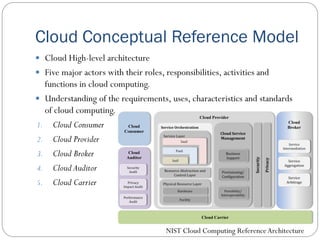
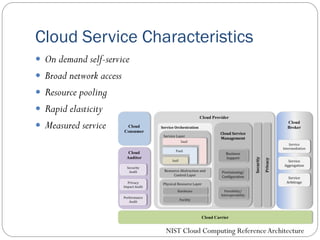
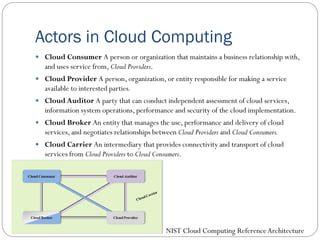
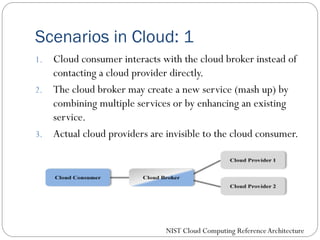
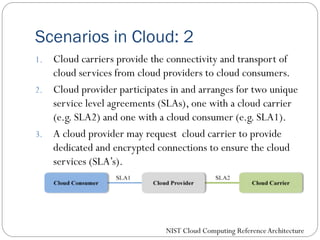
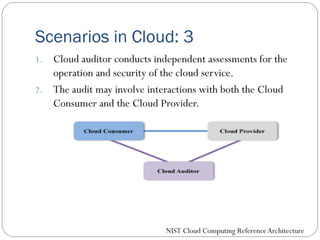
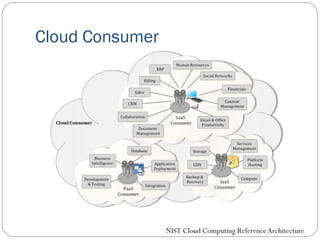
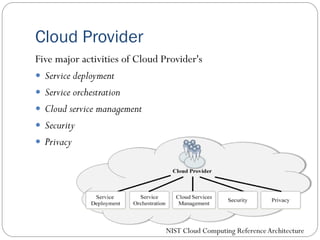
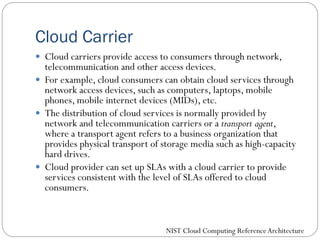
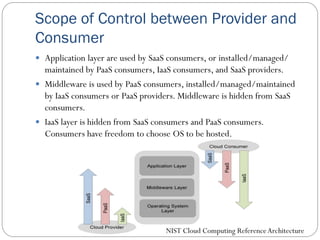
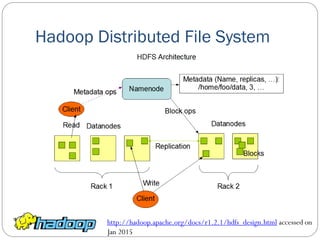
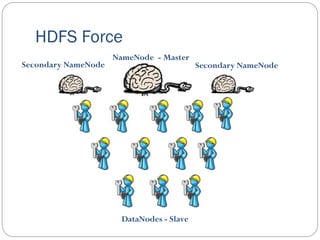
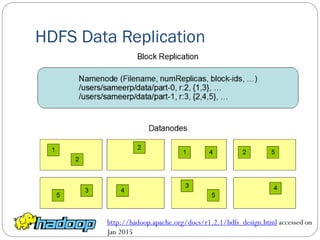
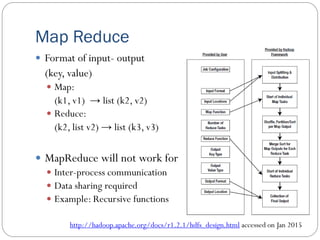
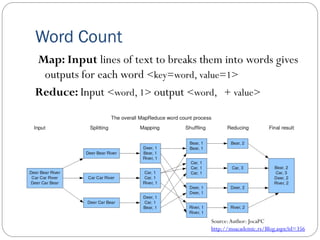
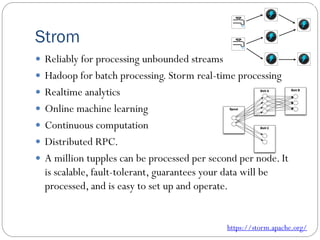
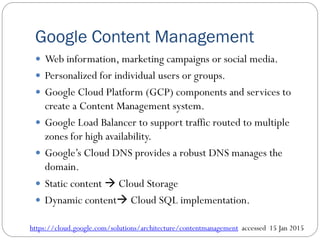
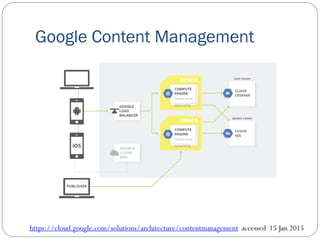
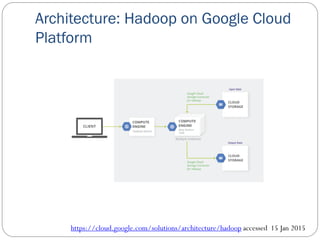
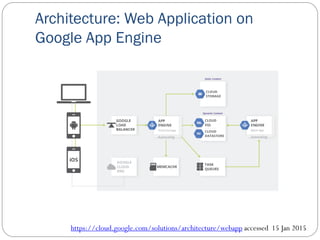
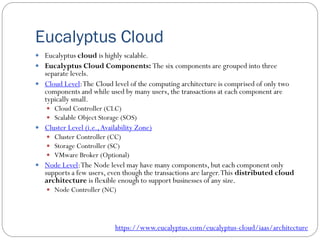
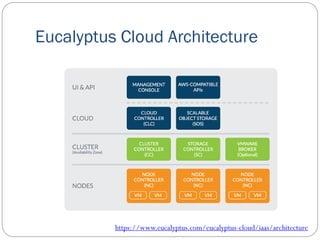
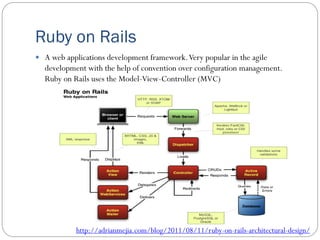
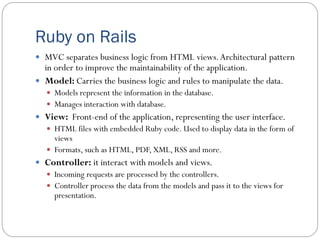
