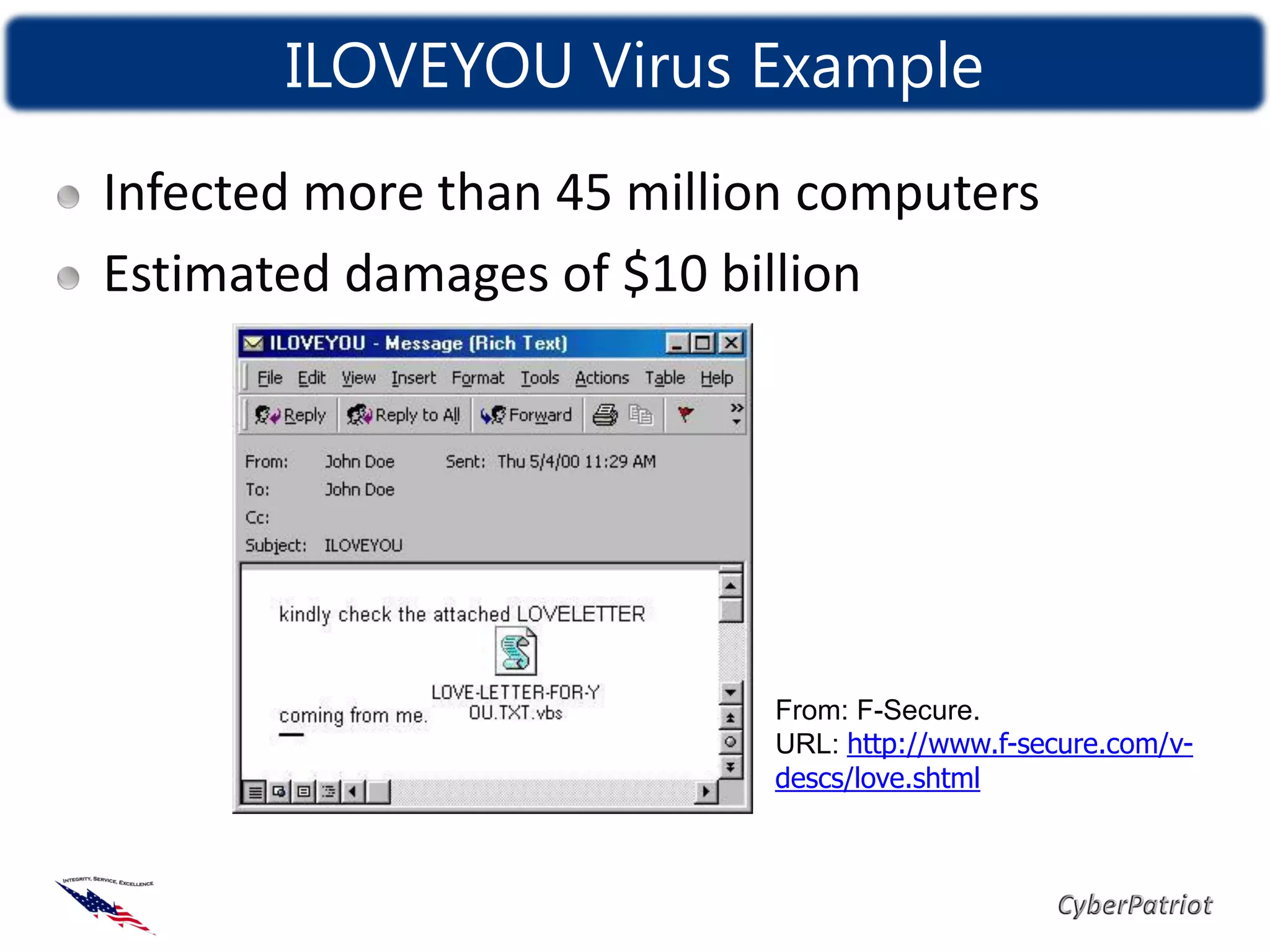
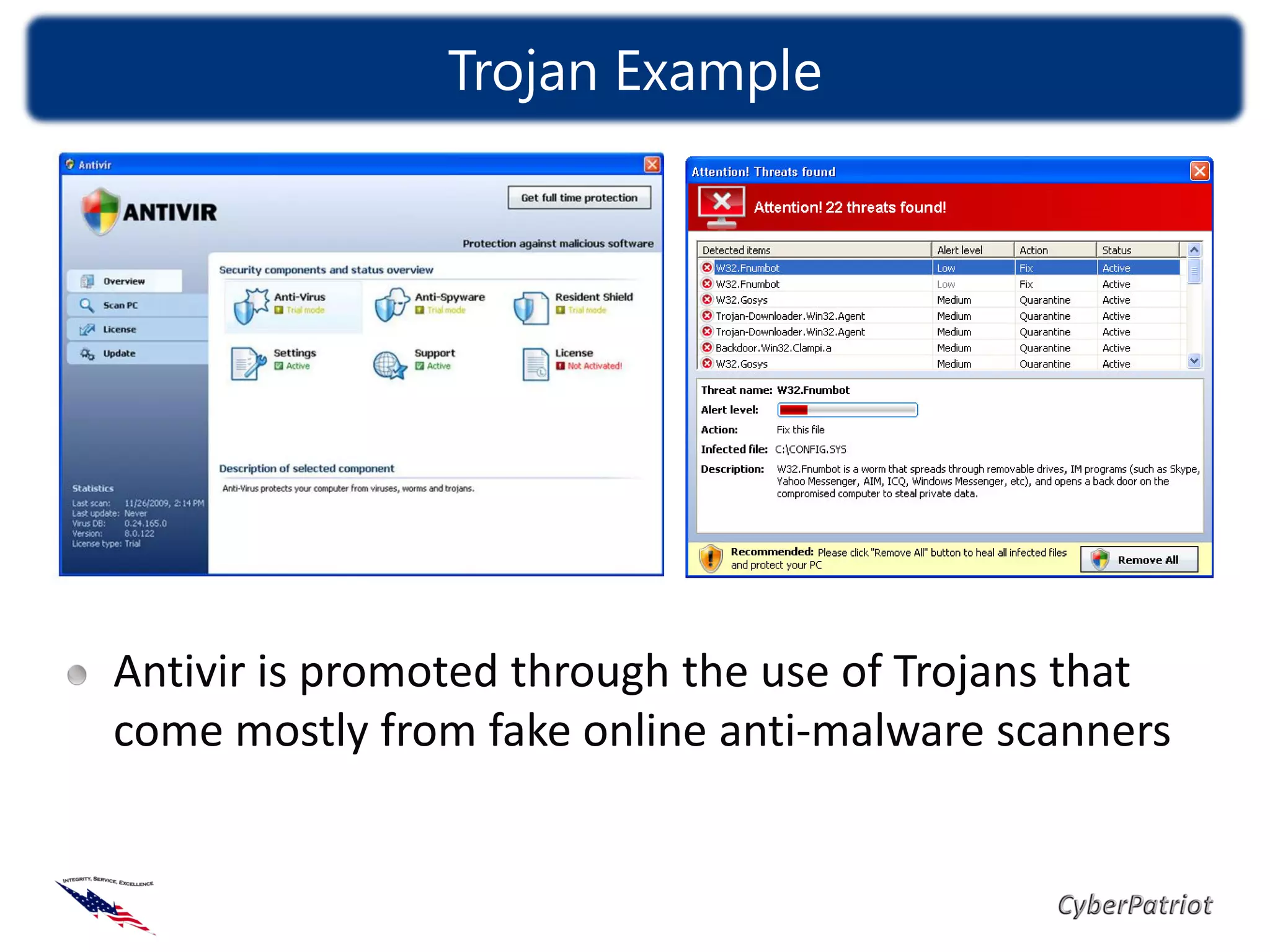
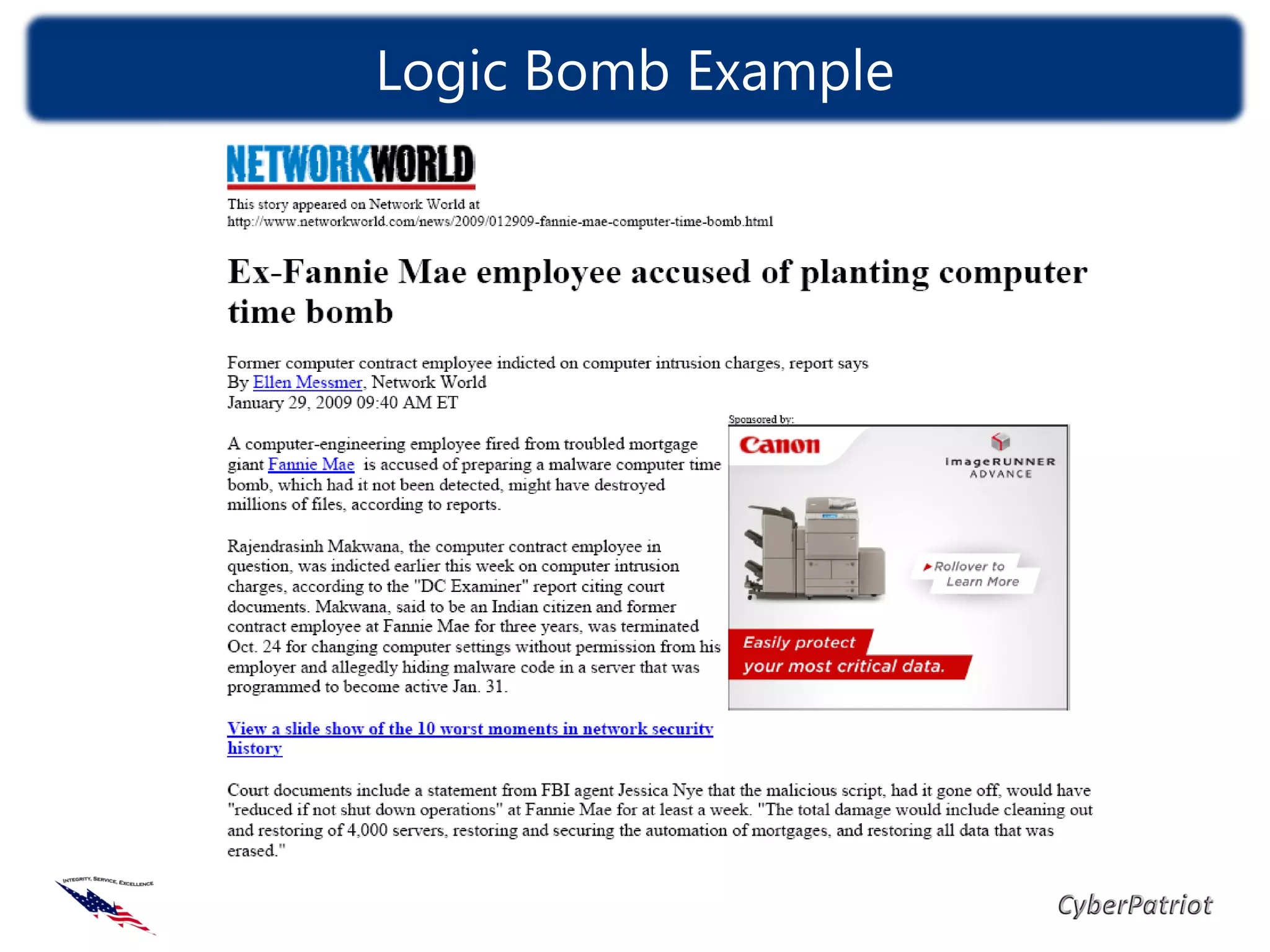
