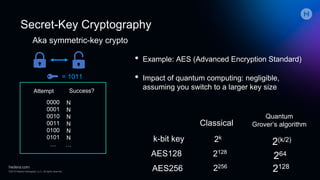
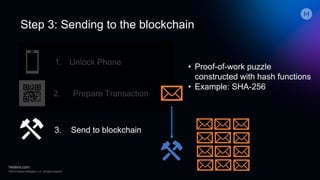
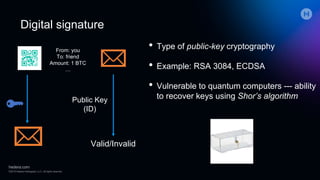
The document discusses the implications of quantum computing on cryptography, emphasizing the weaknesses of public-key cryptography against quantum attacks, while secret-key cryptography may remain secure with larger key sizes. It outlines the current capabilities and limitations of quantum computers, highlighting the need for post-quantum cryptographic solutions and the importance of remaining agile in cryptographic practices. The presentation stresses the urgency of addressing vulnerabilities while awaiting standardization of new algorithms.



![Scott Aaronson, “The Limits of
Quantum Computers,” Scientific
American, 2008
“… [quantum computers] would provide
dramatic speedups for a few specific
problems… For other problems, however—
such as playing chess, scheduling airline
flights and proving theorems—evidence now
strongly suggests that quantum computers
would suffer from many of the same
algorithmic limitations as today’s classical
computers.”](https://image.slidesharecdn.com/slidesfromatul-191210193313/85/Quantum-Computing-Cryptography-A-Brief-Introduction-5-320.jpg)