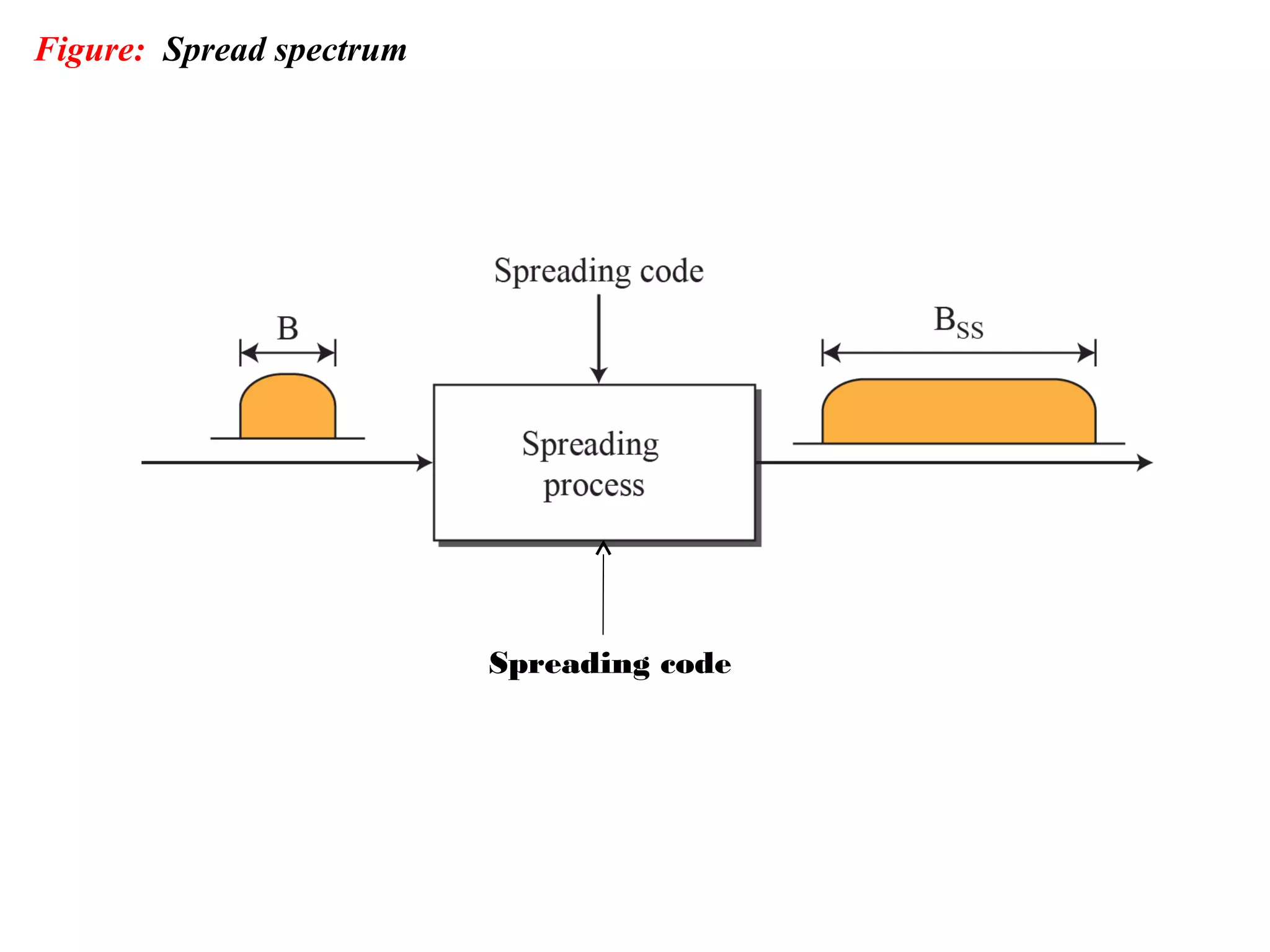
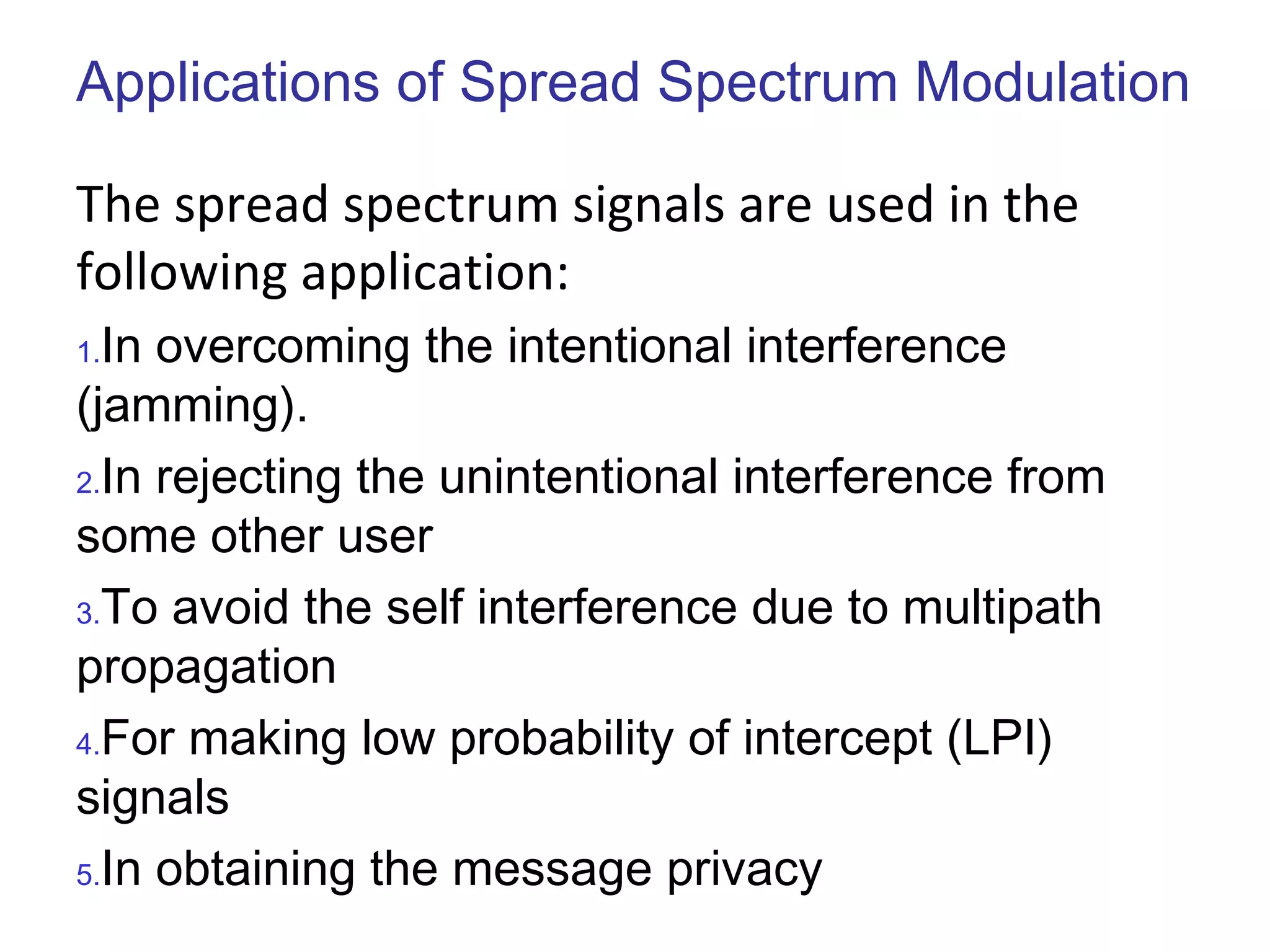
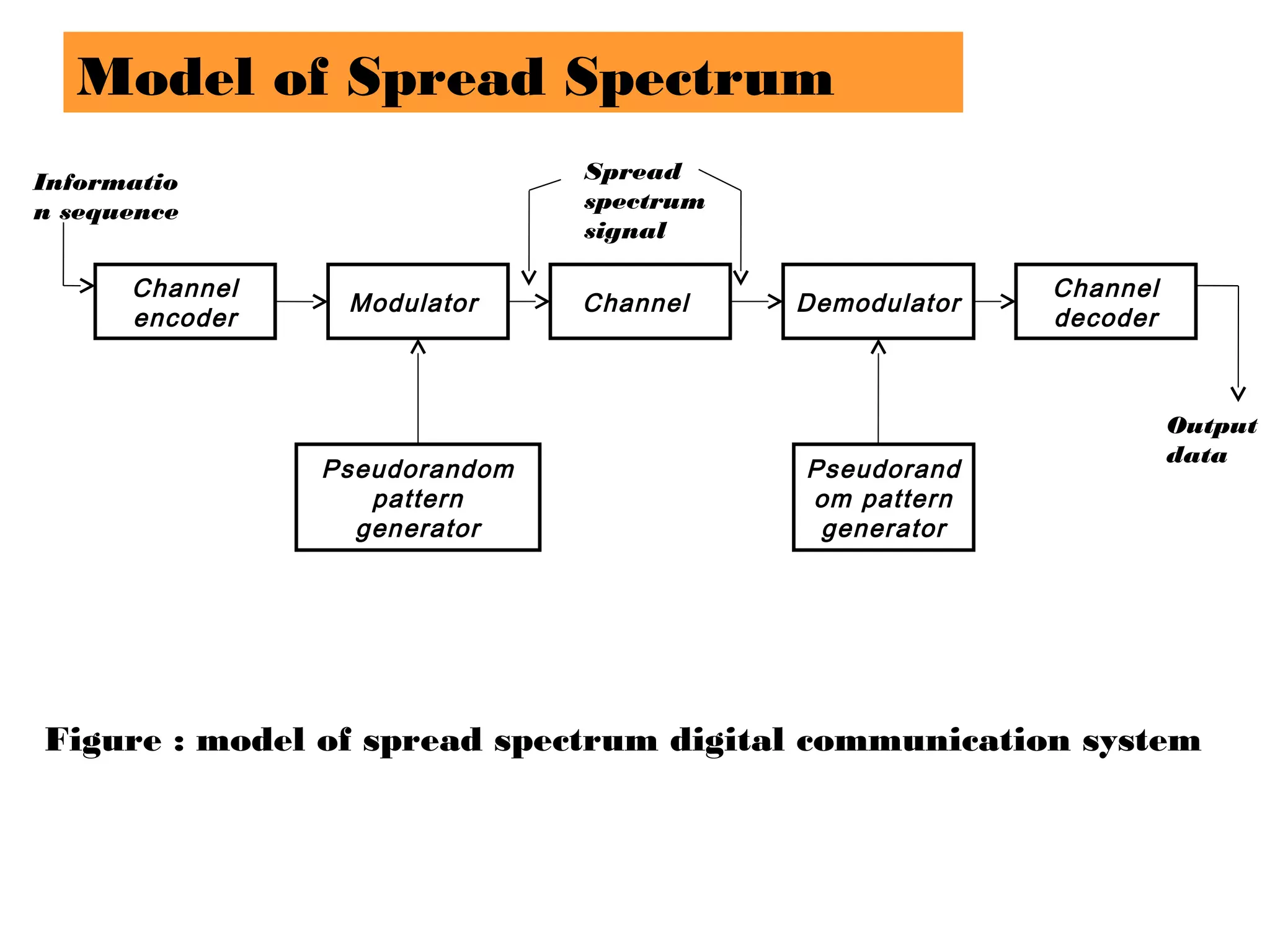
