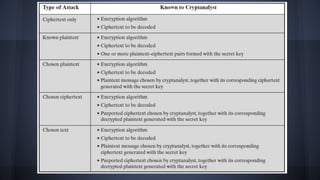
Symmetric encryption uses the same key for both encryption and decryption. It has five components: plaintext, encryption algorithm, secret key, ciphertext, and decryption algorithm. The security depends on keeping the key secret. Symmetric encryption is classified by the type of operations used, number of keys, and how plaintext is processed. Common symmetric algorithms like DES and AES encrypt plaintext in blocks using a substitution-permutation network structure.