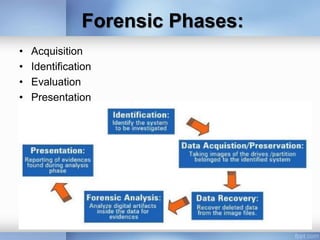
Computer forensics is a branch of digital forensic science involving the legal investigation and analysis of evidence found in computers and digital storage media. The objectives are to recover, analyze, and preserve digital evidence in a way that can be presented in a court of law, and to identify evidence and assess the identity and intent of perpetrators in a timely manner. Computer forensics techniques include acquiring, identifying, evaluating, and presenting digital evidence found in files, databases, audio/video files, websites, and other locations on computers, as well as analyzing deleted files, network activity, and detecting steganography.