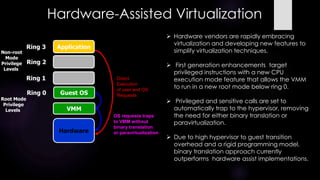
The document provides an overview of virtualization, including definitions, types of virtualization, and popular hypervisors. It discusses how virtualization addresses issues with underutilized servers in data centers by consolidating workloads. Full virtualization provides a complete hardware simulation but has challenges virtualizing certain architectures like x86. Paravirtualization modifies the guest OS, while hardware-assisted virtualization uses new CPU features to simplify virtualization. Memory, storage, network, and application virtualization are also summarized.