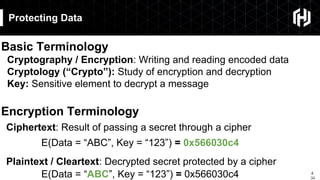
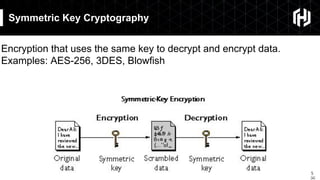
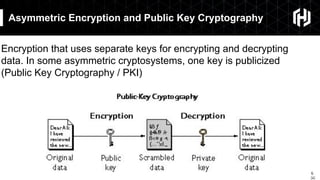
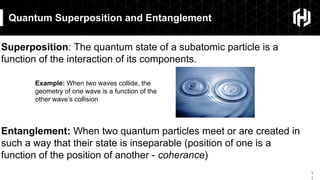
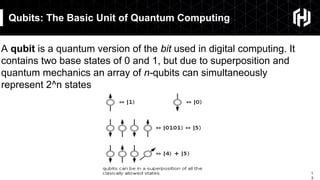
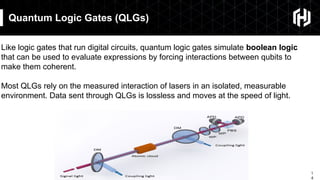
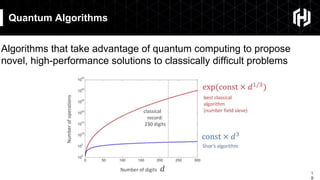
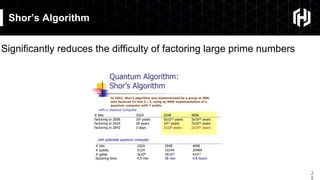
The document discusses the impact of quantum computing on cryptography, emphasizing the threats posed by quantum algorithms like Shor's and Grover's that can significantly weaken existing encryption methods, particularly asymmetric cryptography. It highlights the need for new quantum-secure cryptographic standards and the importance of adapting symmetric key cryptography to longer key lengths to enhance security. Additionally, quantum cryptography techniques like Quantum Key Exchange and the potential for new cryptographic mechanisms are introduced as advancements in safeguarding data.