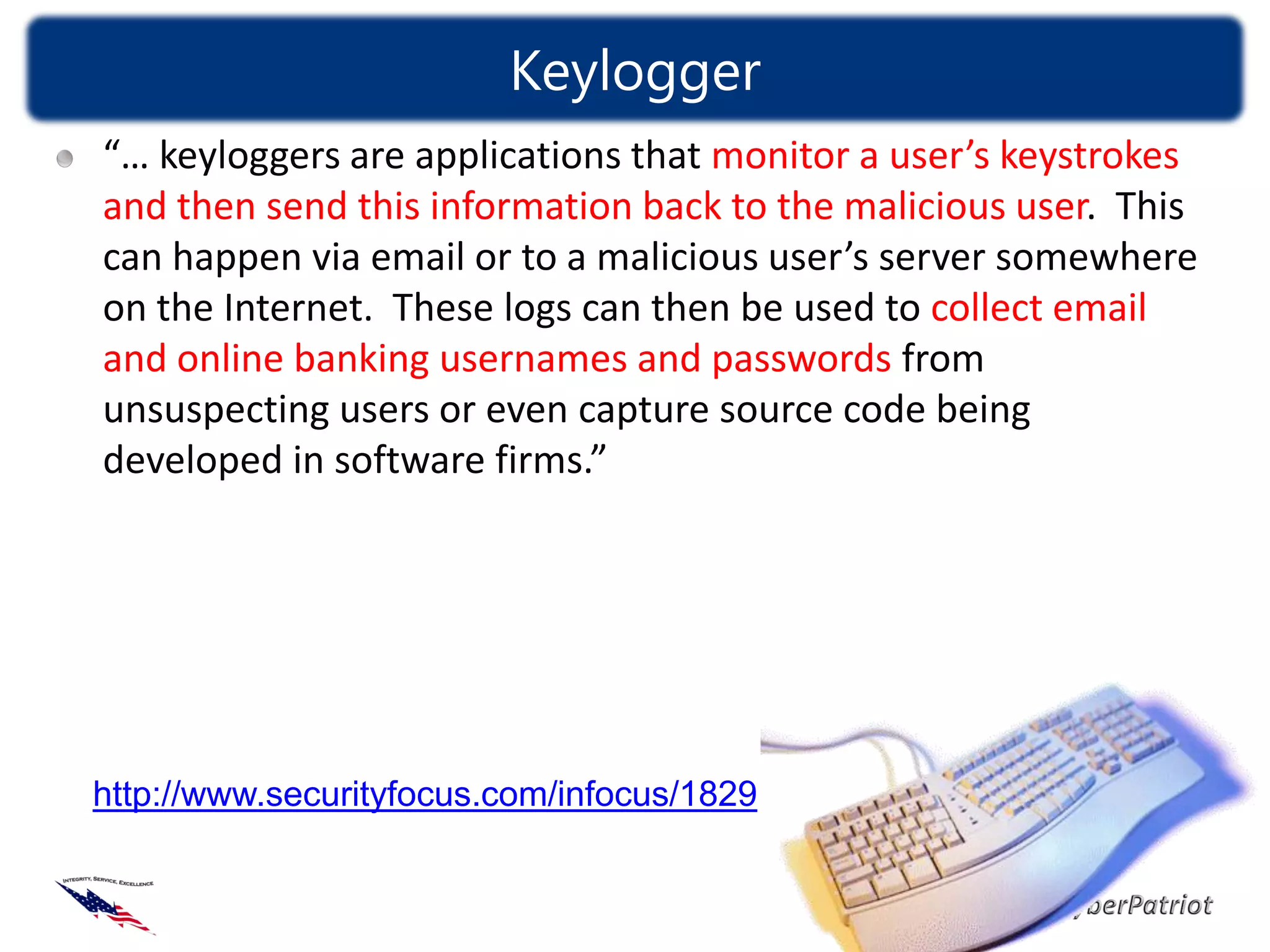
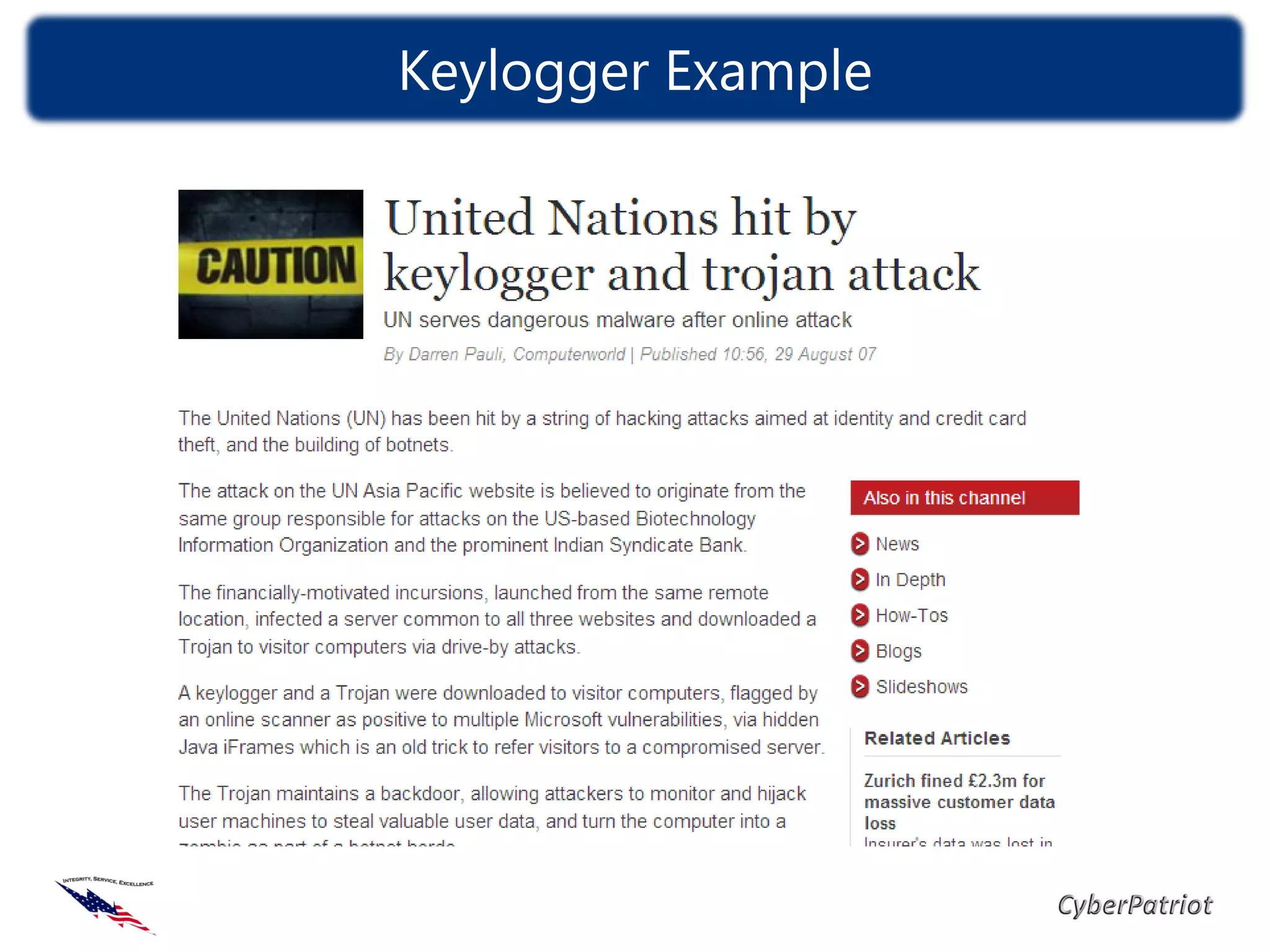
