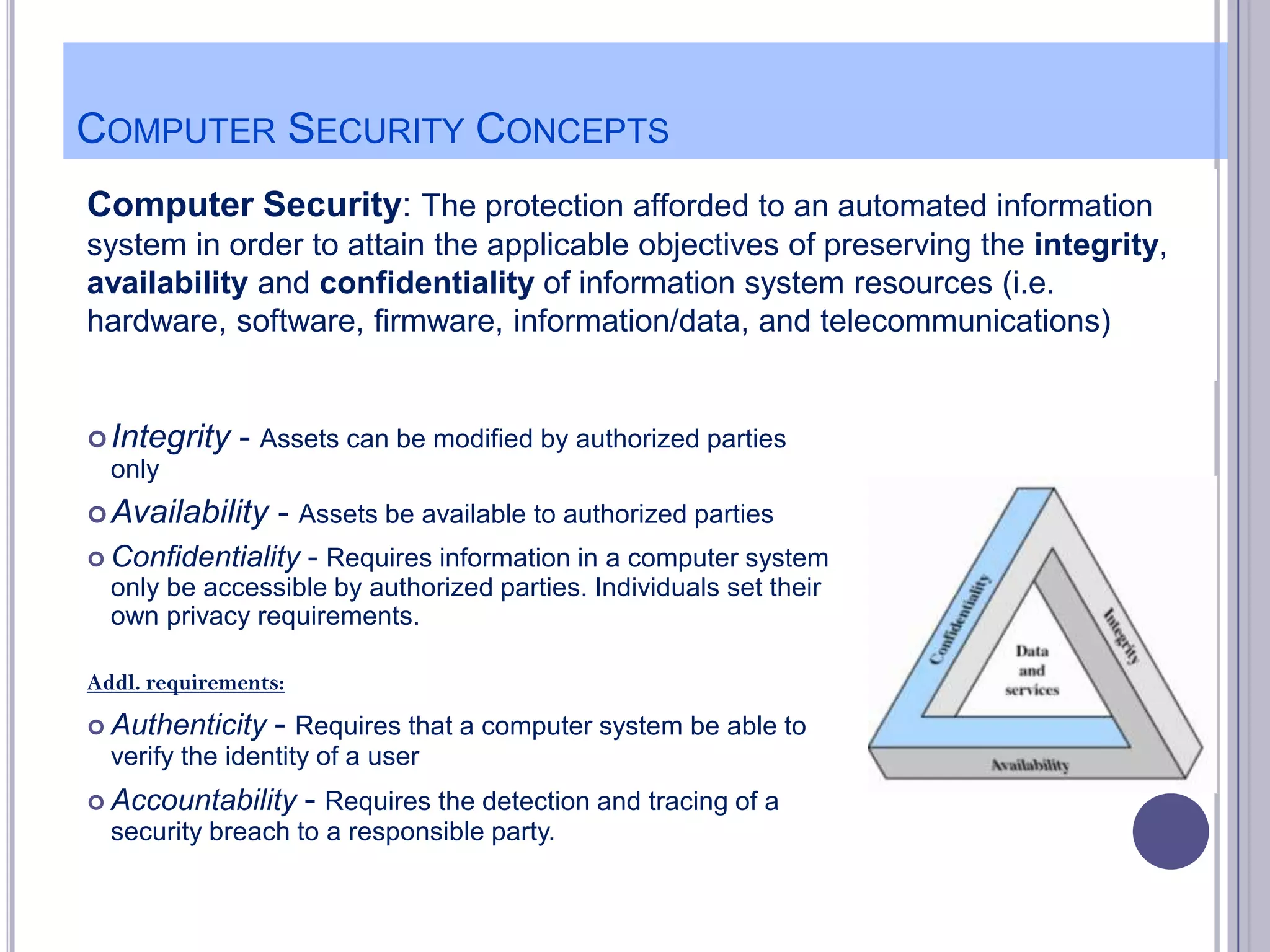
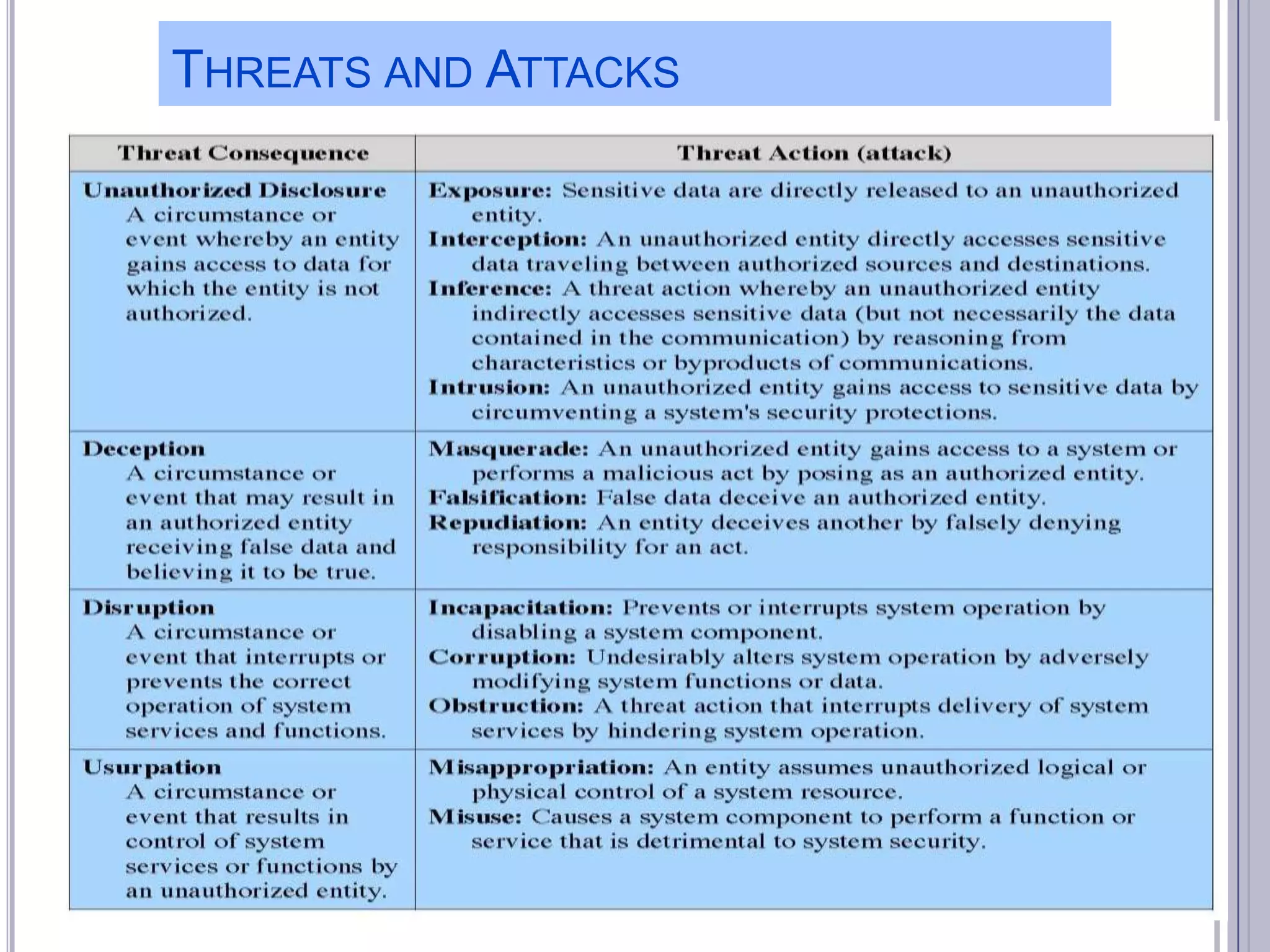
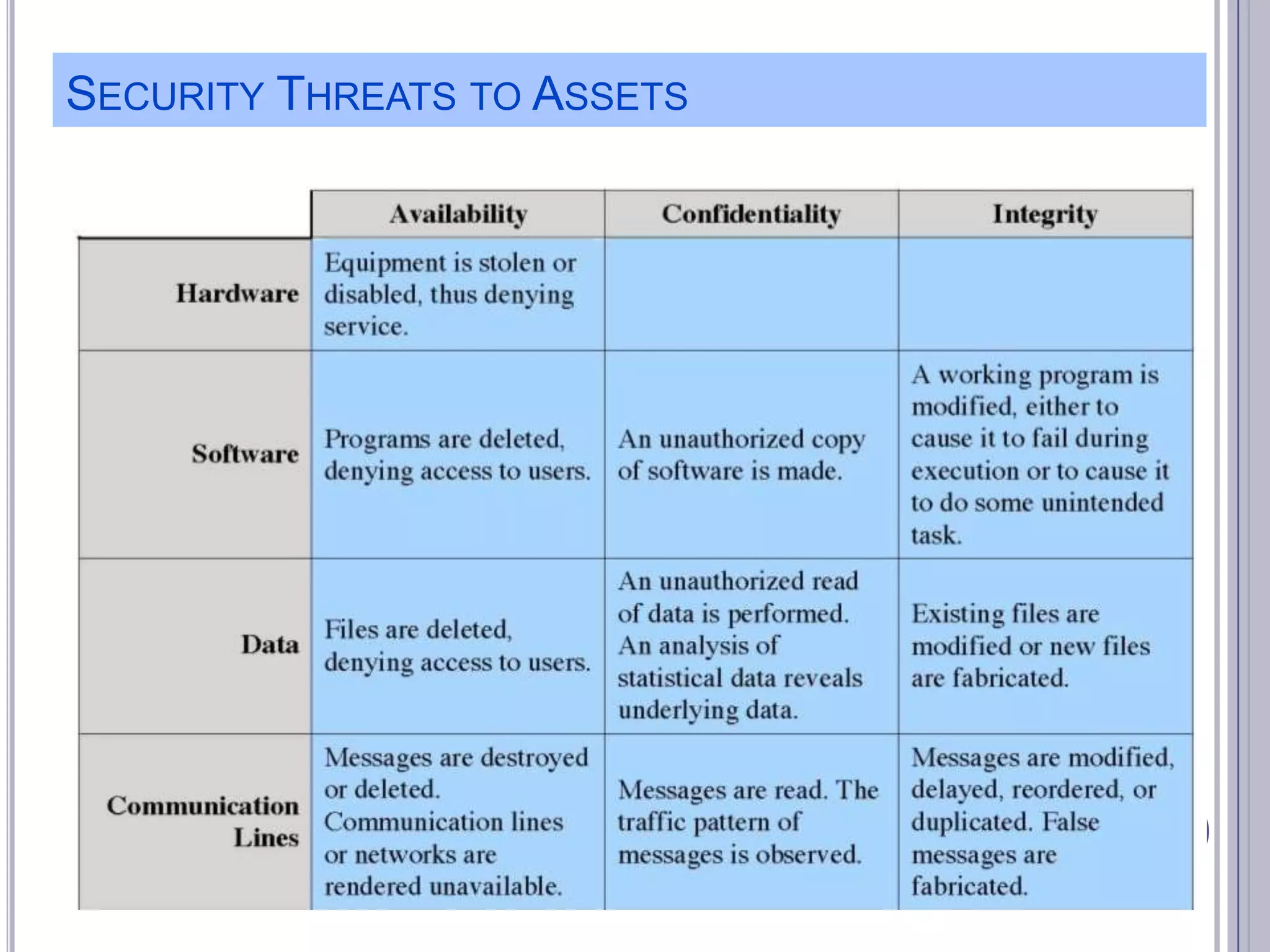
