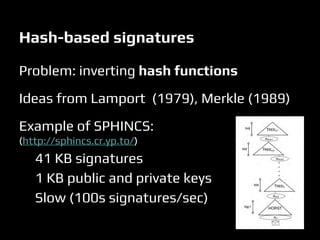
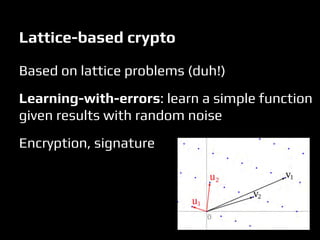
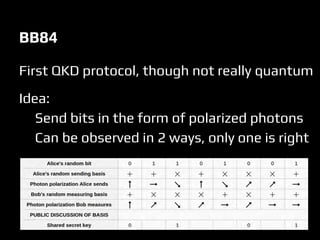
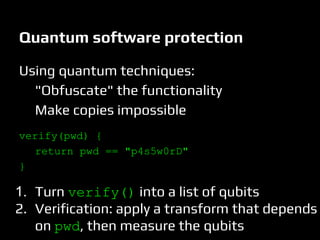
This document discusses quantum computers and their implications for computer security. It begins with introductions to quantum mechanics concepts and how quantum computers work. It then explains that quantum computers could break many current encryption standards by efficiently solving problems like integer factorization that are hard for classical computers. Alternative "post-quantum" encryption methods are discussed. The document also covers quantum key distribution, proposals for quantum copy protection, and potential applications of quantum machines for tasks like machine learning. While quantum computers may revolutionize computing, many challenges remain around building them and developing quantum algorithms.


















![Xe
mod N for e in [1, 2, 3, …] and some X
will repeat with a period dividing (p-1)(q-1)
A period gives information on p and q!
Shor’s algorithm:
1. Prepare qubits to encode X,X2
,X3
,X4
, ... simultaneously
2. Find the period using the Quantum Fourier Transform
3. Exploits the period to recover p and q
Shor’s idea to factor N=pq](https://image.slidesharecdn.com/defcon-23-phillip-aumasson-quantum-computers-vs-computers-se-201030141012/85/DEF-CON-23-Phillip-Aumasson-quantum-computers-vs-computers-security-24-320.jpg)