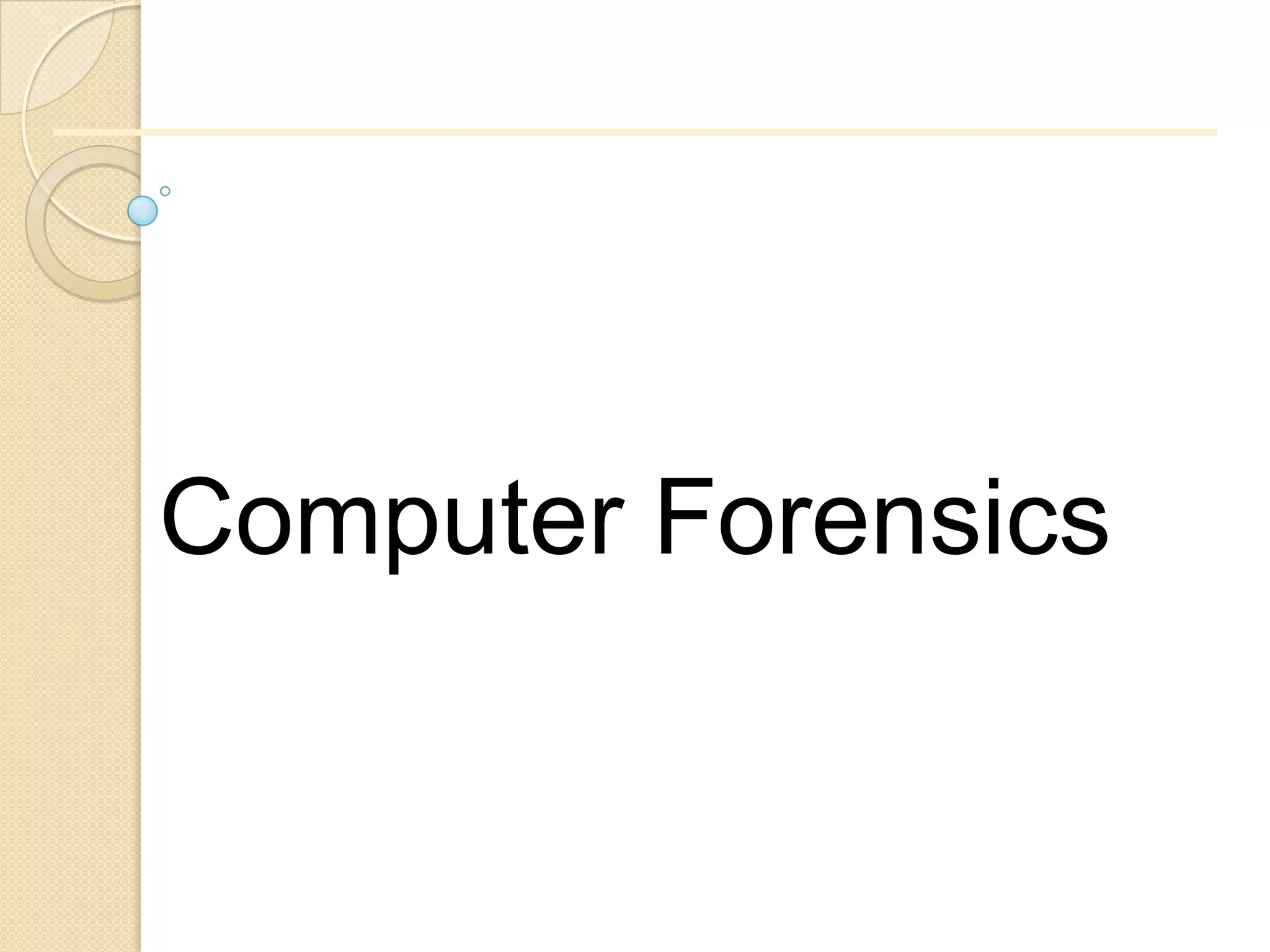
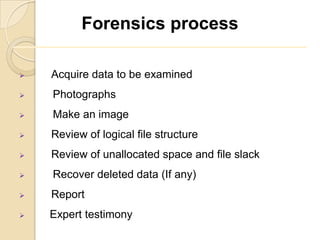
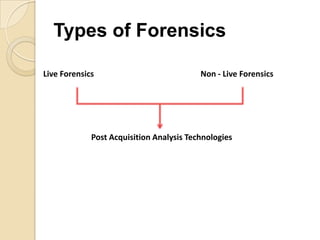
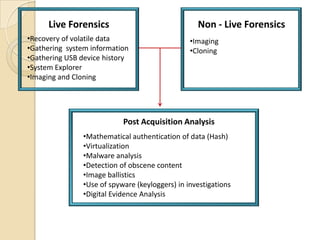
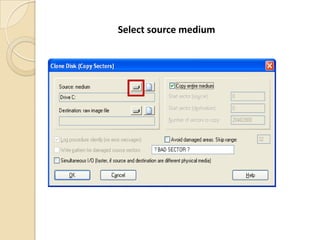
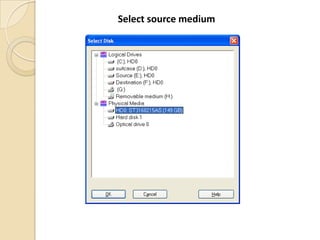
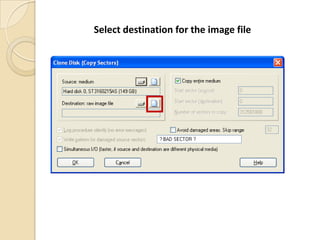
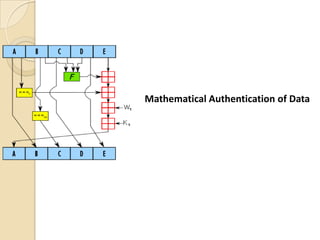
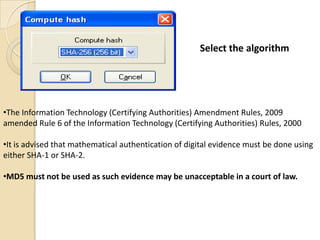
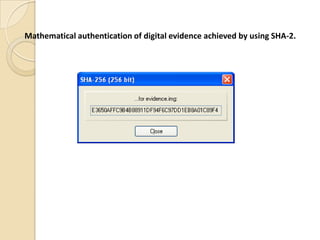
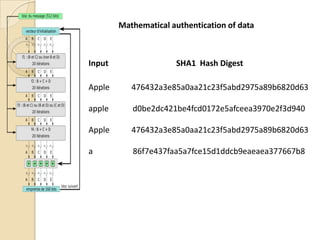
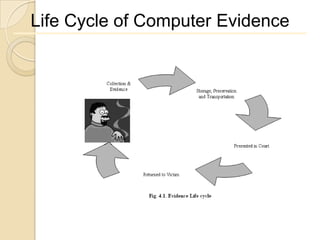
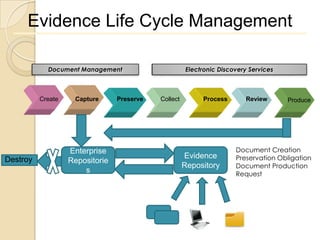
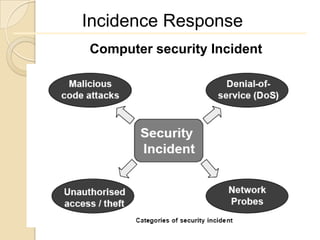
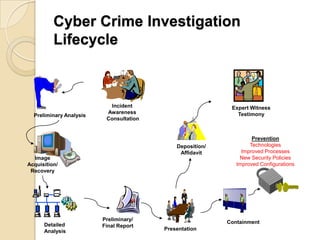
Computer forensics involves applying scientific techniques to determine legal evidence from computers and digital storage media. It includes acquiring data for examination, reviewing file structures and unallocated space to recover deleted data, and reporting findings. Mathematical authentication using hash functions like SHA-1 or SHA-2 ensures data integrity. Evidence is then processed according to guidelines before being presented in court. The goal is to confirm or dispel incidents, establish proper evidence handling, and minimize future risks.