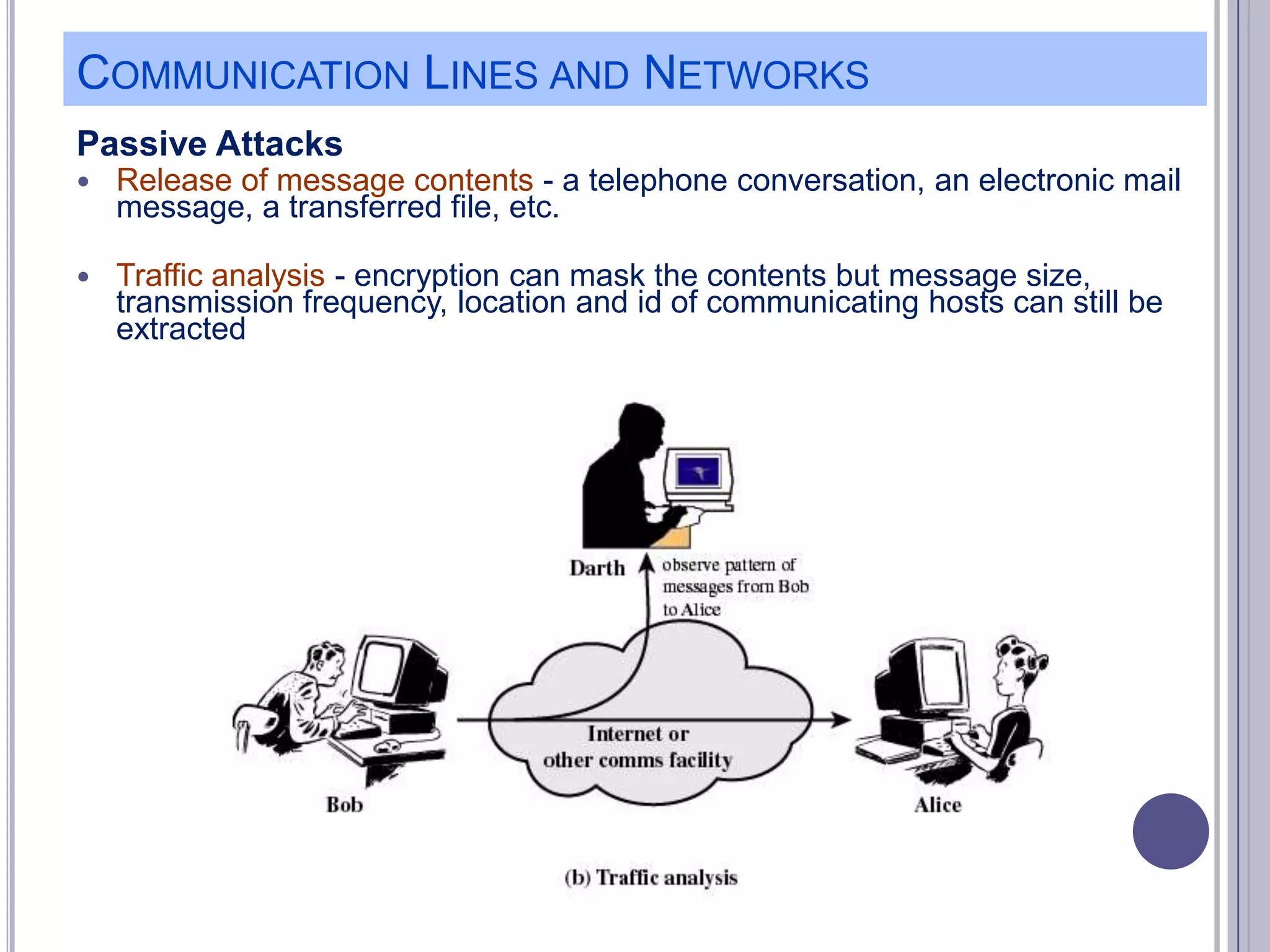
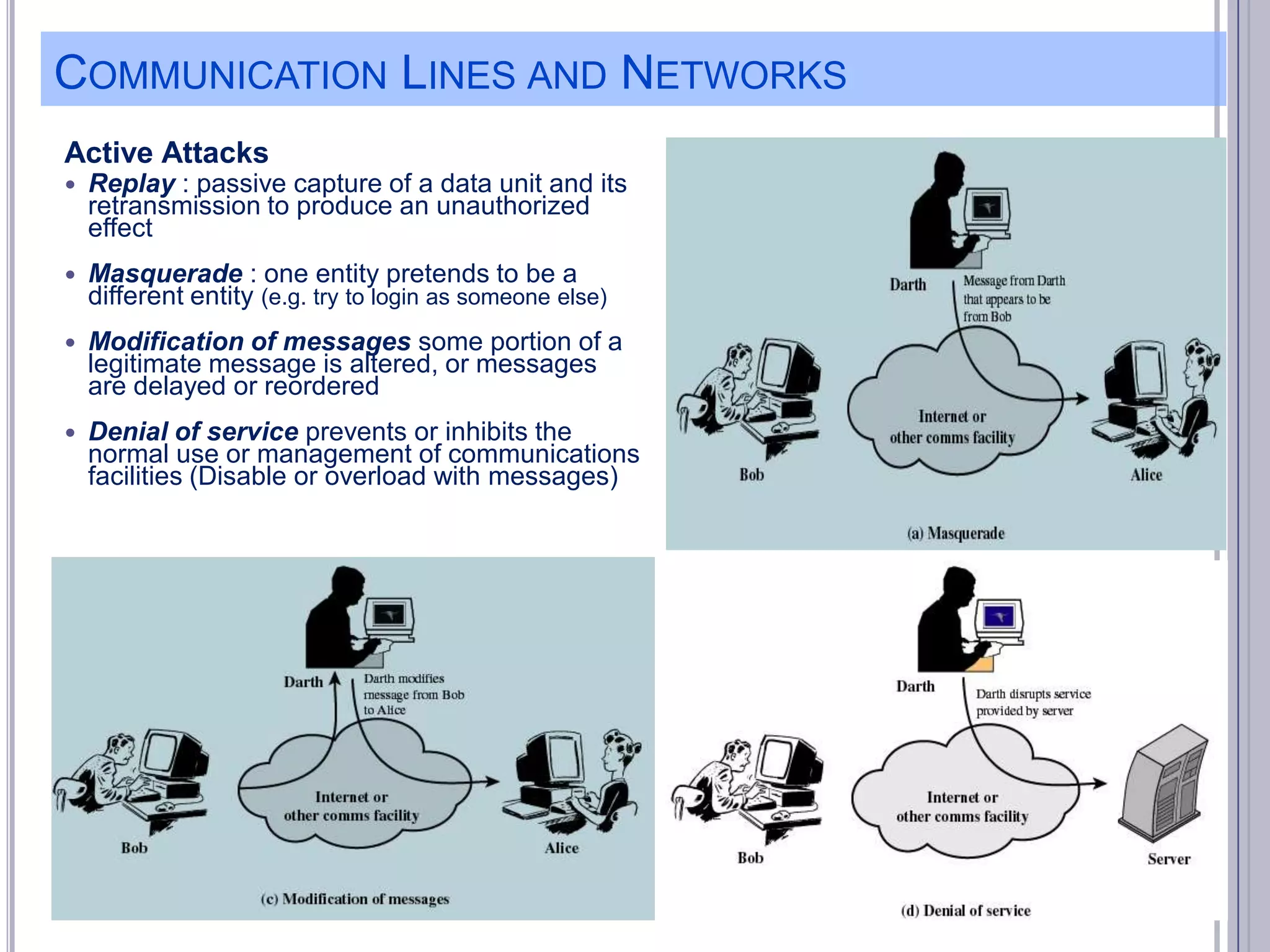
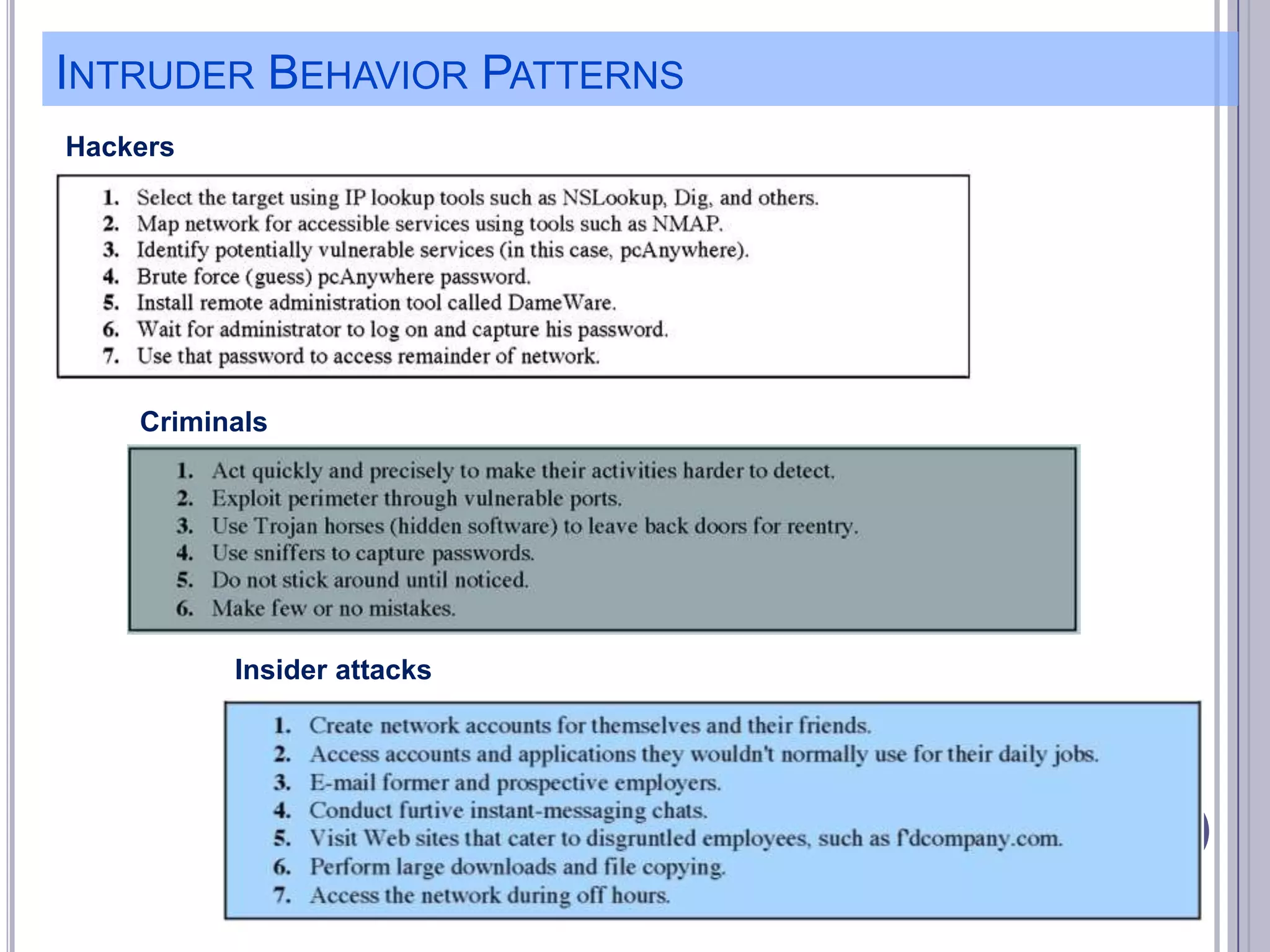