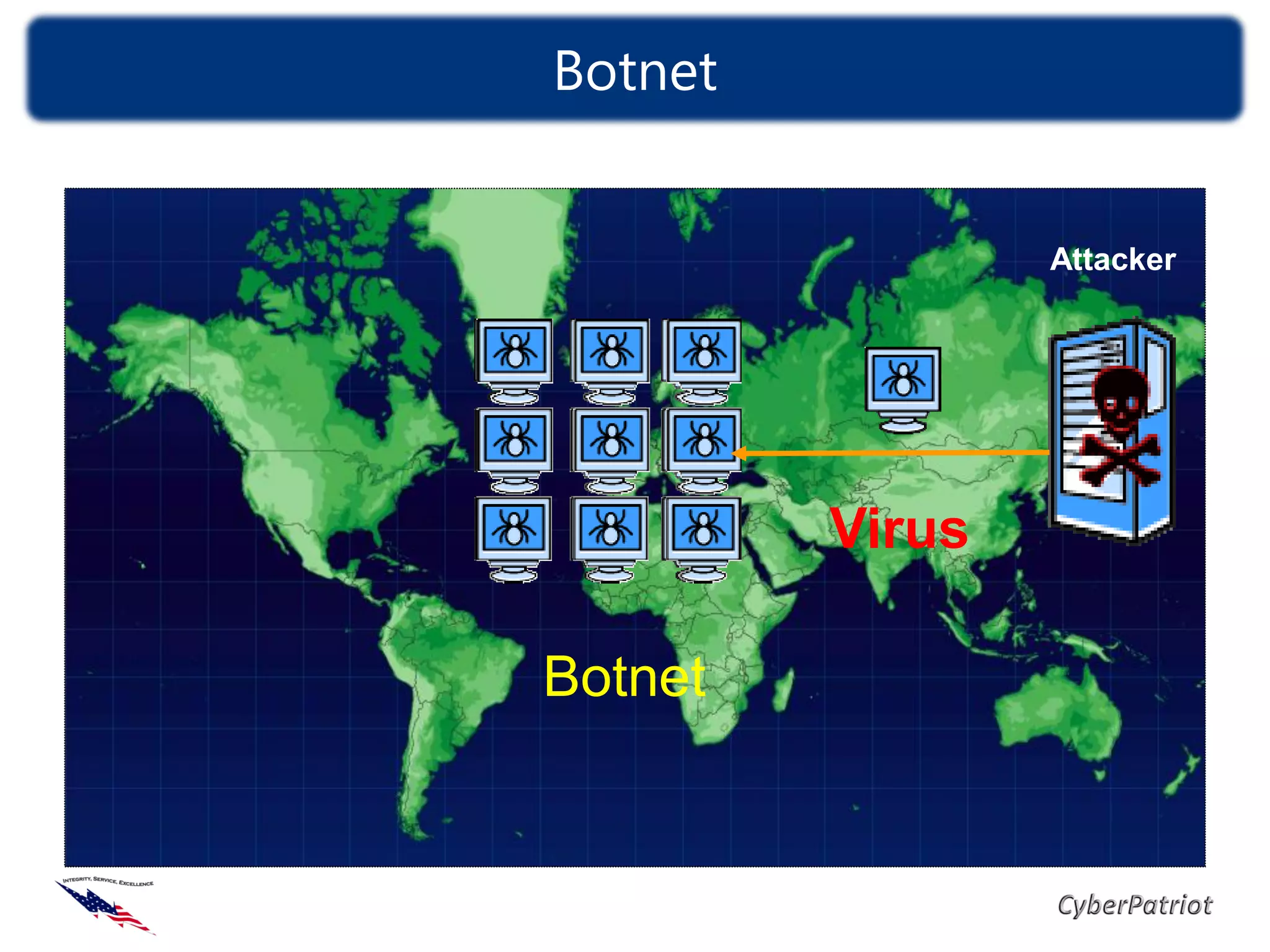
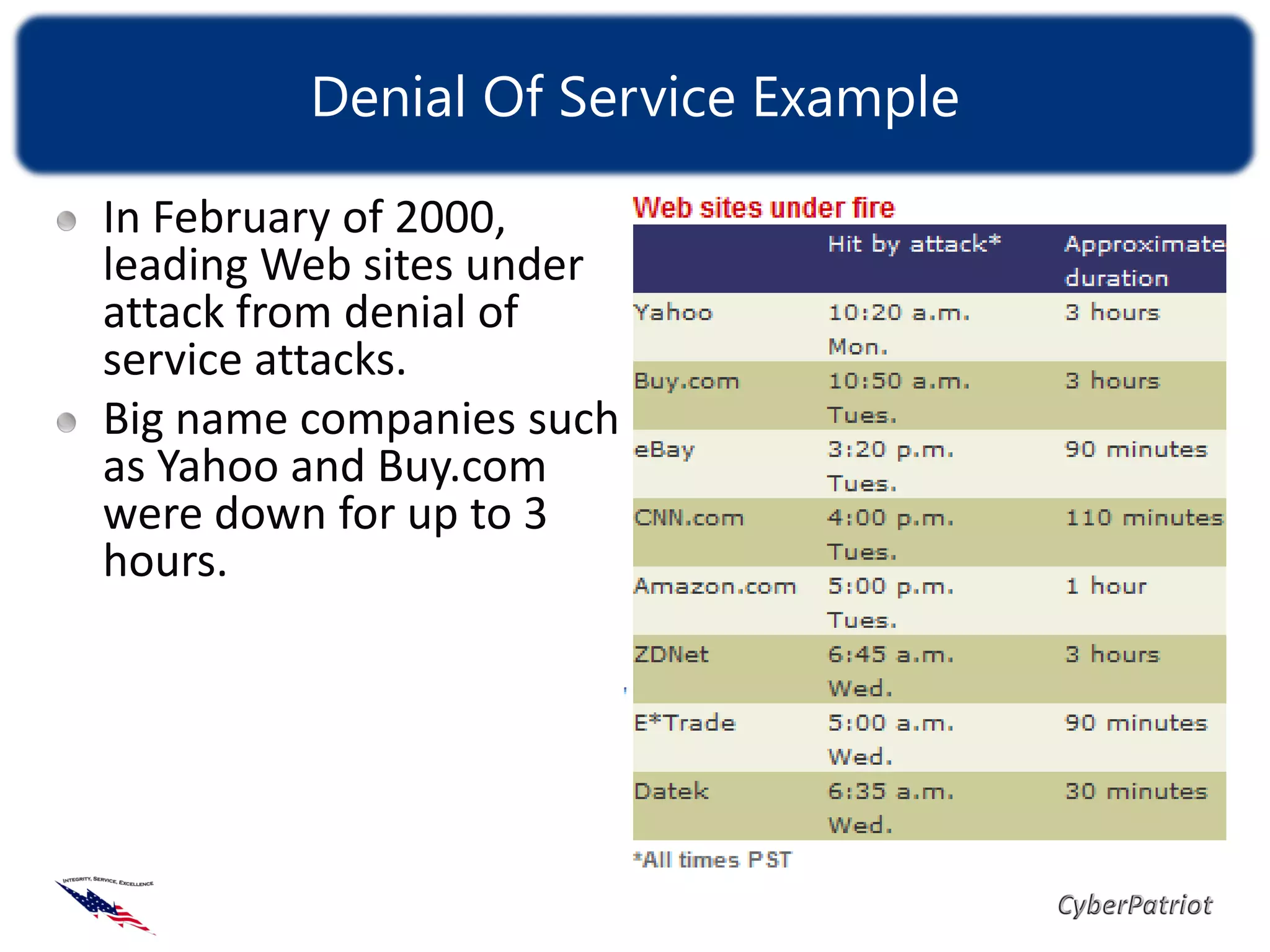
The document defines threats, vulnerabilities, and various types of malware such as viruses, worms, and Trojans. It provides examples of how malware like the ILOVEYOU virus and Sasser worm spread and caused damage. The document also discusses how compromised computers can be used in botnets for spamming and denial of service attacks. It concludes with recommendations on security best practices like keeping systems updated, using antivirus software, and practicing cyber awareness.