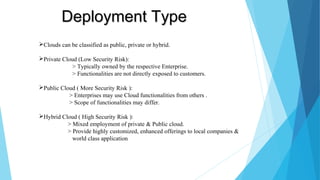
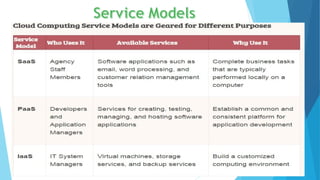
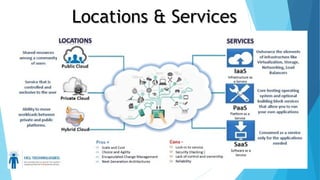
Cloud computing delivers internet-based services like servers, storage, and applications, facilitating faster and more efficient IT solutions with various deployment models: public, private, and hybrid. Security challenges include data protection, user authentication, and the risk of data breaches, alongside issues like denial of service and malicious insiders. To ensure safe practices, cloud providers should obtain certifications demonstrating sound internal controls, and users must remain cautious of the associated risks.