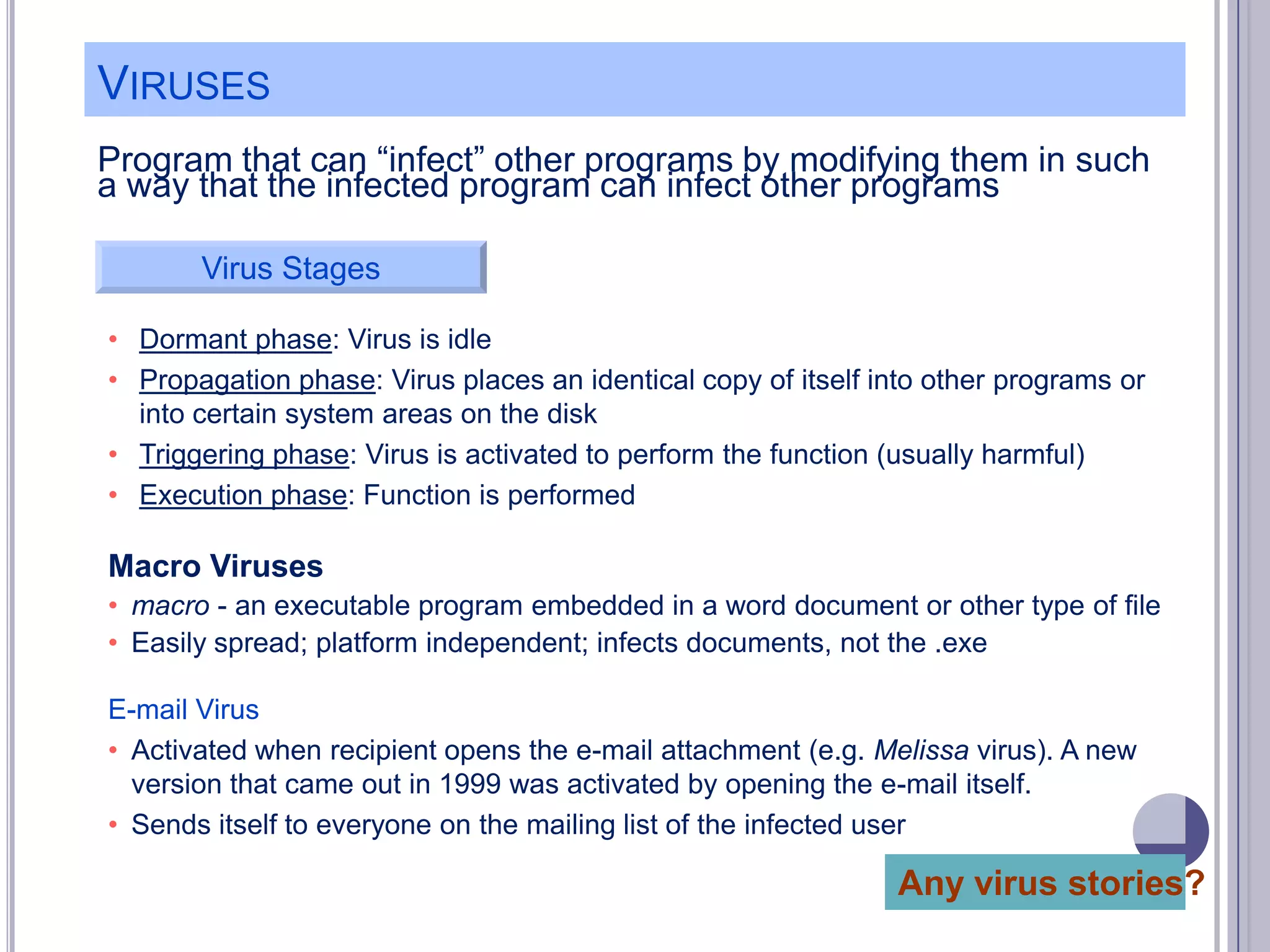
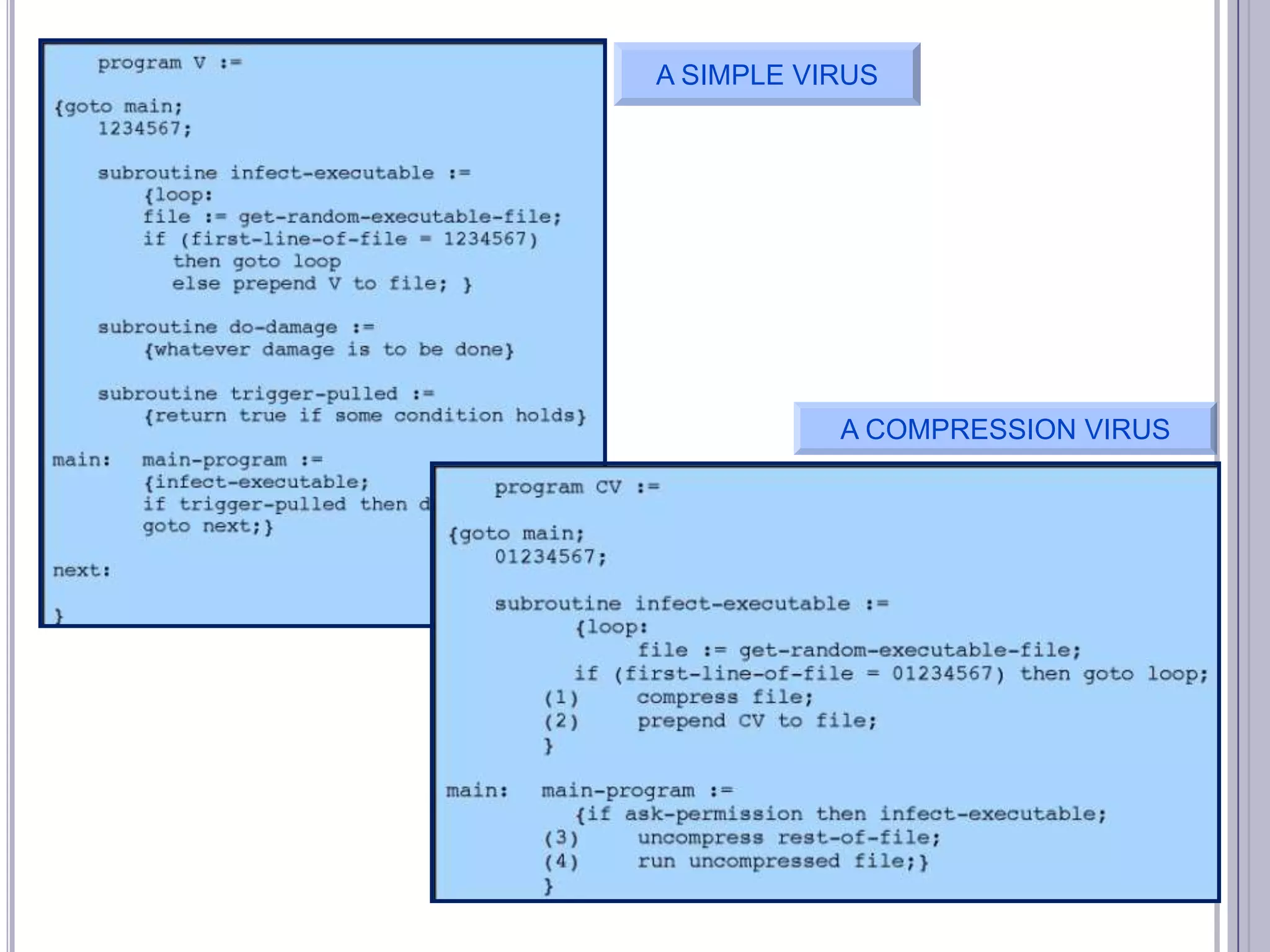
