Embed presentation
Downloaded 1,925 times




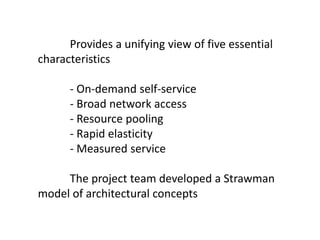

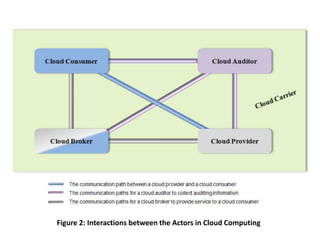
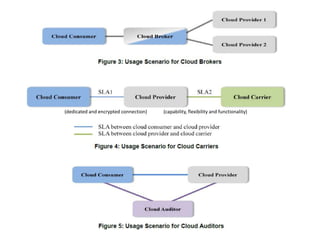
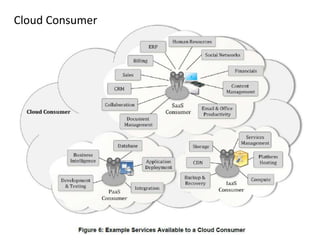
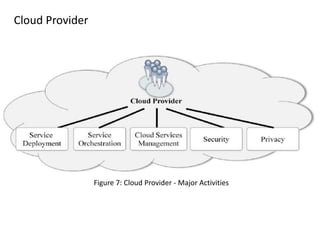

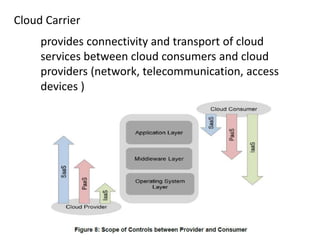
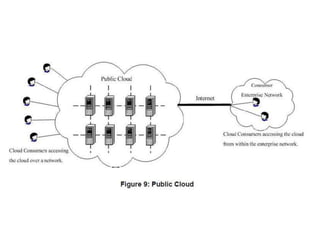
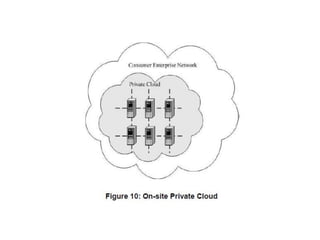
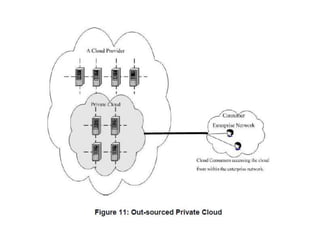
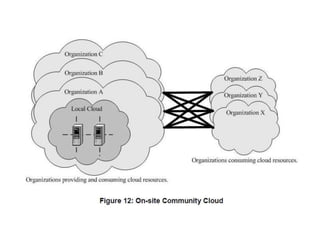
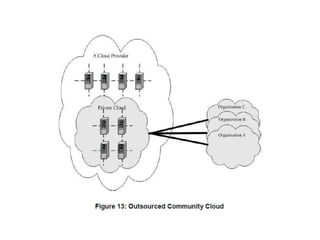
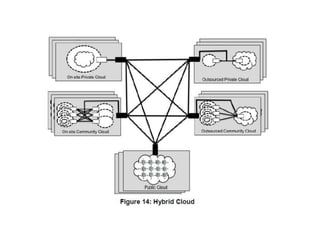
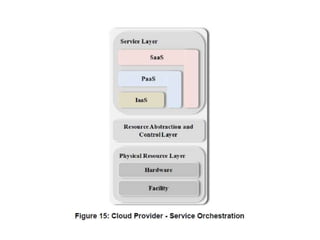
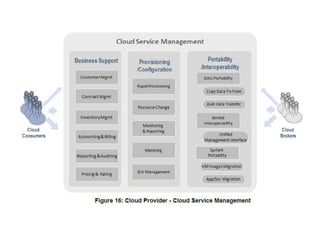
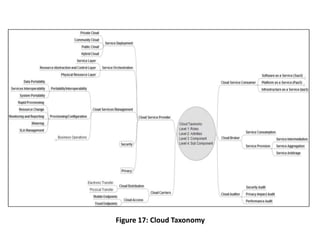

The NIST Cloud Computing Reference Architecture aims to enhance the federal government's secure adoption of cloud computing, focusing on cost reduction and service improvement. It outlines key service models (SaaS, PaaS, IaaS) and essential characteristics such as on-demand self-service and rapid elasticity. The architecture also describes roles within the cloud ecosystem, including cloud consumers, providers, auditors, brokers, and carriers.




