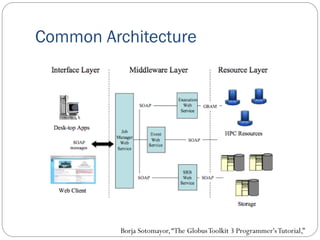
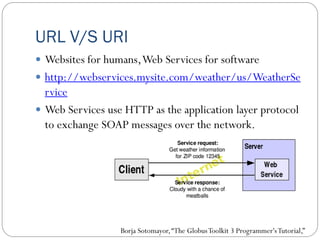
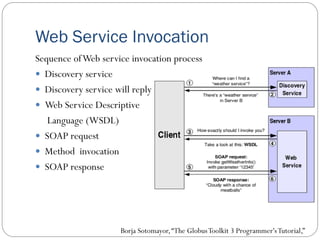
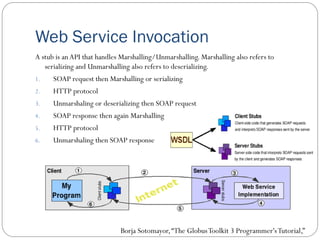
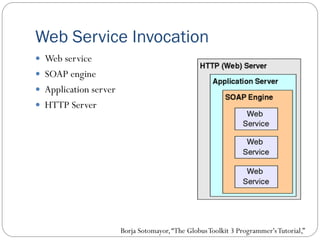
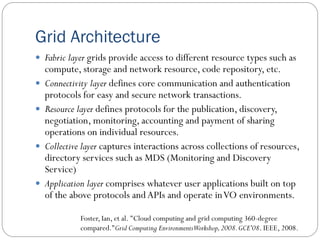
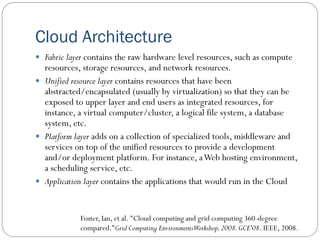
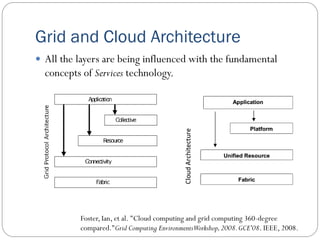
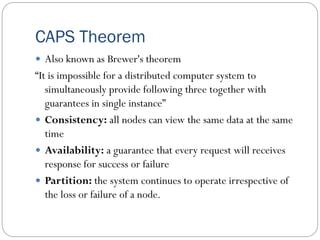
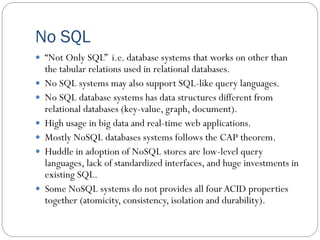
The document provides an extensive overview of cloud computing architecture, detailing the roles of various actors such as cloud consumers, providers, brokers, auditors, and carriers. It discusses the essential characteristics of cloud services alongside the requirements for scalability and cost efficiency, emphasizing the importance of service level agreements (SLAs). Additionally, it outlines various technologies and services including Hadoop, Storm, and the Google File System, while examining their applications in cloud environments.