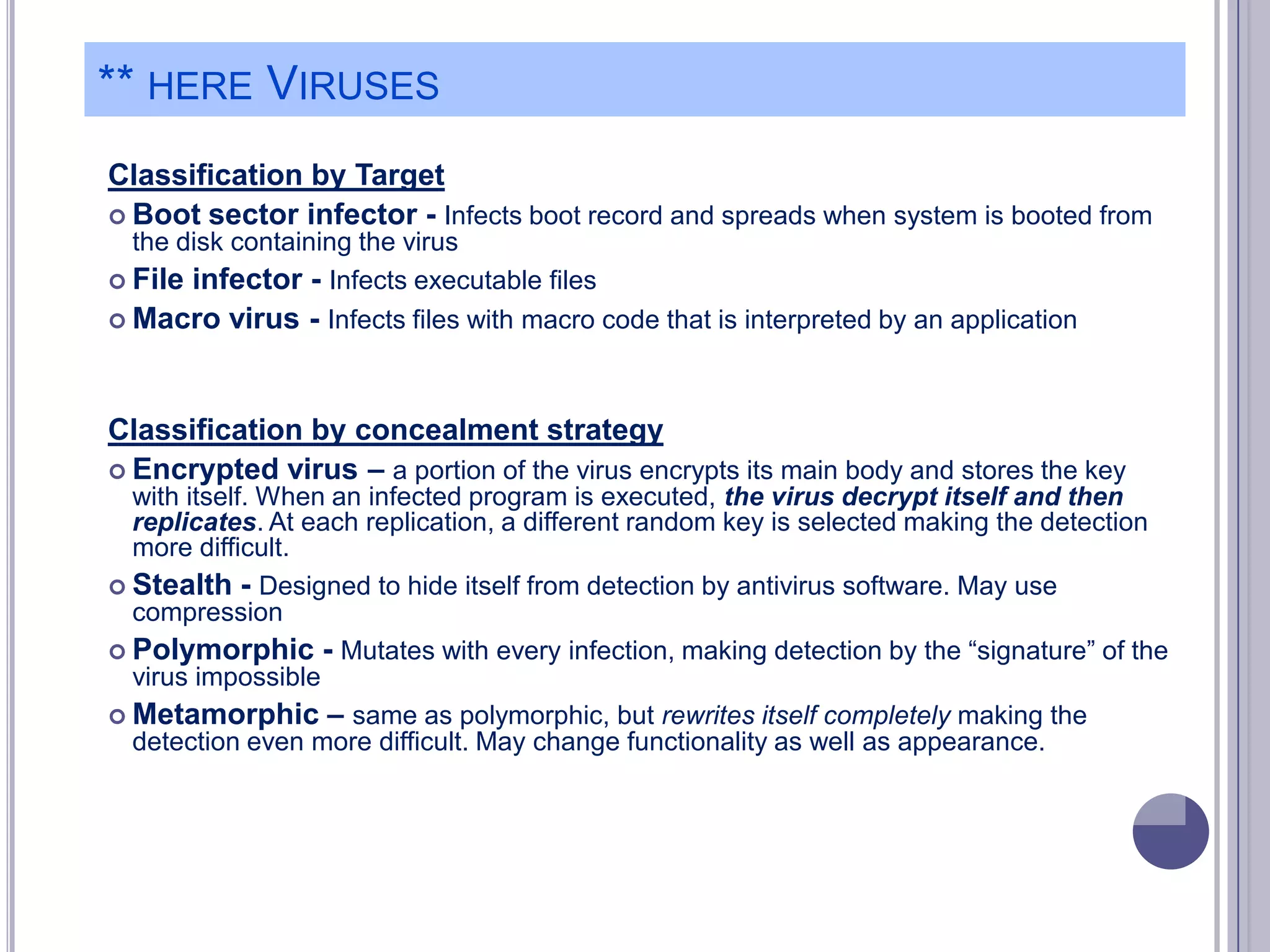
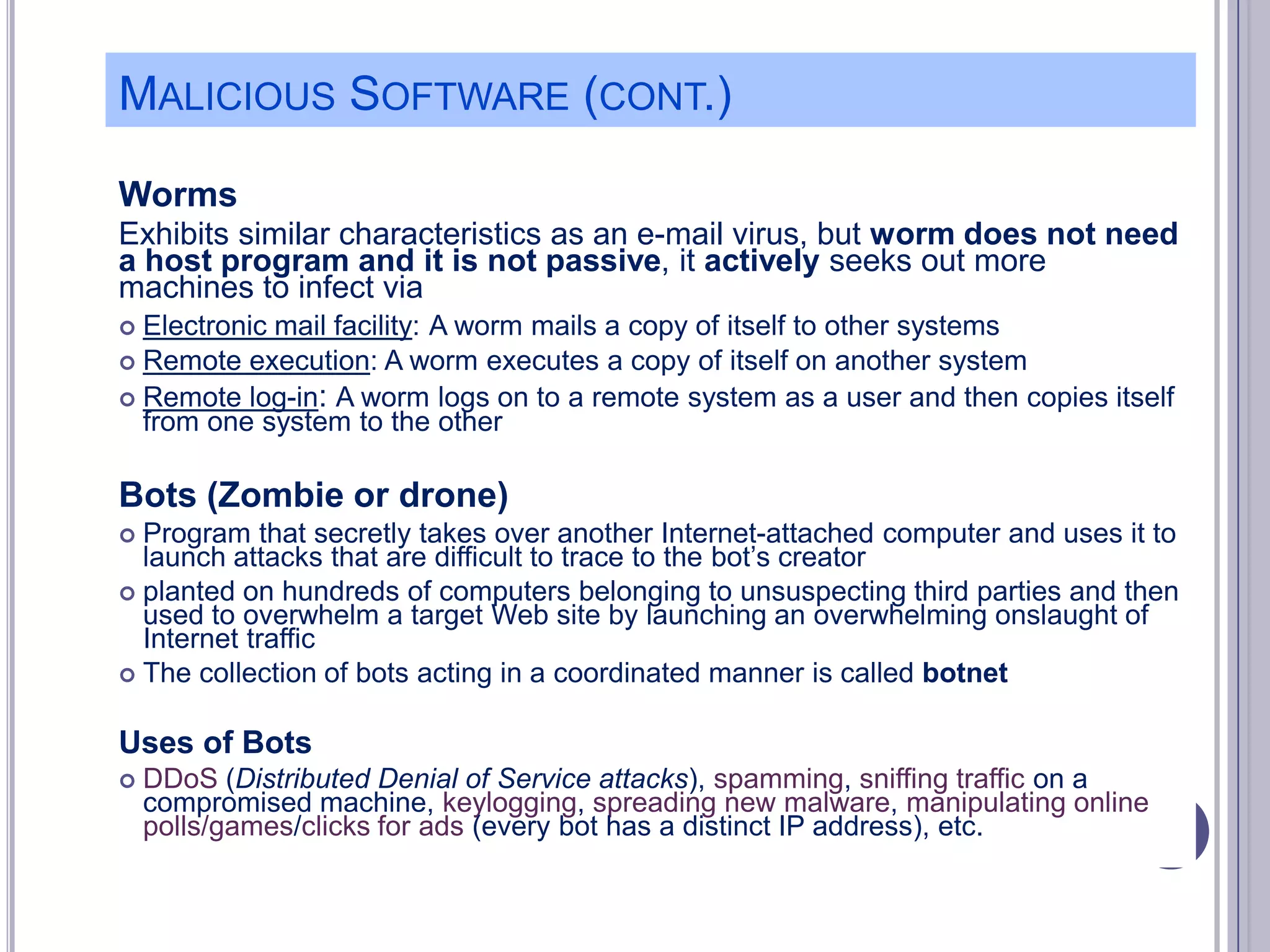
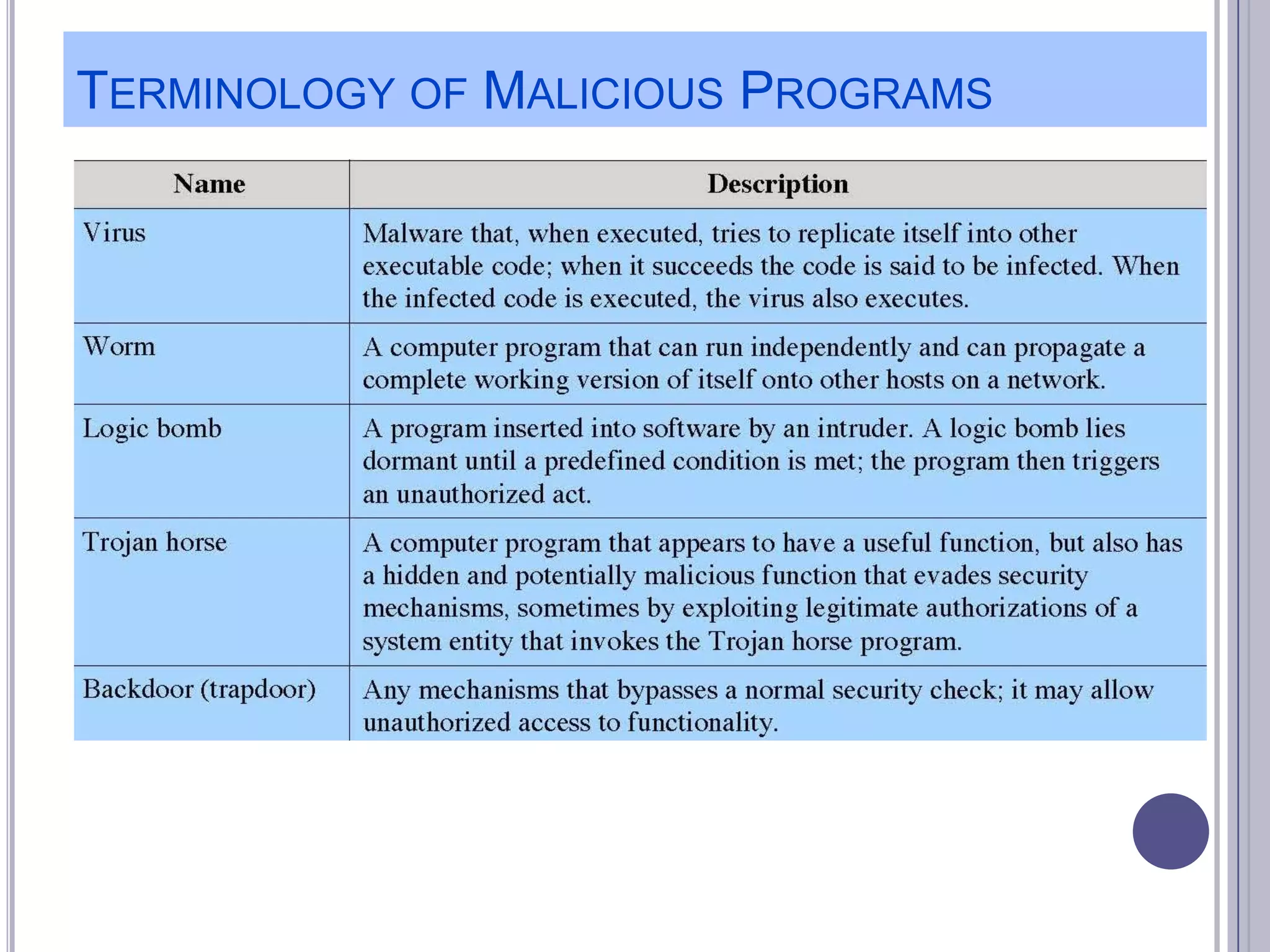
