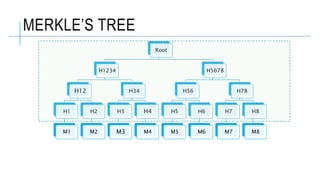
The document discusses quantum cryptography, outlining its importance through topics like quantum key distribution (QKD), asymmetric and symmetric key cryptography, and the threat posed by quantum computing. It details concepts like random number generation, encryption and decryption processes, along with various algorithms, including Shor's algorithm, which poses a challenge to current cryptographic methods. The document also highlights the evolution towards post-quantum cryptography to safeguard against emerging quantum threats.




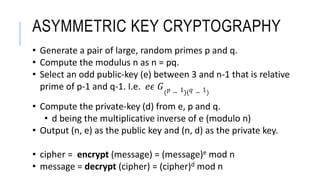
![ASYMMETRIC KEY CRYPTOGRAPHY – A
SIMPLE EXAMPLE
Consider p = 5 and q = 11 n = 55
• p – 1 = 4 and q – 1 = 10
• Choose public-key e = 7 ( relative prime of 4 and 10)
• Choose private-key (d) such that 𝑑 × 𝑒 ≡ 1 𝑚𝑜𝑑[(𝑝 − 1 ×
𝑞 − 1 ]
• i.e. 7𝑑 ≡ 1𝑚𝑜𝑑40 d is 23.
• Output (55, 7) as the public key and (55, 23) as the private key.
Suppose message = 8
• cipher ≡ (message)e mod n ≡ 87 mod 55 = 2
• message ≡ (cipher)d mod n ≡ 223 mod 55 = 8](https://image.slidesharecdn.com/quantumcryptography-tech-talk-v3-190413163042/85/Quantum-cryptography-by-Girisha-Shankar-Sr-Manager-Cisco-6-320.jpg)