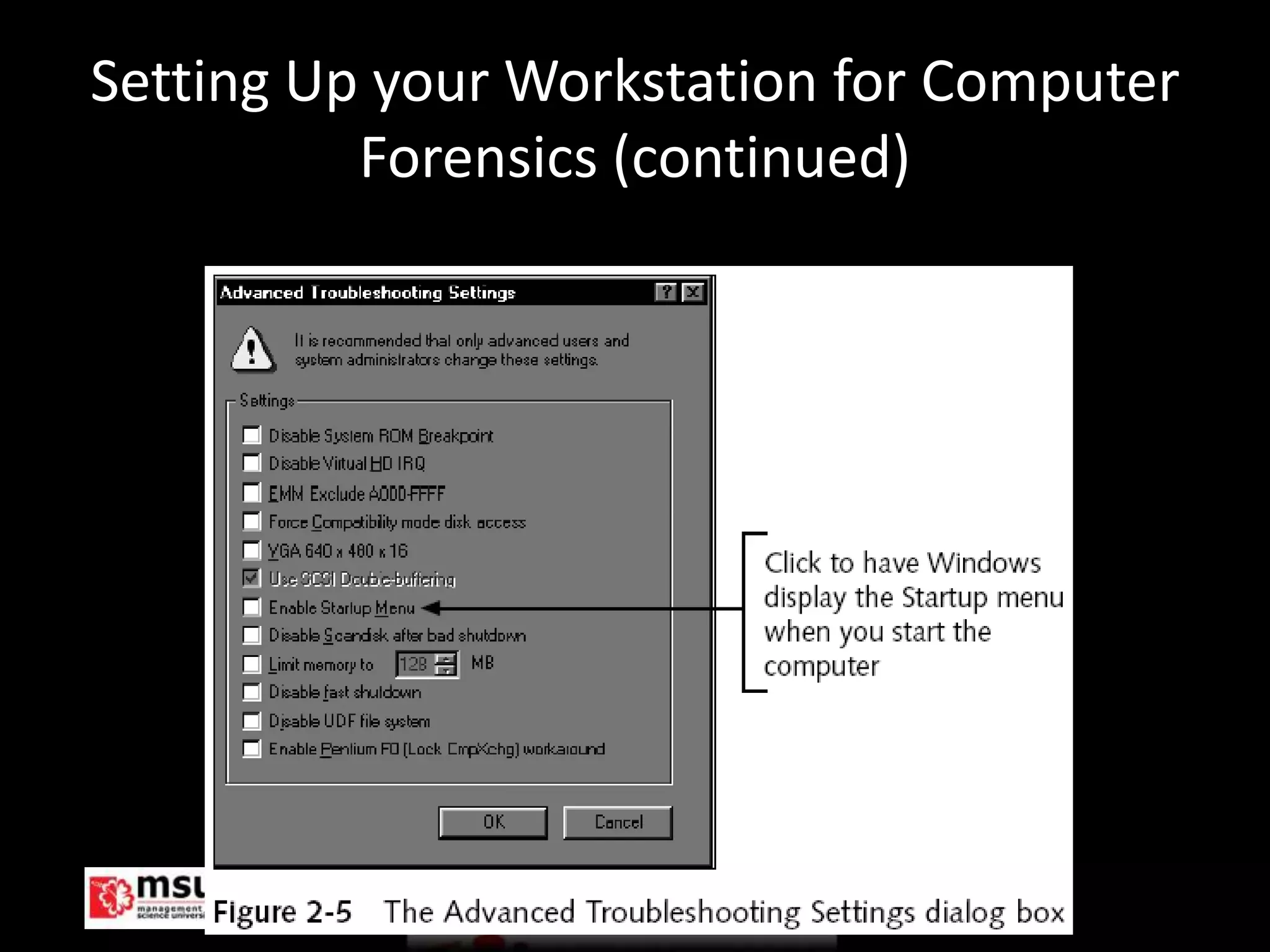
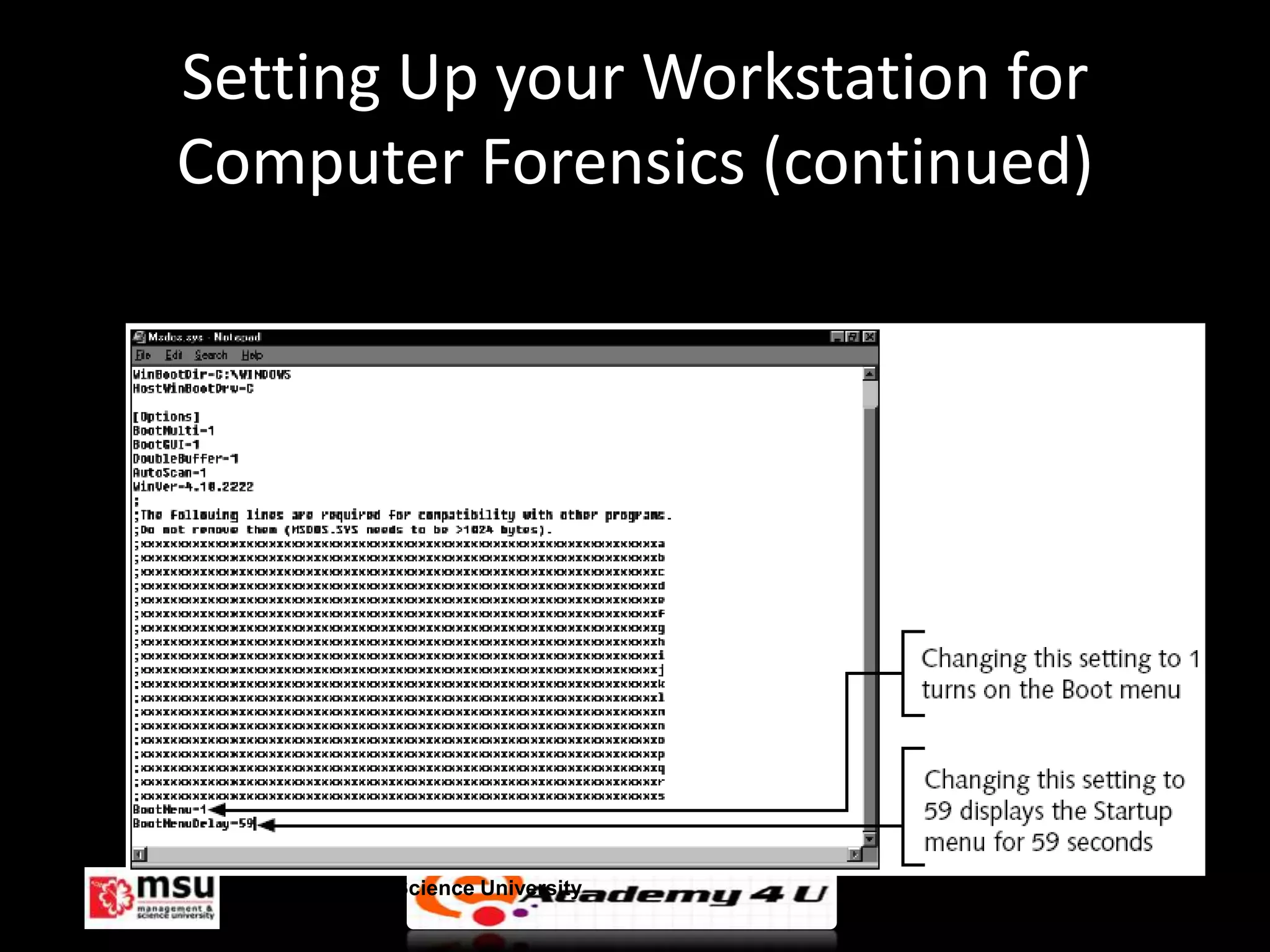
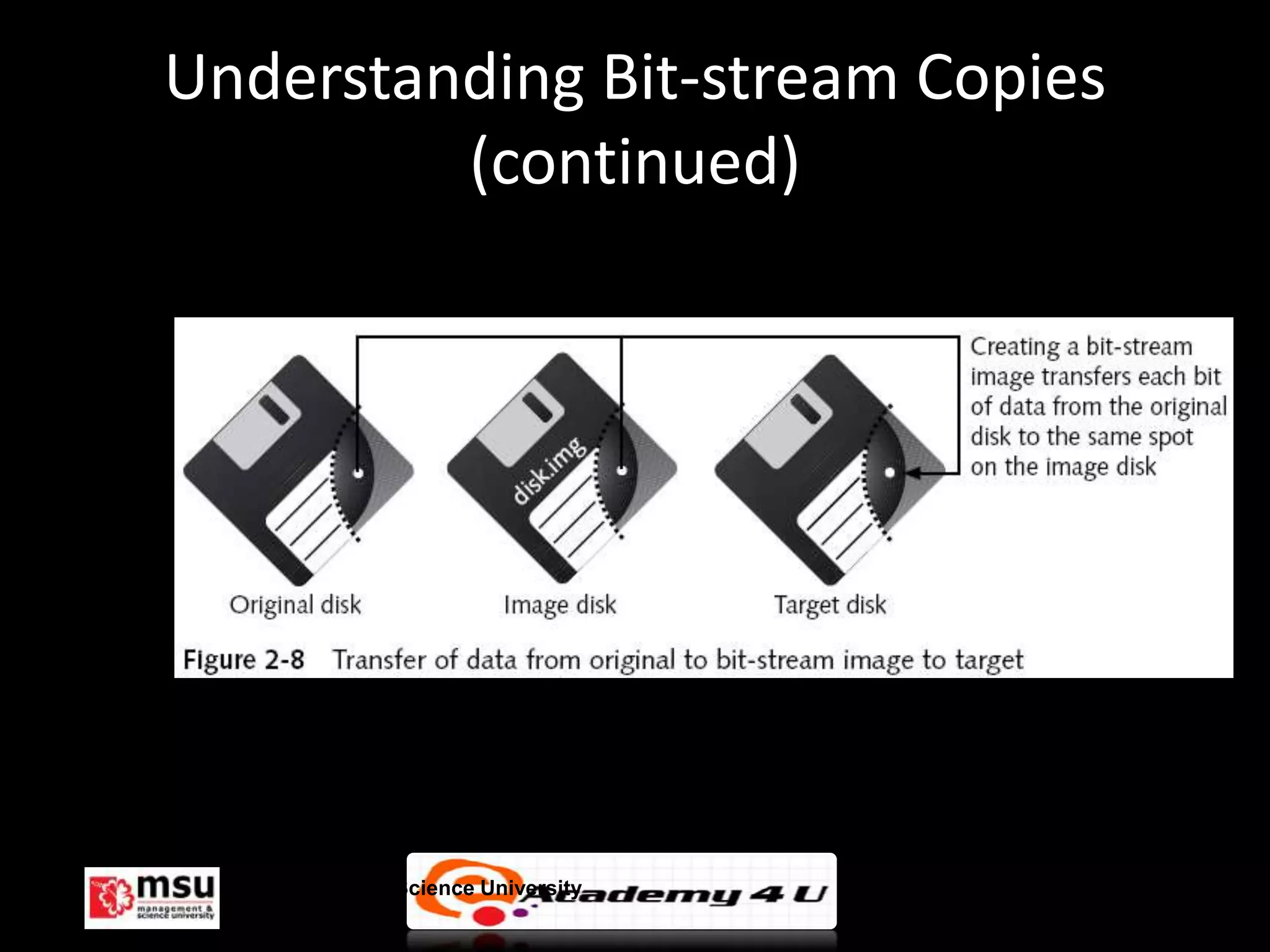
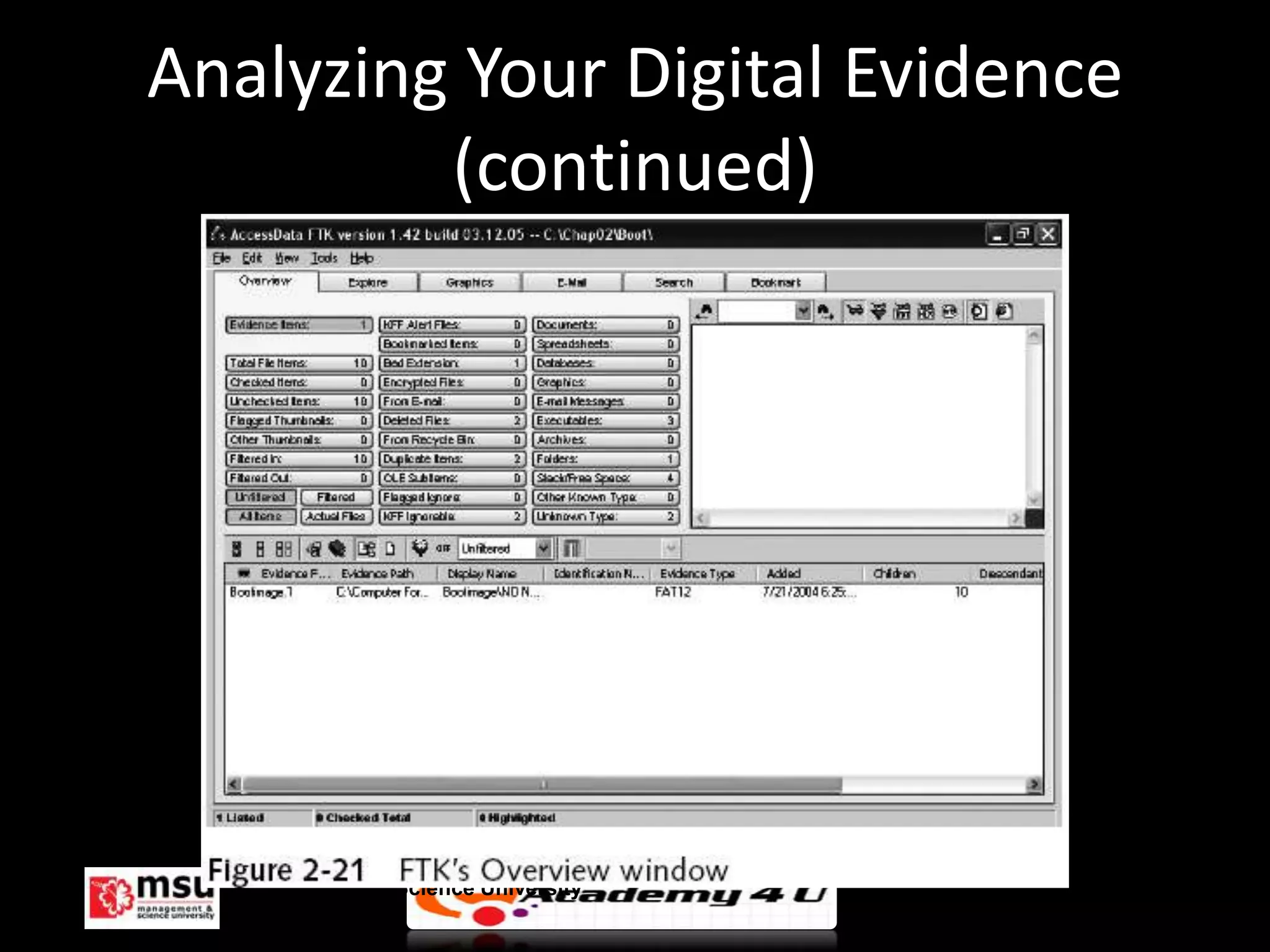
The document discusses the process of conducting a computer investigation from start to finish. It begins with preparing an investigation plan that assesses the case details and requirements. Evidence is then gathered following chain of custody procedures. Bit-stream copies are created of the original data using specialized tools to analyze the evidence without altering it. Finally, investigations are concluded by completing a case report and critiquing the process to improve future investigations.