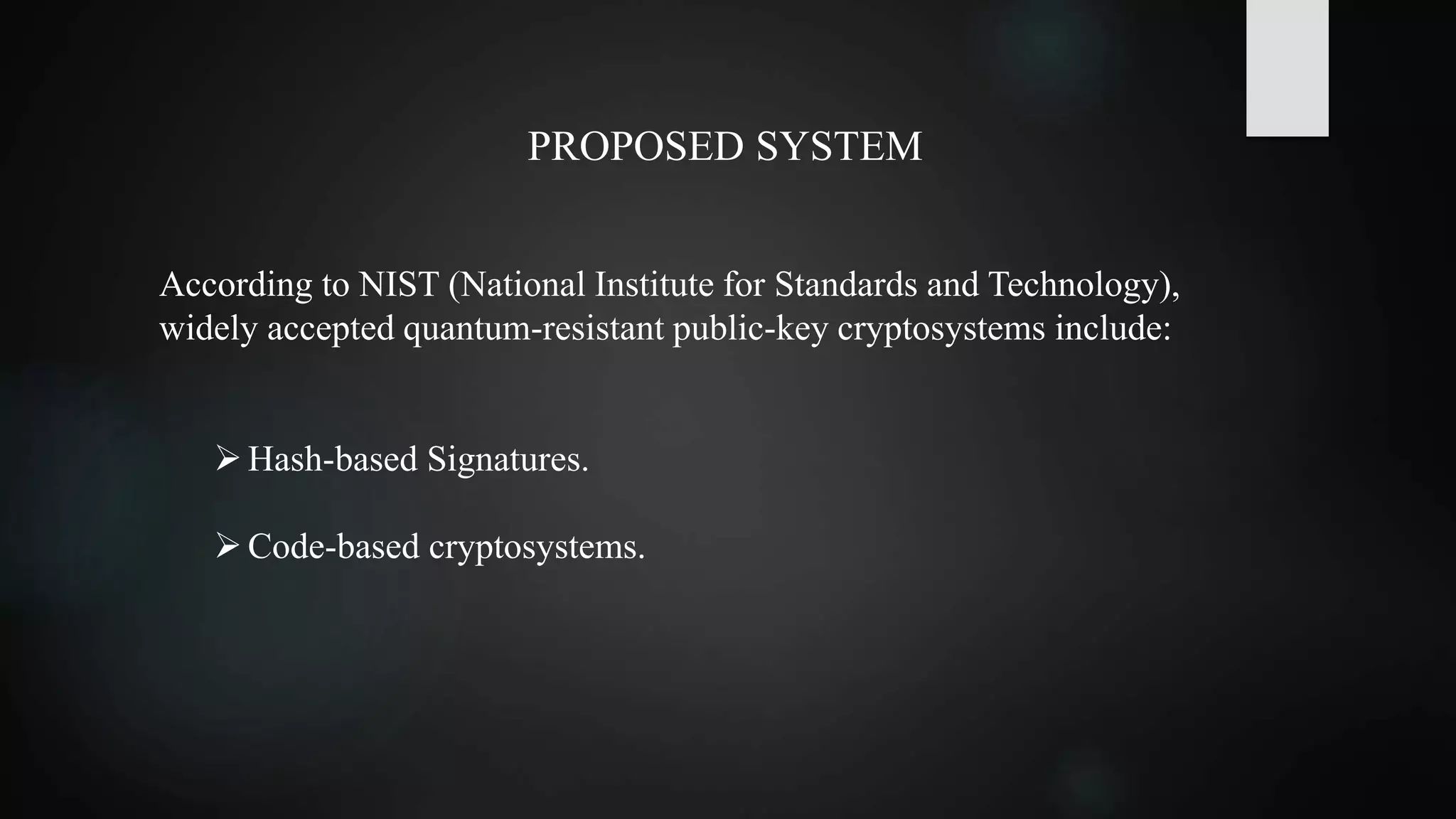
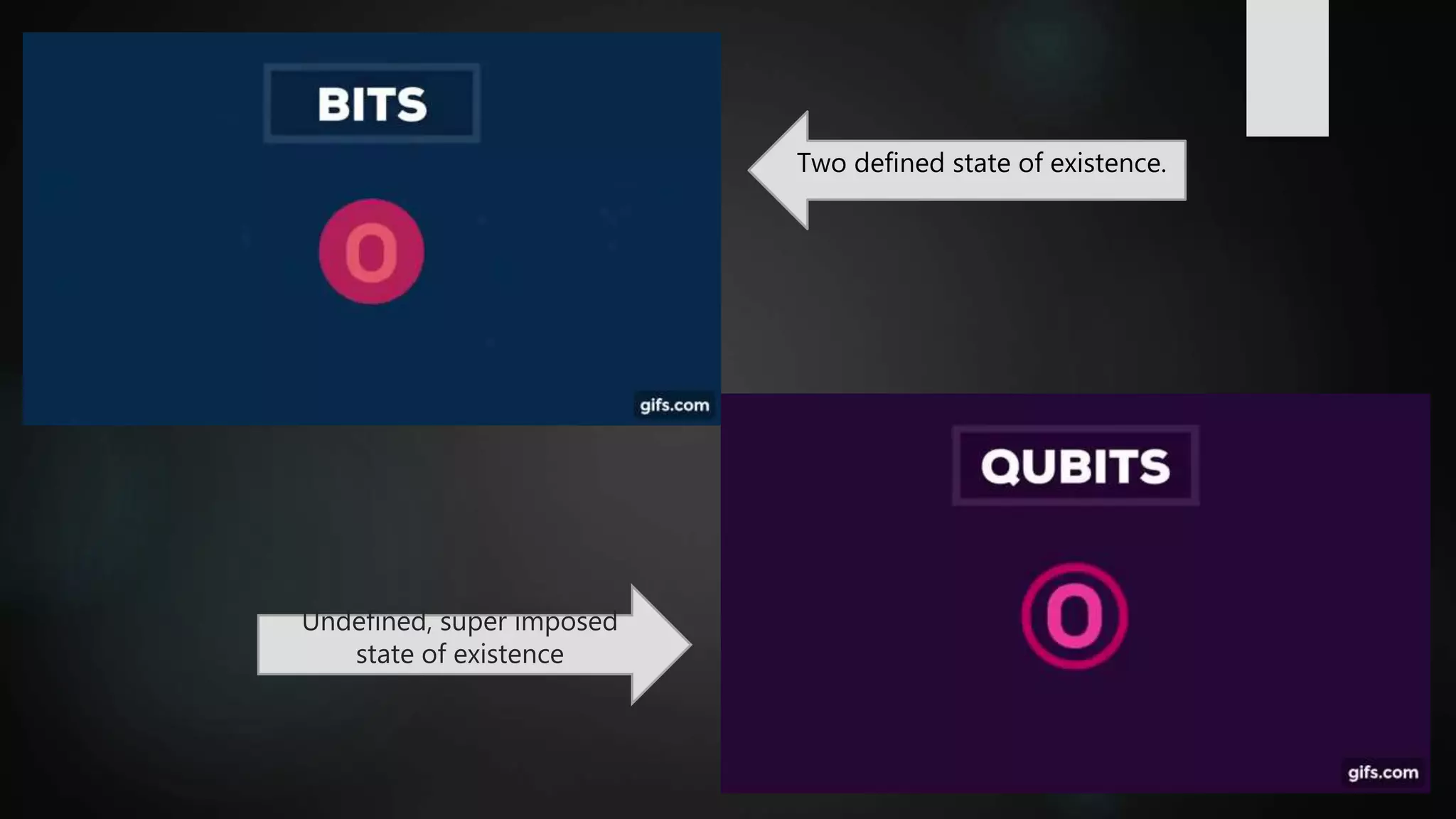
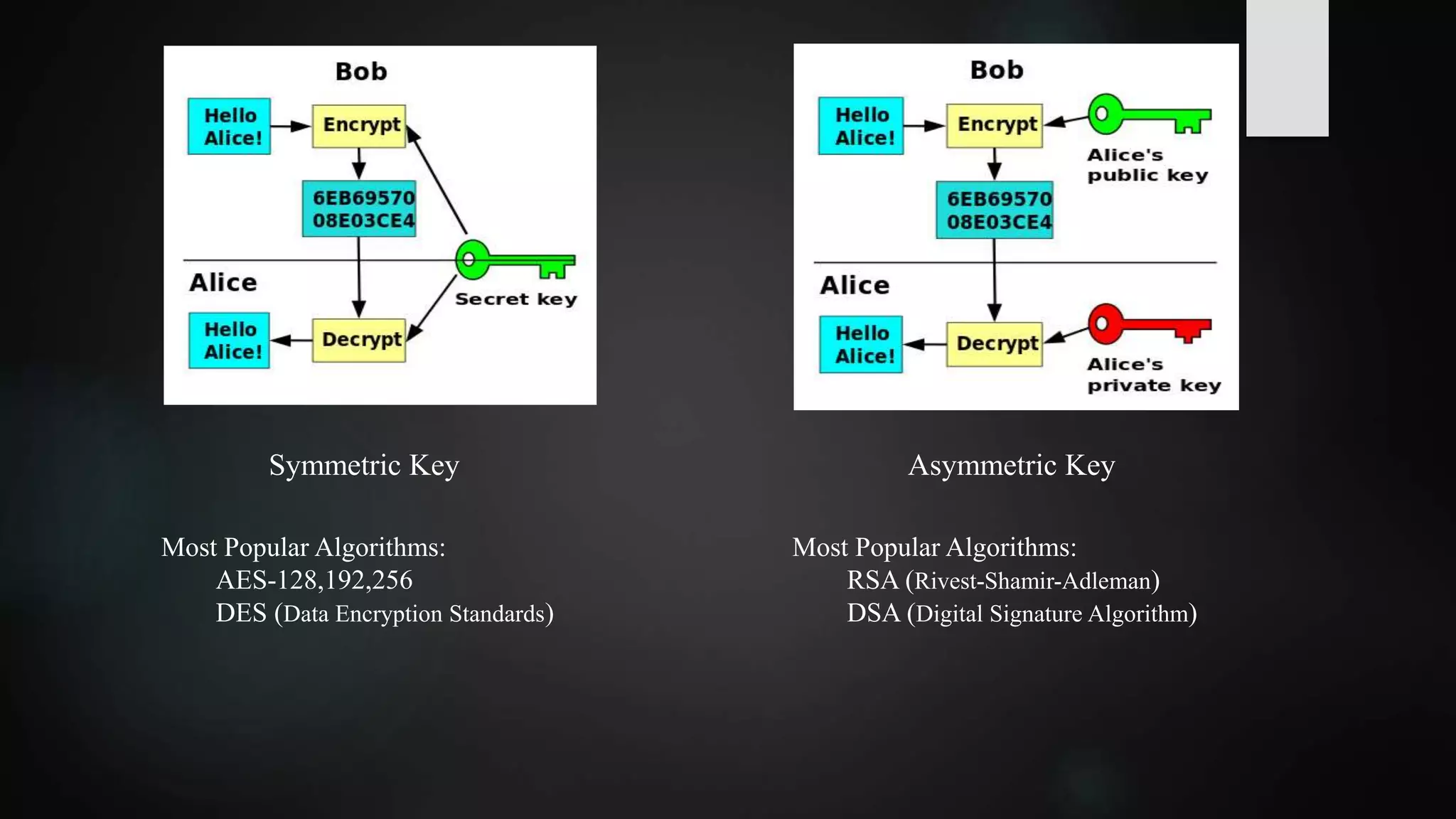
This document summarizes research on securing Internet of Things (IoT) communication in a quantum world. Currently, IoT relies on cryptographic algorithms like AES and RSA, but these may be broken by quantum computers. The document reviews symmetric key and asymmetric key cryptography. It proposes using hash-based and code-based cryptosystems, like SPHINCS and McEliece, which are quantum-resistant. Doubling the key size of AES to 256 bits could also secure it against quantum attacks. The development of practical quantum computers may take 5-10 more years, so it is important to adopt quantum-resistant algorithms now to protect data in the future.









