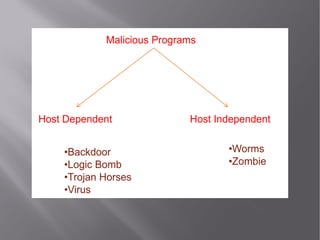
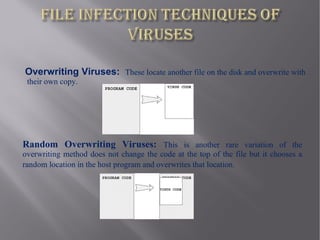
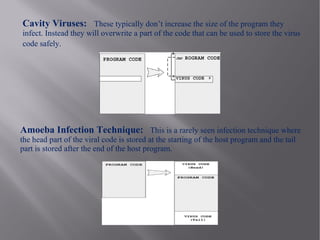
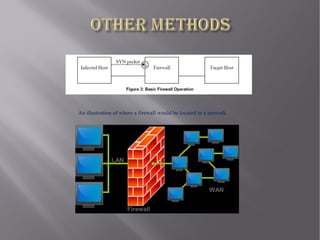
This document discusses network viruses and strategies for virus detection and prevention. It defines viruses, worms, and Trojan horses and explains how they differ. It then covers various virus spreading strategies and types, including binary, script, macro, boot sector, and worm viruses. The document also discusses detection methods like signature-based and heuristic detection. For prevention, it recommends keeping antivirus software and signatures updated to identify new viruses. Memory demands of antivirus software are also discussed.





















![[1] Peter Szor, The Art of Computer Virus and Defence, Harlow, England:
Addison Wesely Professional, 2005.
[2] Norman, Norman book on Computer Virus, Norman ASA, 2003.
[3] Dan Xu, Xiang Li, and Xian Fan Wang, Mechanisms for Spreading of
Computer Virus on the Internet: An Overview, IEEE Computer Society 2004,
601-606.
[4] Darrell M. Kienzie, and Matthew C. Elder, Recent Worms: A Survey and
Trends, Washington, DC, USA: WORM-2003
[5] David Moore, Vern Paxson, Stefan Savage, Colleen, Stuart Staniford and
Nicholas Weaver, Inside the Slammer Worm, IEEE Security and Privacy, 2003.
[6] Nicholas Weaver, Vern Paxson, Stuart Staniford, and Robert Cunnigham, A
Taxonomy of Computer Worms, Washington, DC, USA: WORM-2003.](https://image.slidesharecdn.com/networkvirusdetectionprevention-120429070735-phpapp01/85/Network-virus-detection-prevention-28-320.jpg)