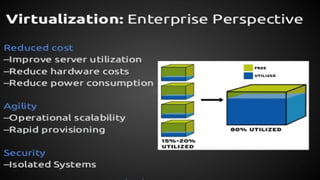
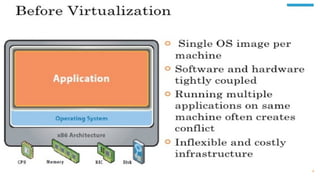
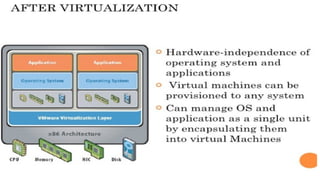
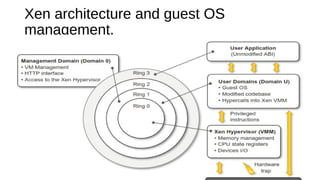
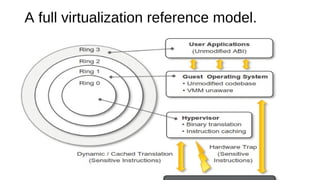
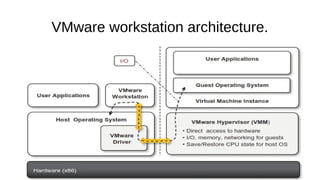
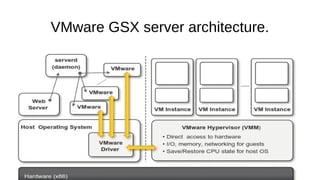
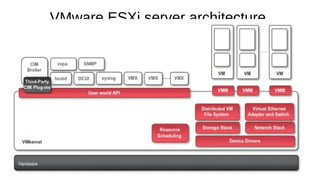
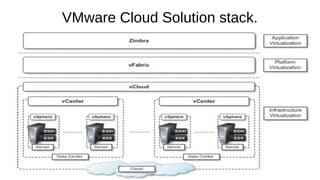
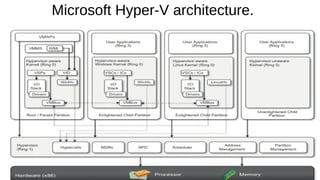
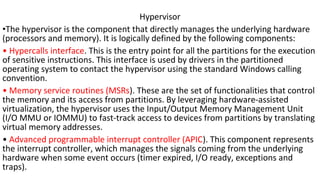
Virtualization provides advantages like managed execution, isolation, resource partitioning and portability. However, it can also lead to performance degradation, inefficiency, and new security threats. Virtualization technologies like Xen, VMware and Hyper-V use approaches like paravirtualization and full virtualization to virtualize hardware and provide isolated execution environments while managing the tradeoffs between performance, functionality and security.