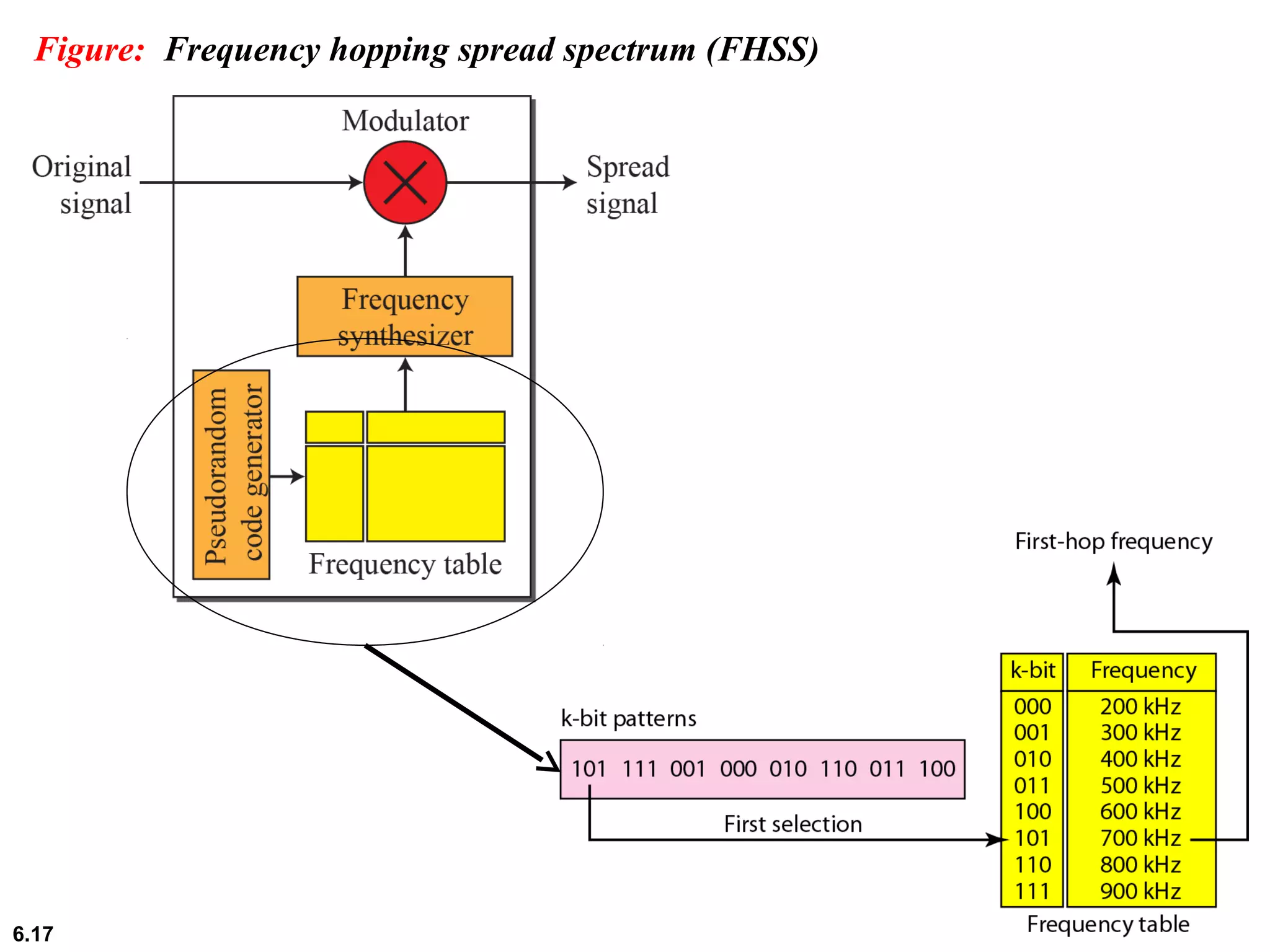
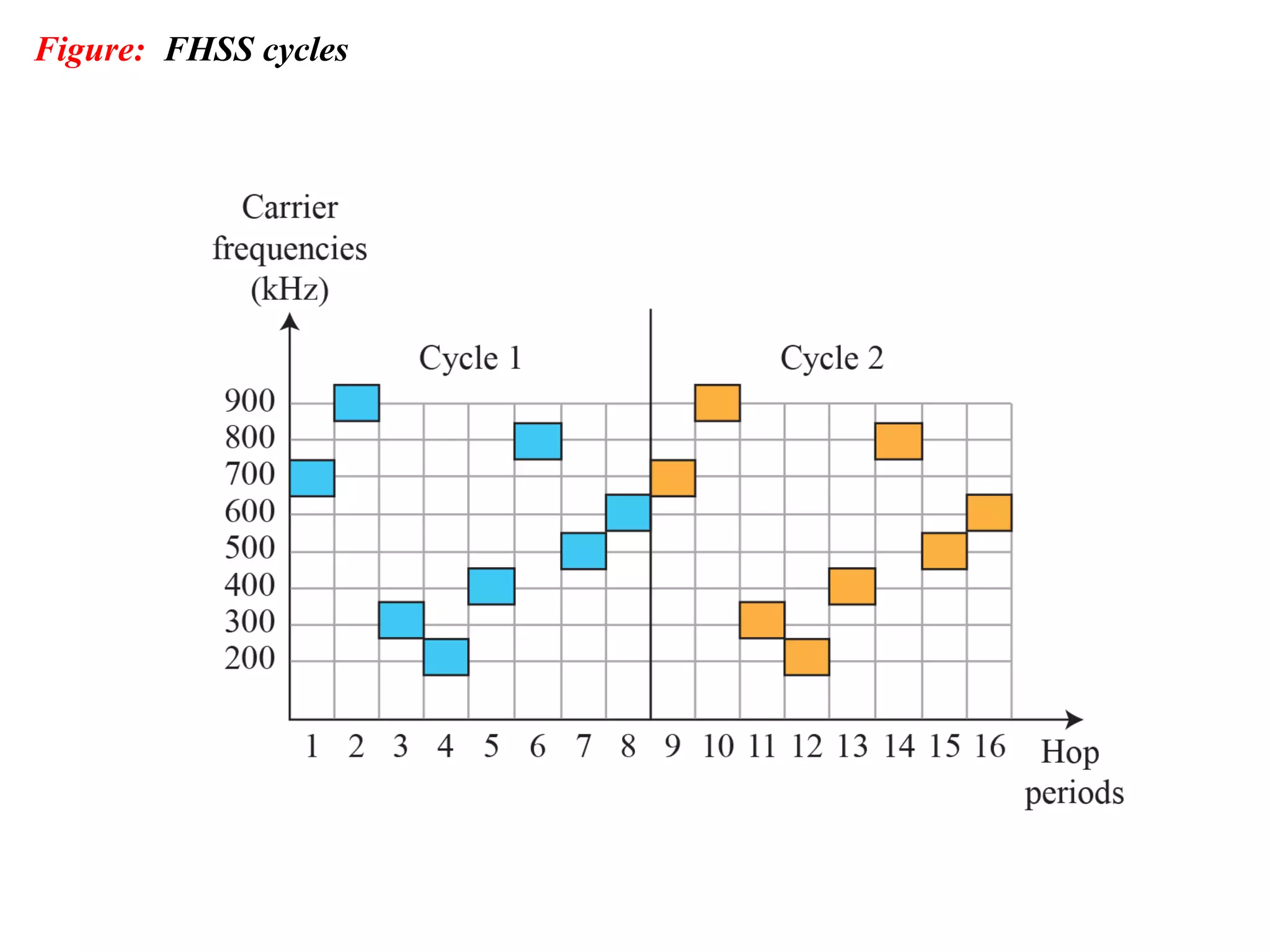
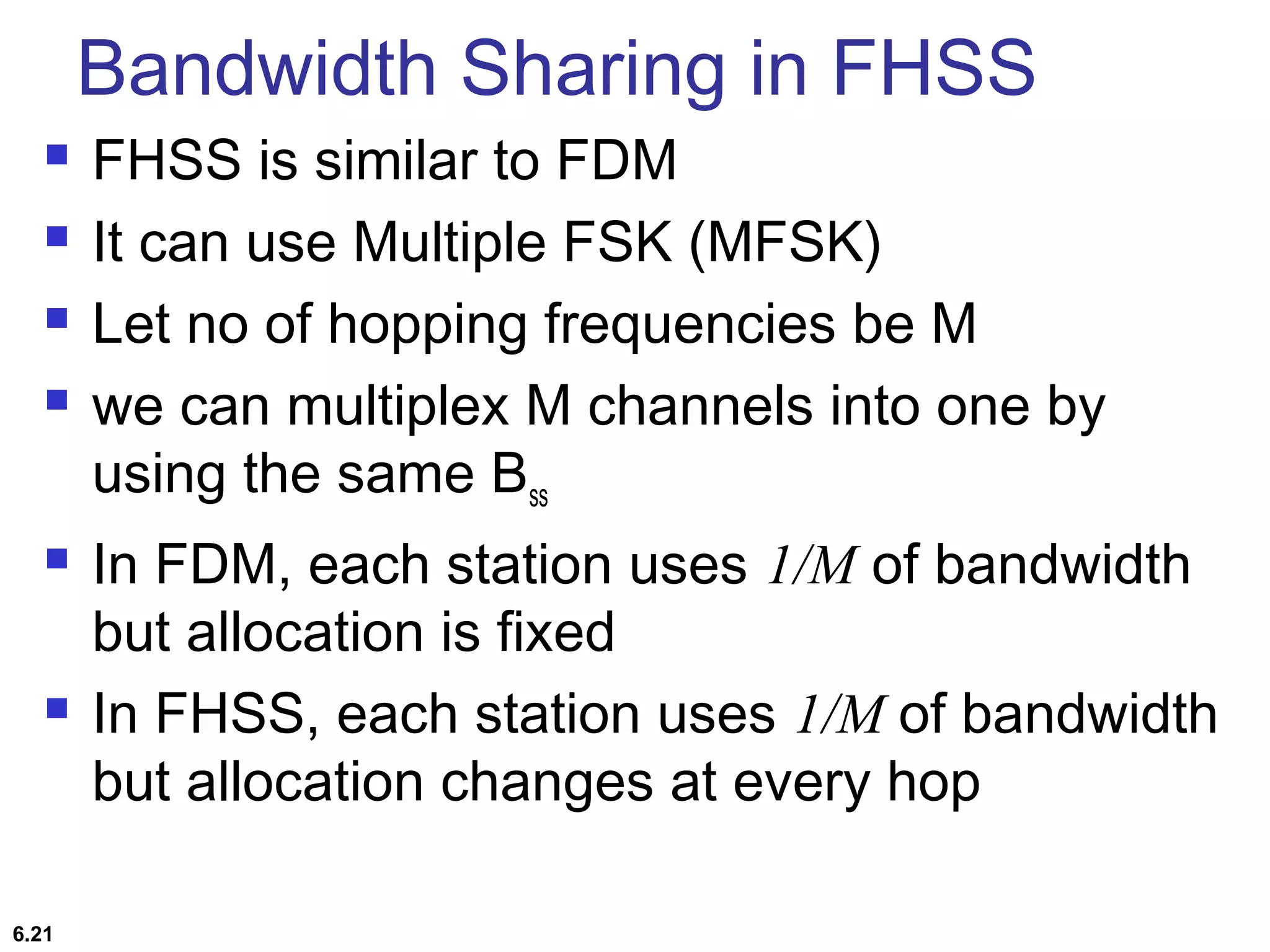
