Embed presentation
Downloaded 150 times







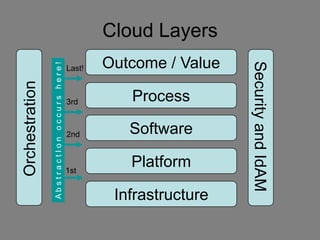

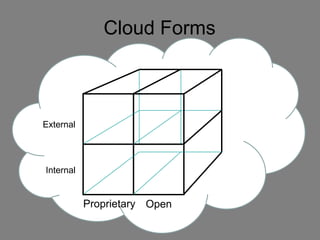
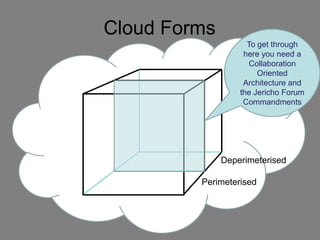
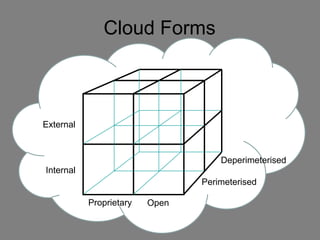
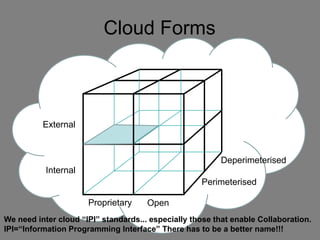
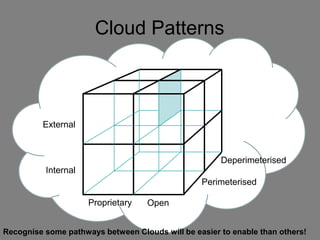
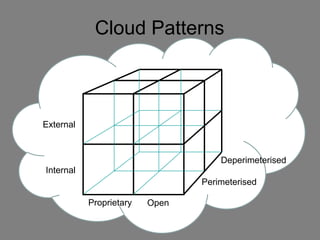

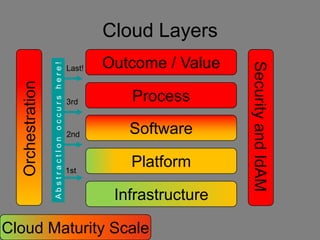



The document discusses the complexities of cloud computing, emphasizing the need for a universal data classification model and recognized trust level standards. It highlights the importance of security, data redundancy, and the various types of cloud forms that influence data management strategies. Additionally, it advocates for standardized metadata and collaboration-oriented architecture to improve cloud security and interoperability.





















