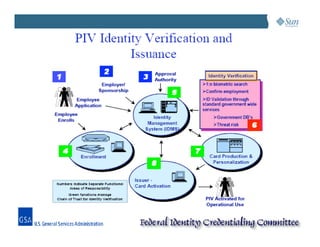
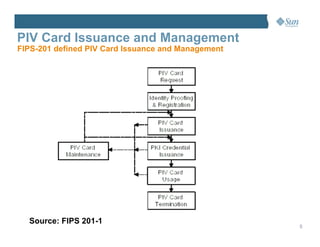
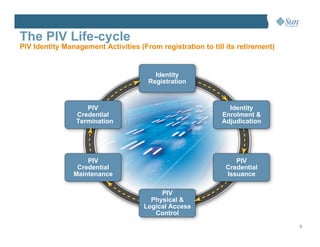
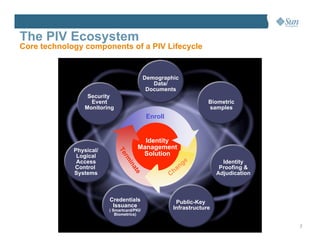
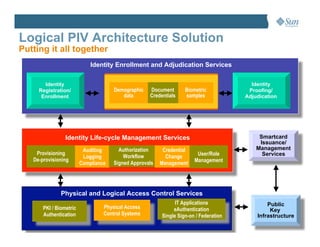
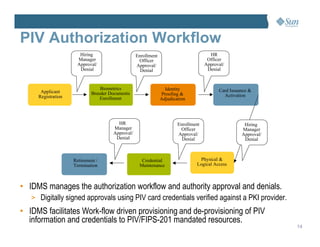
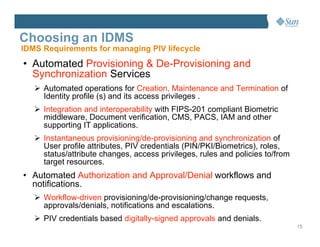
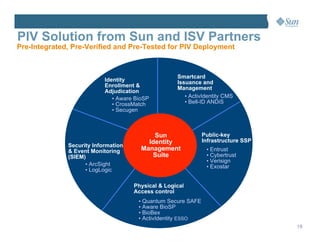
This document discusses managing the Personal Identity Verification (PIV) life-cycle and converging physical and logical access control systems. It explores the challenges of the PIV life-cycle from issuance through retirement. Key challenges include managing identity information across different systems, establishing administrative controls and workflows, and provisioning/de-provisioning with disparate solutions. The document also examines challenges of enabling PIV credentials to authenticate physical and logical access systems and managing authentication processes. Finally, it presents a logical PIV architecture solution to integrate identity enrollment, life-cycle management services, and physical/logical access control.