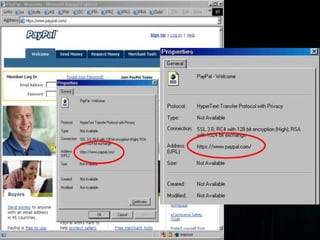
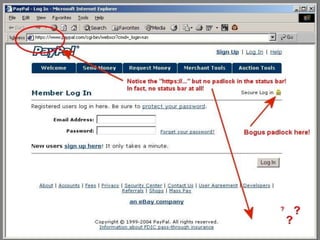
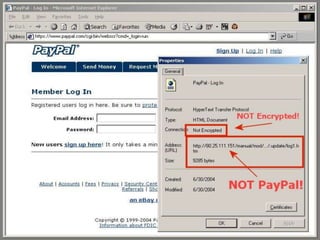
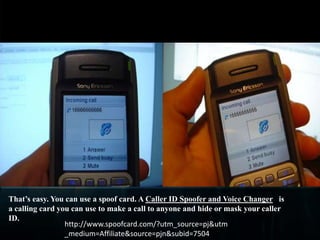
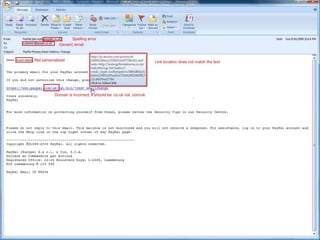
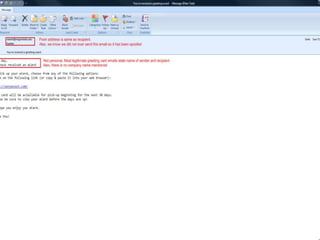
Spoofing involves falsifying data to masquerade as another user or system. There are several types of spoofing attacks:
IP spoofing involves altering packet source IP addresses to hide the identity of the actual source. URL and referrer spoofing tricks users into thinking they are visiting legitimate sites when they are actually being directed to fake sites controlled by attackers. Caller ID spoofing allows callers to hide their real numbers. Email address spoofing modifies email headers to make emails appear to be from someone other than the actual sender. Spoofing techniques are commonly used by hackers and spammers to conceal their identities and gain illegitimate access.