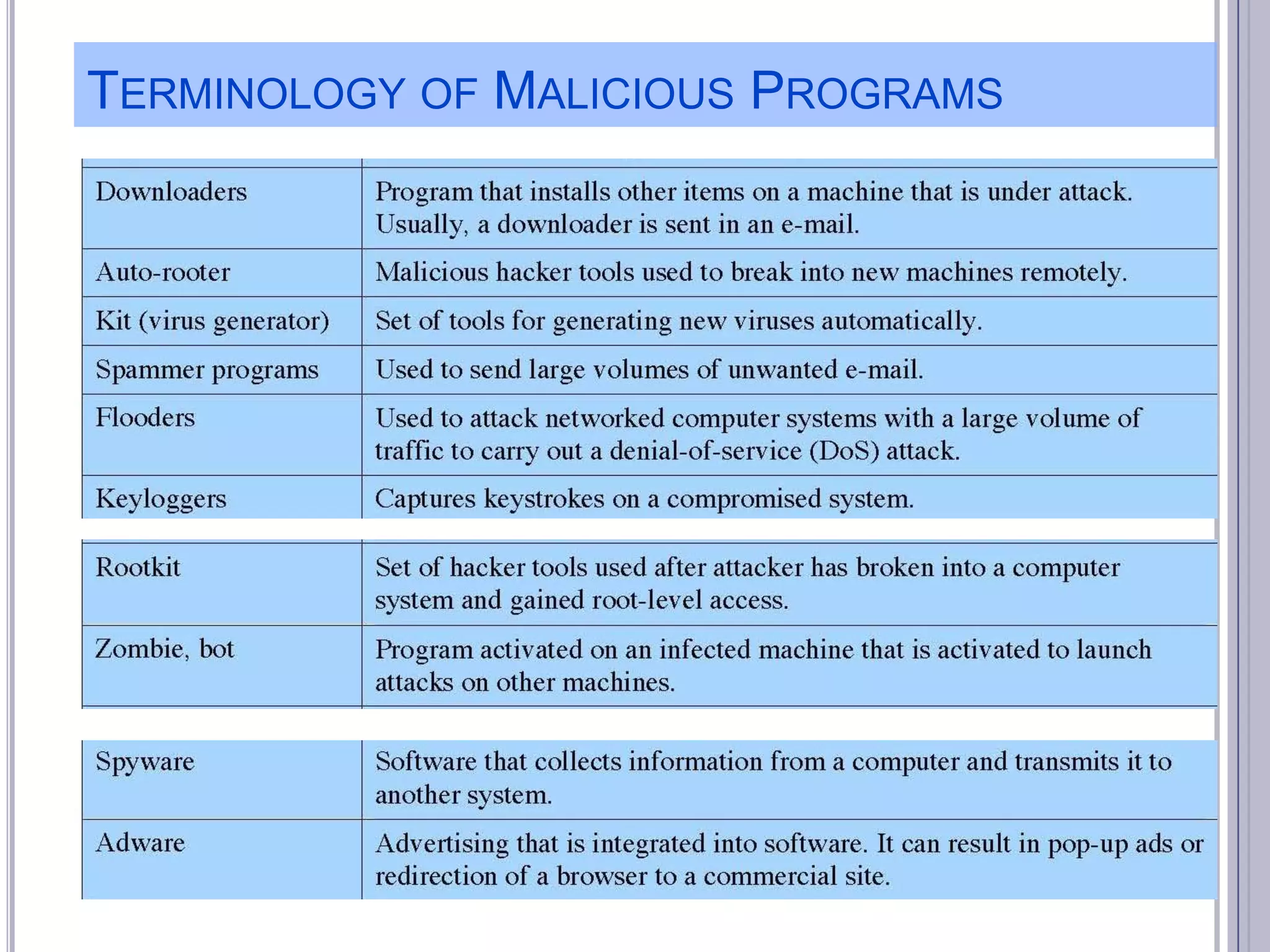
The document describes various computer security concepts including threats to information systems like viruses, worms, Trojans, and bots. It discusses different types of malware such as file infectors, macro viruses, encrypted viruses, and rootkits. It also outlines security defenses like using updated antivirus software, firewalls, and practicing safe email/web habits by avoiding suspicious attachments or downloads.