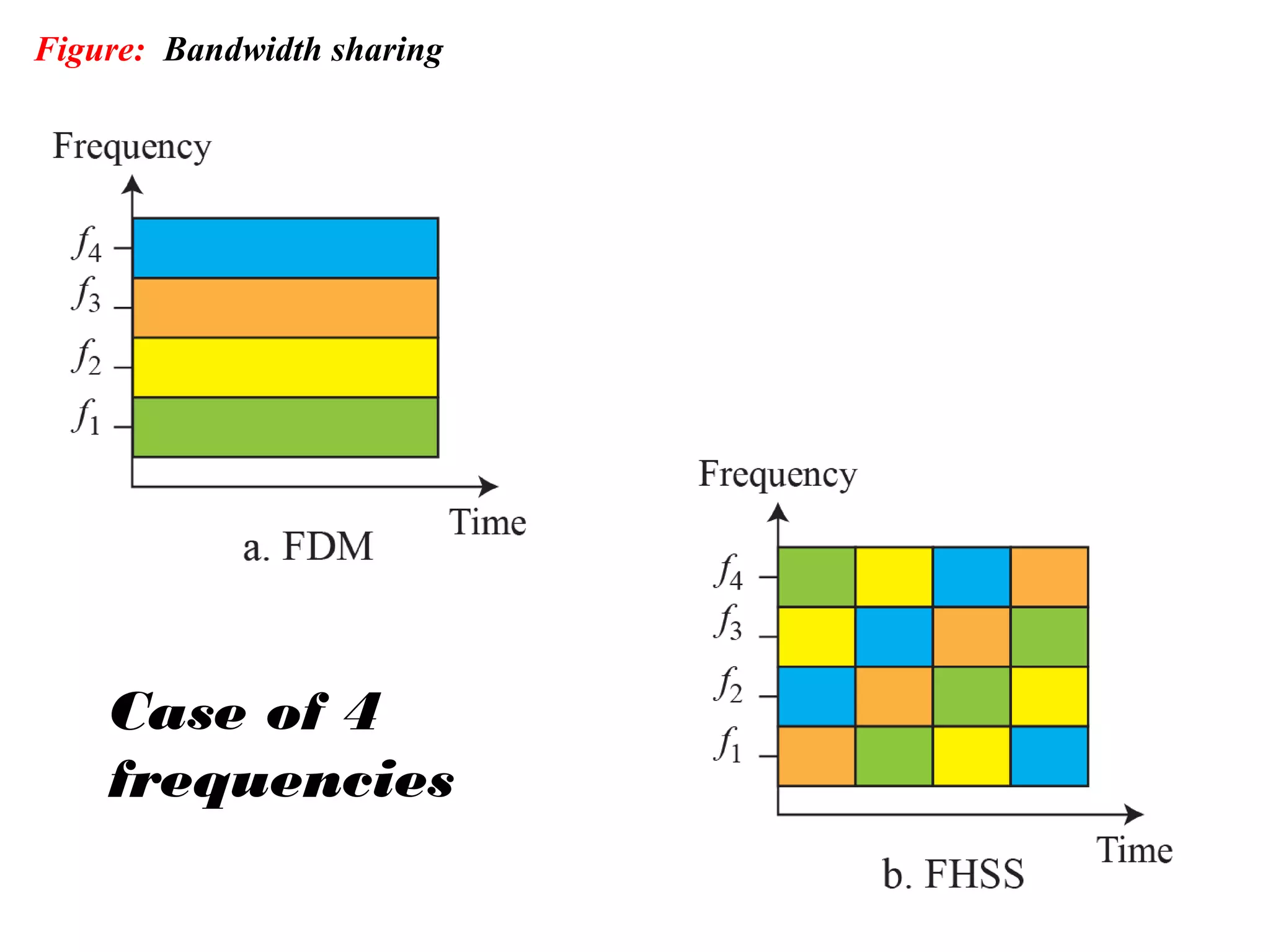
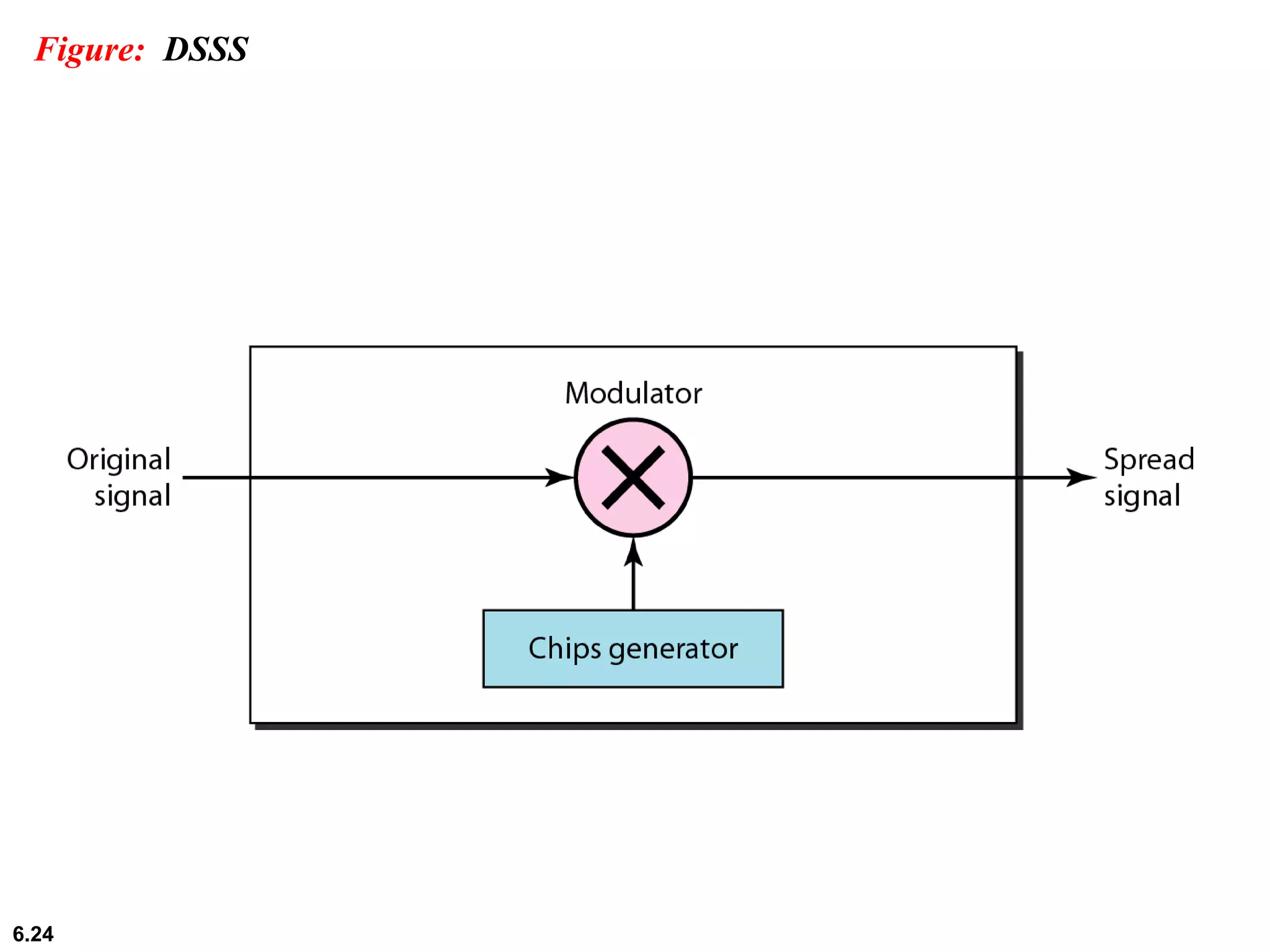
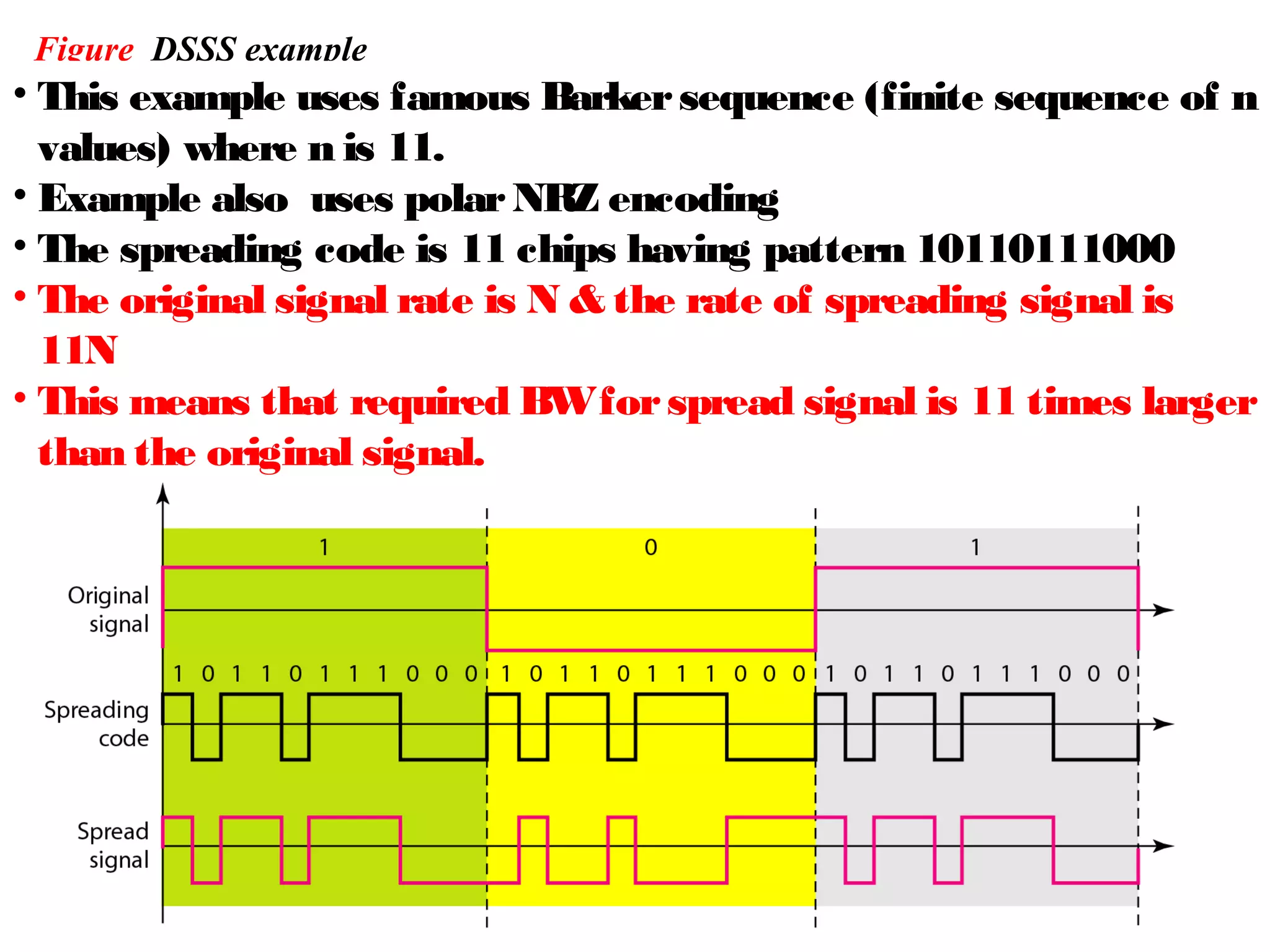