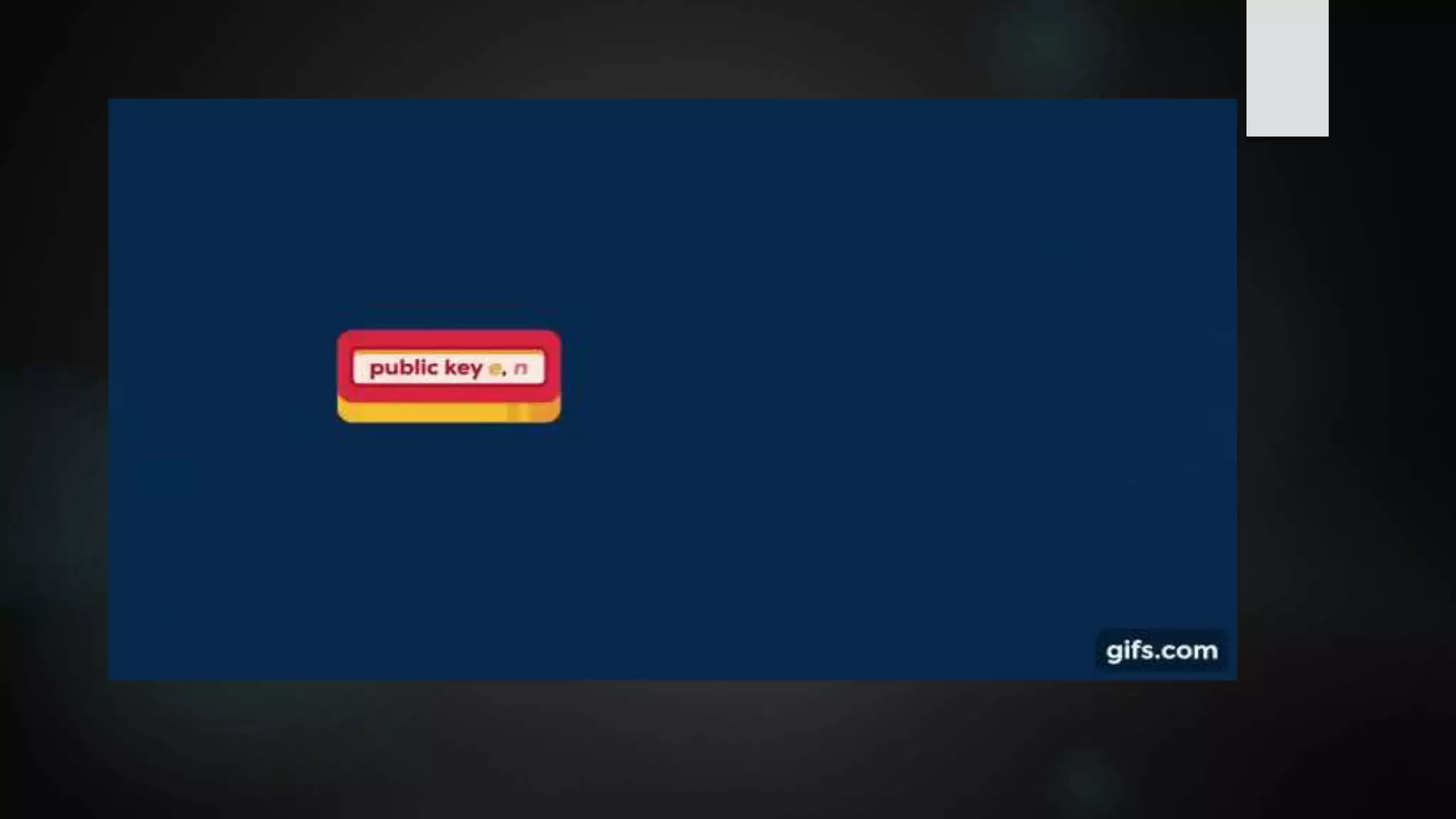
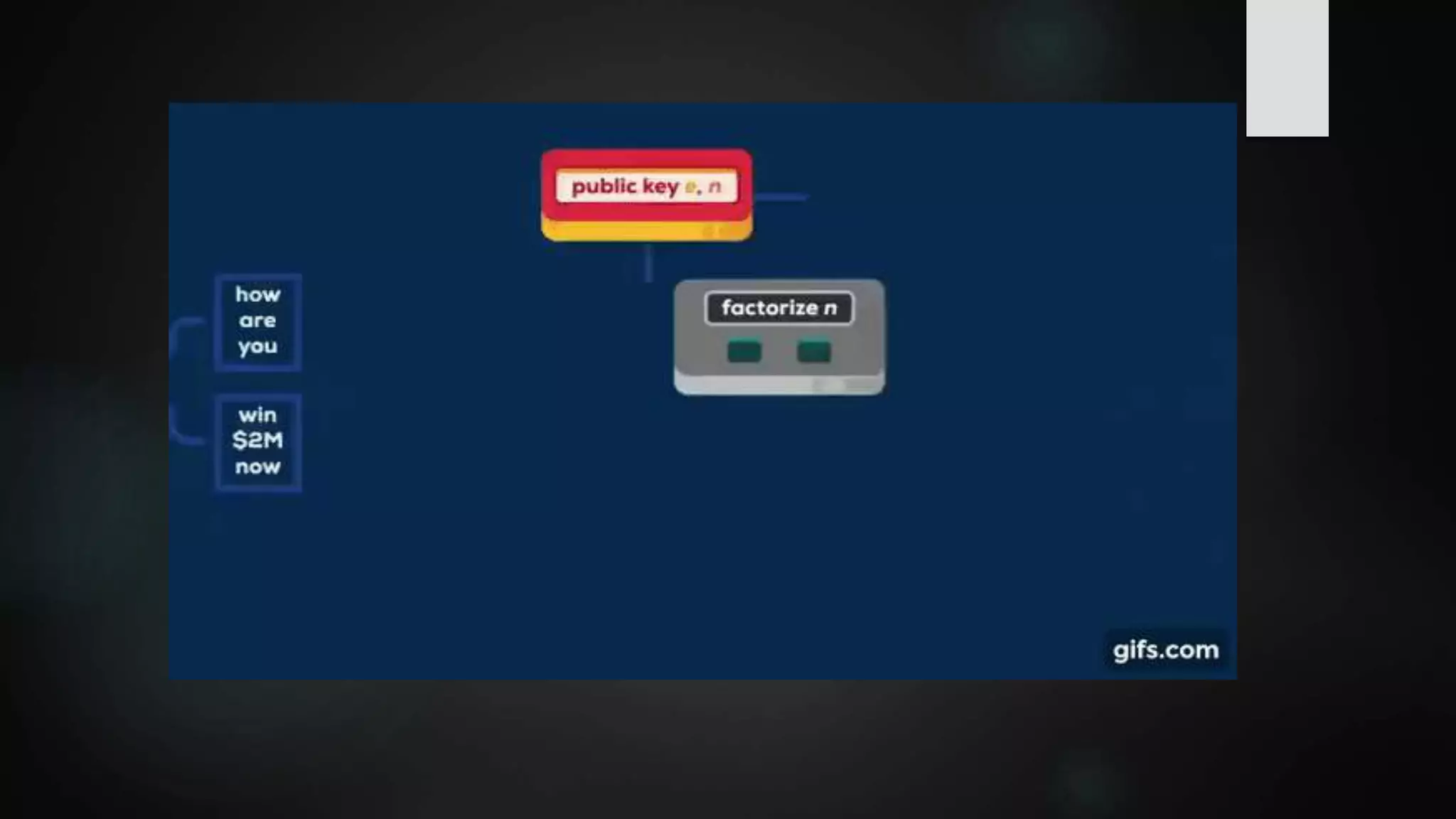
![Factoring A Product Of Two Large Primes
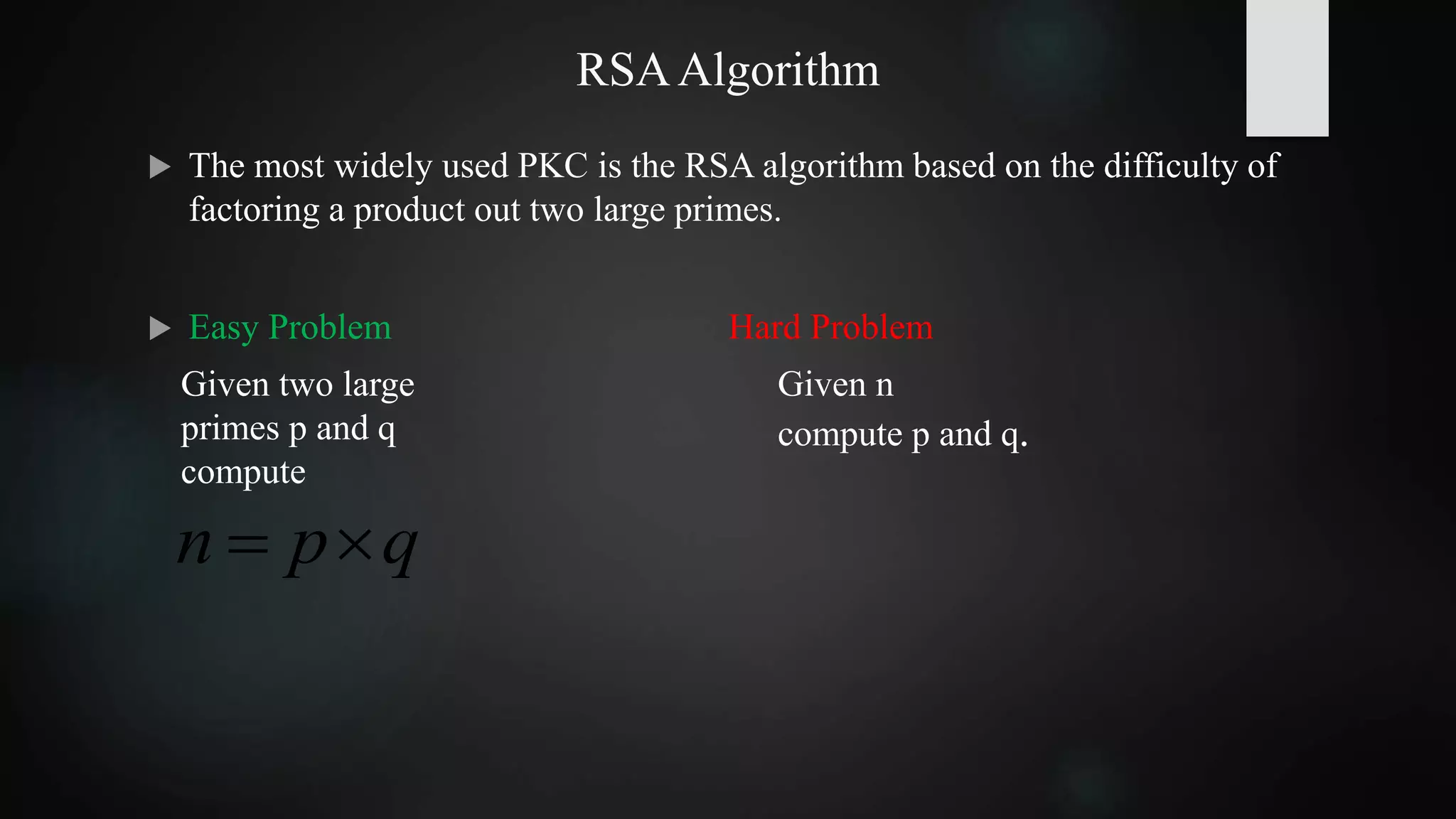
The best known conventional algorithm requires the solution time proportional
to:
Shor’s algorithm easily solves the large T(n) problem on a Quantum computer,
hence RSA cannot be safe in a Quantum world.
])ln(ln)(lnexp[)( 3/23/1
nncnT
For p & q 65 digits long T(n) is approximately
one month using cluster of workstations.
For p&q 200 digits long T(n) is astronomical.](https://image.slidesharecdn.com/securingtheiotinthequantumworld-170610091657/75/Technical-Seminar-on-Securing-the-IoT-in-the-Quantum-World-17-2048.jpg)