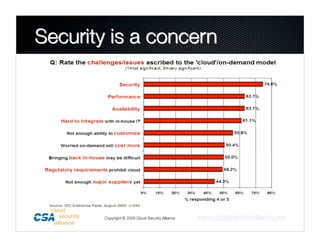
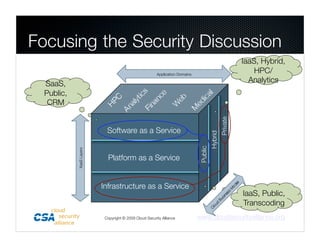
1. The Cloud Security Alliance is a global non-profit organization focused on best practices for cloud security.
2. It has an inclusive membership of cloud experts and produces guidance documents, checklists, and research on topics like threats, encryption, and compliance.
3. The Alliance aims to help secure cloud computing through education and by promoting best practices.