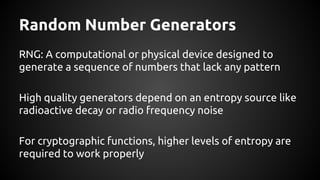
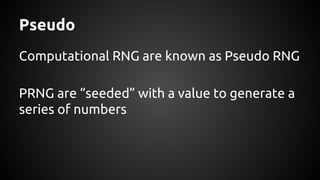
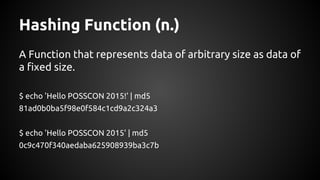
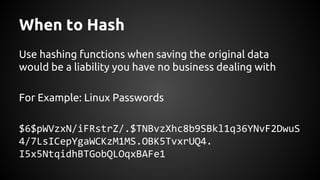
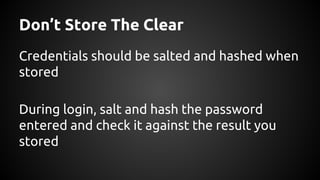
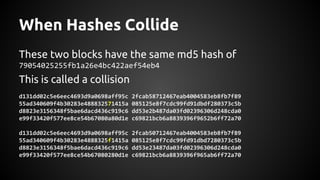
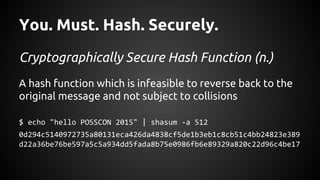
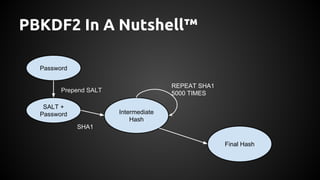
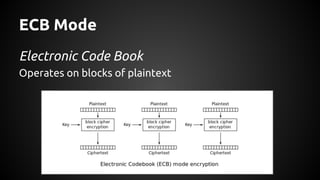
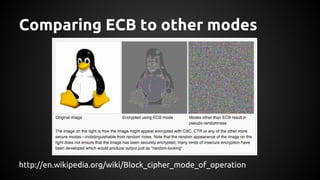
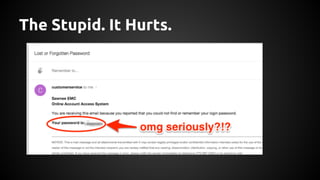
The document discusses the proper use of cryptography in applications, focusing on key concepts such as random number generation, salting, hashing, key derivation, and symmetric encryption. It highlights common mistakes made in the implementation of cryptographic techniques, emphasizing the importance of securing passwords and the dangers of weak configurations. The speaker, Andy Watson from Ionic Security, aims to educate developers to avoid these pitfalls and use established methodologies to protect sensitive data.