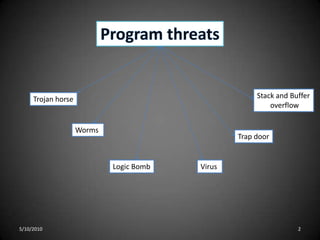
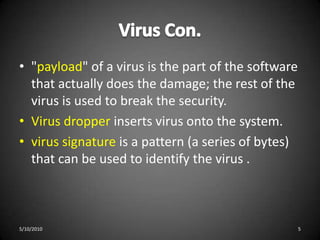
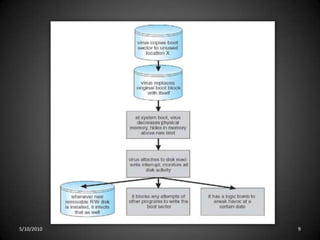
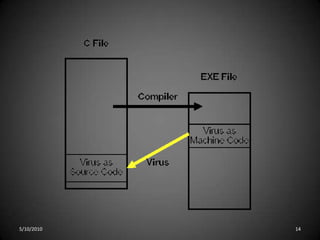
This document discusses various types of program threats including logic bombs, viruses, worms, and trojan horses. It focuses on viruses, defining them as code fragments embedded in legitimate programs that can spread via email or macros. The document categorizes viruses and provides examples, noting that file viruses append to files, boot sector viruses infect boot sectors, macro viruses spread through documents, and polymorphic/encrypted viruses aim to avoid detection. In summary, it defines computer viruses, explains how they spread, and outlines several categories of viruses along with examples.