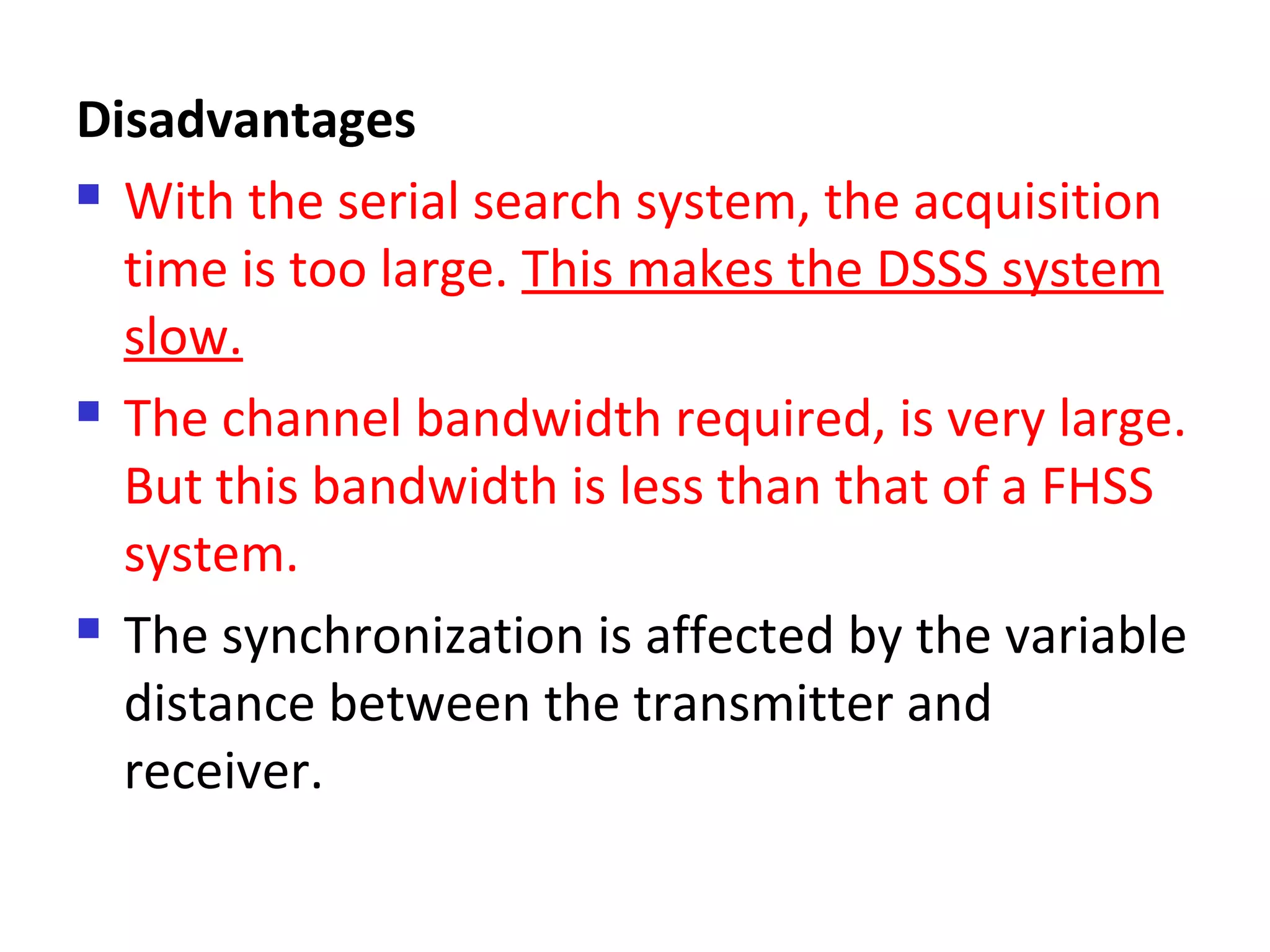
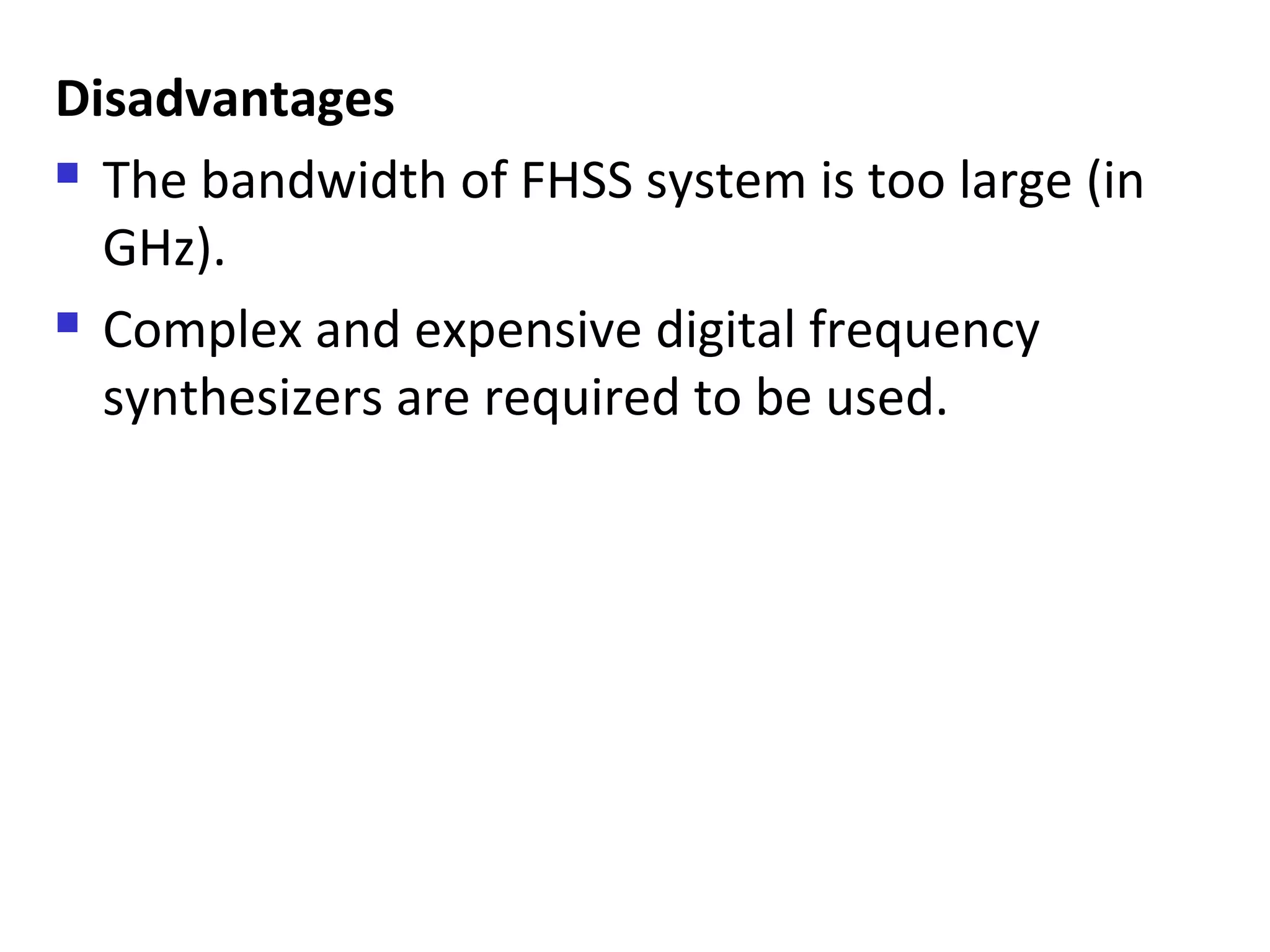
This document provides an overview of spread spectrum techniques in wireless communication, emphasizing their importance in achieving bandwidth efficiency and security against eavesdropping and jamming. It describes methods such as Frequency Hopping Spread Spectrum (FHSS) and Direct Sequence Spread Spectrum (DSSS), including their mechanisms, advantages, and applications. The document also discusses the role of pseudorandom pattern generators in ensuring secure and synchronized communication.