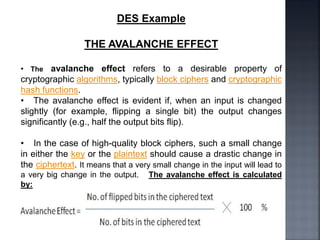
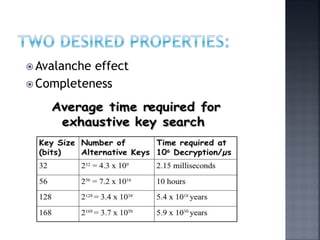
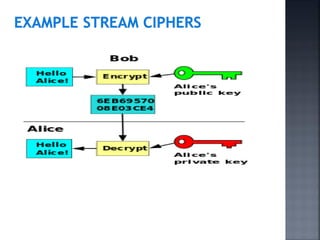
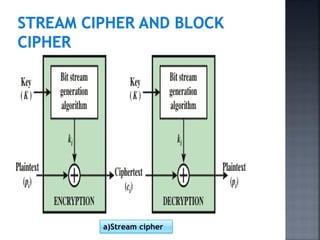
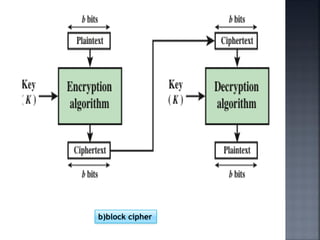
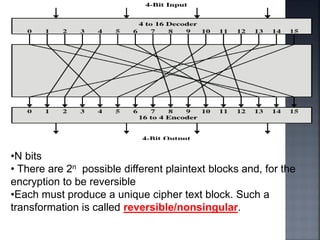
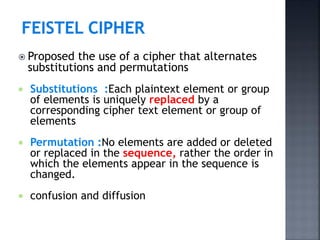
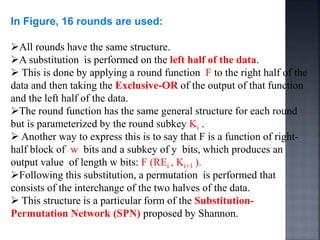
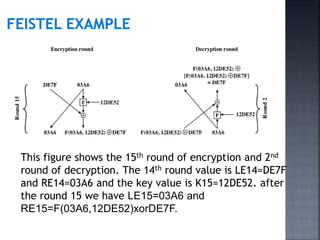
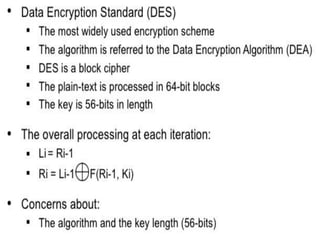
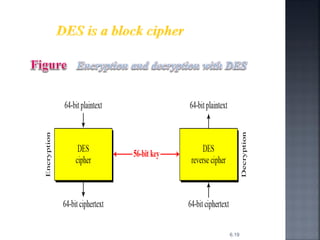
This document discusses stream ciphers and block ciphers. It provides examples of stream ciphers like the Auto keyed Vigenère cipher and Vernam cipher. It explains that in a stream cipher, each plaintext digit is encrypted individually with the corresponding digit from a pseudorandom key stream. The document also discusses block ciphers, noting that they treat blocks of plaintext as a whole and produce cipher text blocks of equal length. It provides details on the DES algorithm, including its use of Feistel networks and substitution-permutation networks.




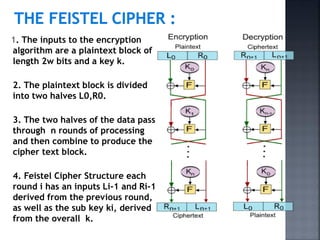


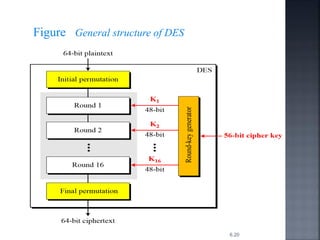

![6. Finally, the pre-output is passed through permutation [IP-1] that is
inverse of the initial permutation function, to produce the 64 bit cipher
text.
7. The right hand side portion, in which the 56 bit key is used. Initially the
key is passed through a permutation function.
8. Then for each 16 rounds, a sub key(Ki) is produced a combination of a
left circular shift and a permutation.
9.This is same for each round. But different sub key is produced because
the repeated shift of the key bits
DES Encryption Algorithm:
1. The left hand side of the figure, the plaintext proceeds in three
phases.
2.First, 64 bit plaintext passes through an initial permutation(IP)
that rearranges the bit produce the permuted input.
3. The phase consisting of sixteen rounds of the same function,
which involves both permutation and substitution functions.
4. The output of the last round consists of 64 bits that are a
function of input plaintext and a key.
5. The left & right halves of the output are swapped to produce
the pre-output.](https://image.slidesharecdn.com/pptns-190330053342/85/Network-Security-UNIT-II-22-320.jpg)