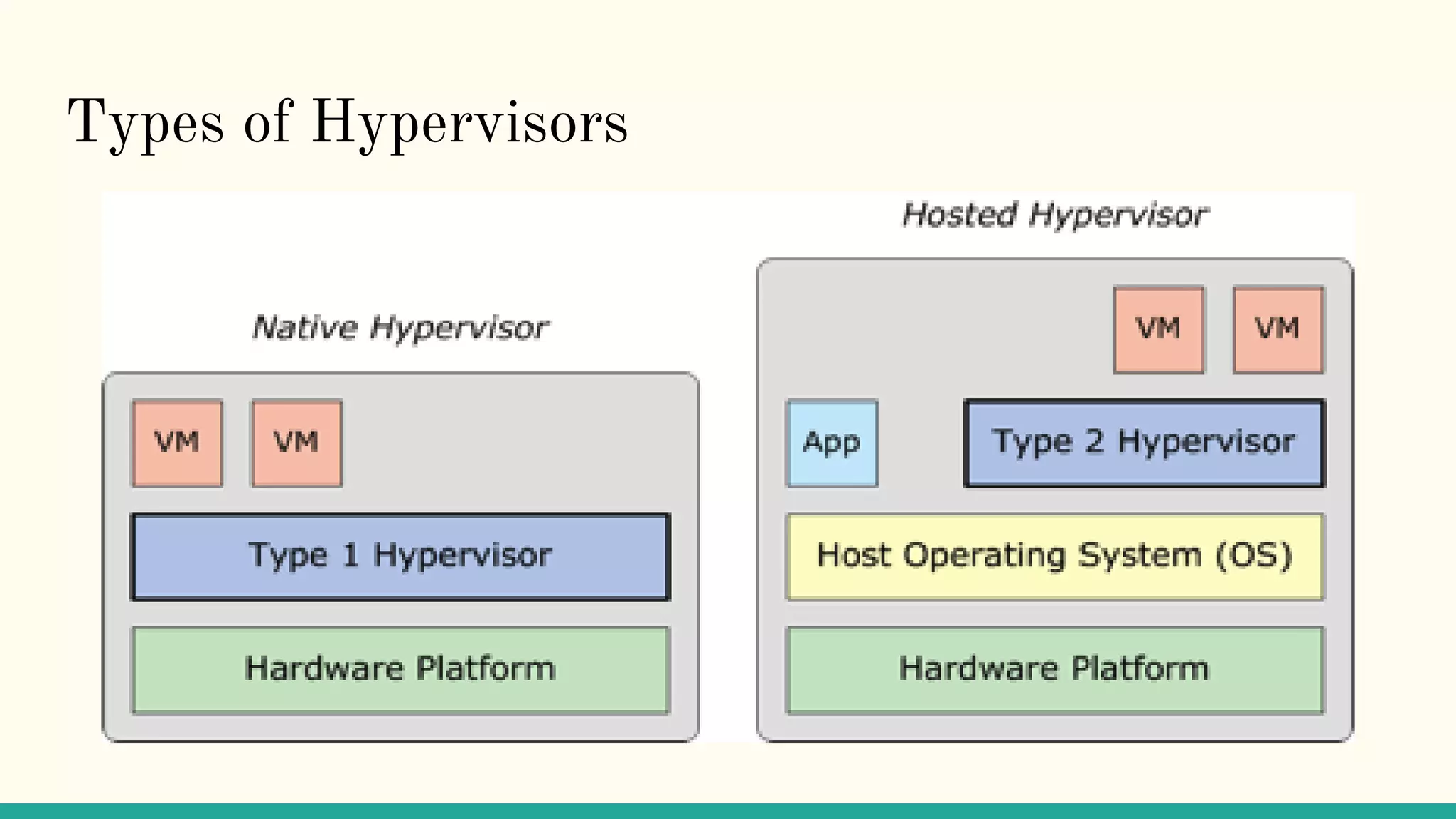
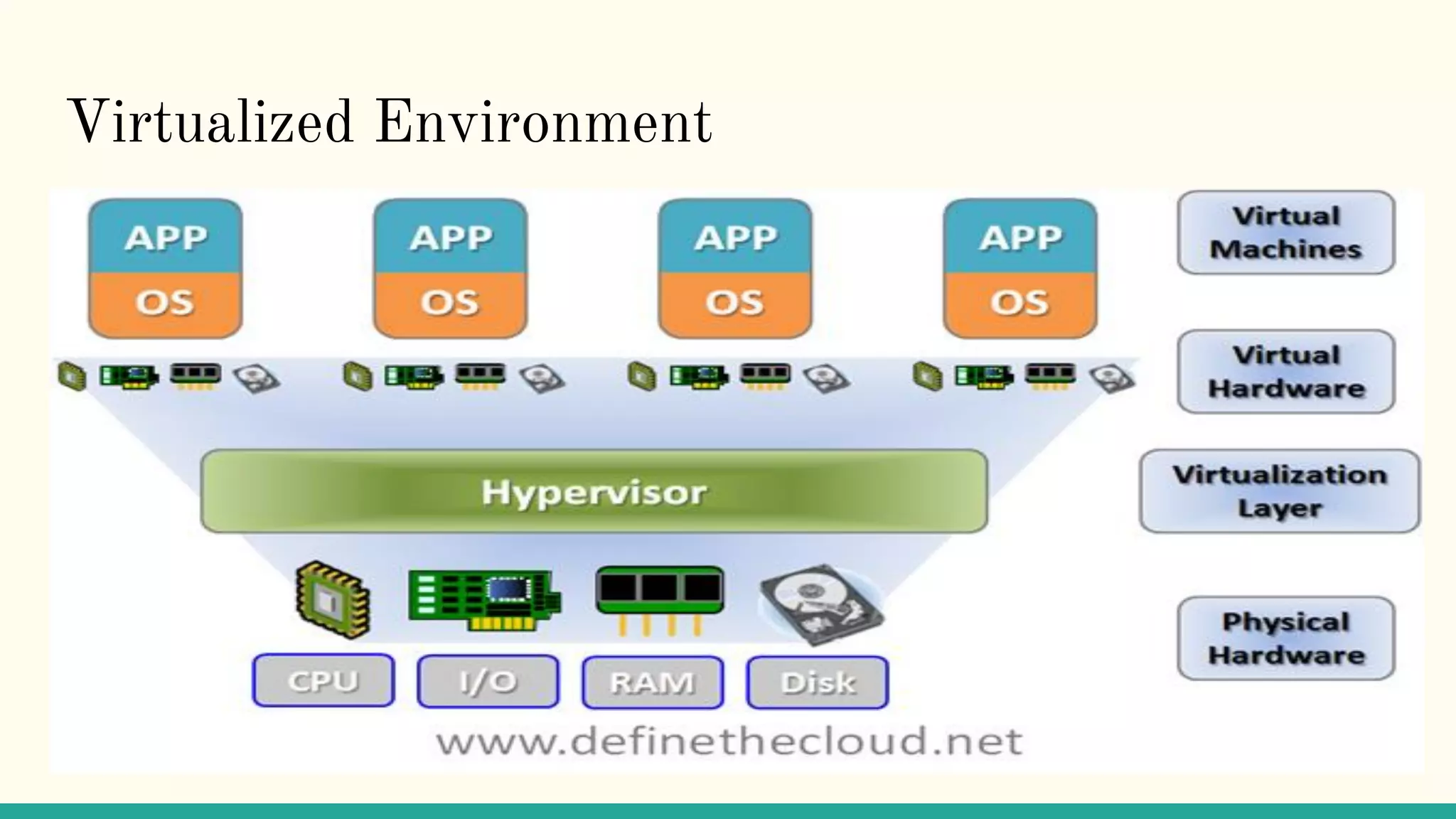
Virtualization refers to creating virtual versions of hardware platforms, operating systems, and other resources. It provides abstraction between computing resources and applications. Key terms include virtual machine, guest OS, hypervisor, and virtual machine monitor. Before virtualization, each physical machine ran one OS image, resources were underutilized, and infrastructure was inflexible. Virtualization allows multiple VMs to run on a single physical machine, improving utilization and flexibility. It virtualizes CPU, memory, I/O, networking, and other resources. CPU virtualization uses binary translation, paravirtualization, or hardware assistance. Memory virtualization maps guest physical to machine memory. I/O virtualization routes requests between virtual and physical devices. Popular virtualization